声明:原文版权归属Intel®,这里仅作学习使用
来源:Intel® 64 and IA-32 Architectures Software Developer's Manual Volume 3A: System Programming Guide, Part 1
Chapter 3.2 USING SEGMENTS 使用段
The segmentation mechanism supported by the IA-32 architecture can be used to implement a wide variety of system designs. These designs range from flat models that make only minimal use of segmentation to protect programs to multi-segmented models that employ segmentation to create a robust operating environment in which multiple programs and tasks can be executed reliably.
The following sections give several examples of how segmentation can be employed in a system to improve memory management performance and reliability.
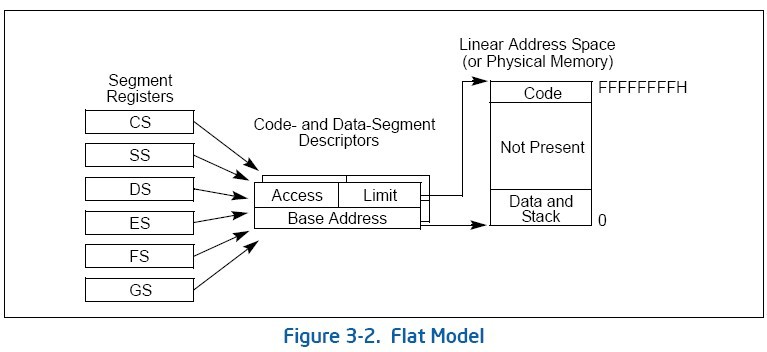
3.2.1 Basic Flat Model 基本平坦模型
The simplest memory model for a system is the basic "flat model,"(最基本的是平坦模型) in which the operating system and application programs have access to a continuous, unsegmented address space(操作系统和应用程序可以访问连续的、未分段的地址空间(这样很不安全)). To the greatest extent possible, this basic flat model hides the segmentation mechanism of the architecture from both the system designer and the application programmer.(基本平坦模型对系统设计者和应用程序开发者都隐藏了体系结构中的分段的机制)
To implement a basic flat memory model with the IA-32 architecture, at least two segment descriptors must be created, one for referencing a code segment and one for referencing a data segment (see Figure 3-2)(平坦模型至少要创建两个段描述符,一个代码段,一个数据段). Both of these segments, however, are mapped to the entire linear address space: that is, both segment descriptors have the same base address value of 0 and the same segment limit of 4 GBytes.(两段均映射到0-4G整个线性地址空间) By setting the segment limit to 4 GBytes, the segmentation mechanism is kept from generating exceptions for out of limit memory references, even if no physical memory resides at a particular address. ROM (EPROM) is generally located at the top of the physical address space, because the processor begins execution at FFFF_FFF0H(固化的ROM通常在高的物理地址). RAM (DRAM) is placed at the bottom of the address space because the initial base address for the DS data segment after reset initialization is 0(内存通常从低地址开始启动).
3.2.2 Protected Flat Model 保护平坦模型
The protected flat model is similar to the basic flat model, except the segment limits are set to include only the range of addresses for which physical memory actually exists (see Figure 3-3)(保护平坦模型类似于基本平坦模型,只是段界限设置为物理内存实际存在的范围). A general-protection exception (#GP) is then generated on any attempt to access nonexistent memory(访问不存在的内存会产生通用保护异常). This model provides a minimum level of hardware protection against some kinds of program bugs.(对程序中的bug提供最少等级的硬件保护)
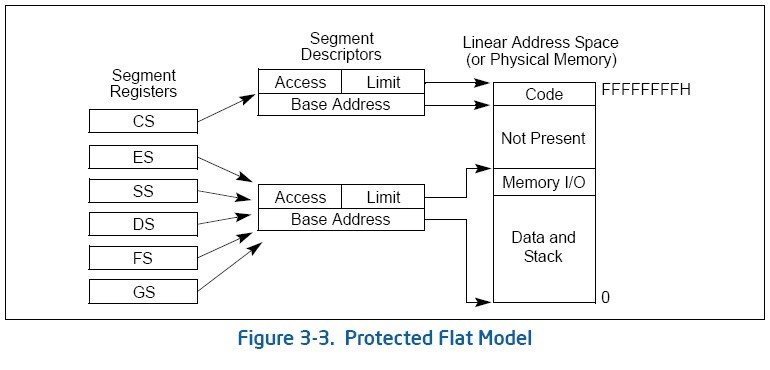
More complexity can be added to this protected flat model to provide more protection. (可以给该模型增加复杂度,以提供更多的保护)For example, for the paging mechanism to provide isolation between user and supervisor code and data, four segments need to be defined: code and data segments at privilege level 3 for the user, and code and data segments at privilege level 0 for the supervisor(给用户特权级3的代码段和数据段,给管理员特权级0的代码段和数据段). Usually these segments all overlay each other and start at address 0 in the linear address space.(通常,这些段在线性地址空间是相互重叠的,并且都从0地址开始) This flat segmentation model along with a simple paging structure can protect the operating system from applications, and by adding a separate paging structure for each task or process, it can also protect applications from each other. Similar designs are used by several popular multitasking operating systems.
3.2.3 Multi-Segment Model 多段模型
A multi-segment model (such as the one shown in Figure 3-4) uses the full capabilities of the segmentation mechanism to provided hardware enforced protection of code, data structures, and programs and tasks. Here, each program (or task) is given its own table of segment descriptors and its own segments(每个程序,或任务,都有自己的段描述符和段). The segments can be completely private to their assigned programs or shared among programs.(段可以是私有的,也可以是程序间共享的) Access to all segments and to the execution environments of individual programs running on the system is controlled by hardware.(对于在系统中运行的单个程序对段和执行环境的访问控制由硬件完成)
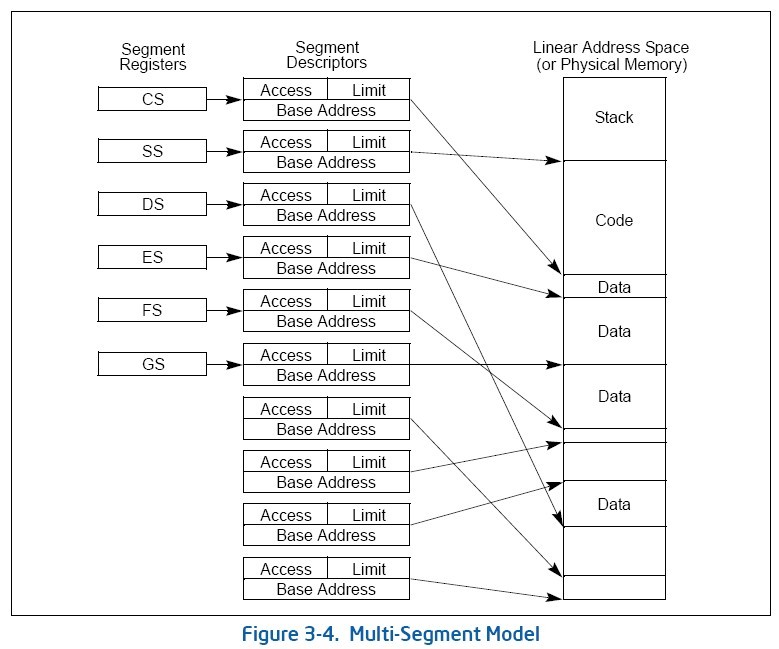
Access checks can be used to protect not only against referencing an address outside the limit of a segment, but also against performing disallowed operations in certain segments.(不仅可以检查对段界限外的地址的访问,还可以检查段中不允许的某些操作) For example, since code segments are designated as read-only segments, hardware can be used to prevent writes into code segments. (如,代码段是只读的段,那么硬件可以阻止对于代码段的写操作)The access rights information created for segments can also be used to set up protection rings or levels. Protection levels can be used to protect operating-system procedures from unauthorized access by application programs.
3.2.4 Segmentation in IA-32e Mode
In IA-32e mode of Intel 64 architecture, the effects of segmentation depend on whether the processor is running in compatibility mode or 64-bit mode. In compatibility mode, segmentation functions just as it does using legacy 16-bit or 32-bit protected mode semantics.
In 64-bit mode, segmentation is generally (but not completely) disabled, creating a flat 64-bit linear-address space. The processor treats the segment base of CS, DS, ES, SS as zero, creating a linear address that is equal to the effective address. The FS and GS segments are exceptions. These segment registers (which hold the segment base) can be used as an additional base registers in linear address calculations. They facilitate addressing local data and certain operating system data structures.
Note that the processor does not perform segment limit checks at runtime in 64-bit mode.
3.2.5 Paging and Segmentation 分页和分段
Paging can be used with any of the segmentation models described in Figures 3-2, 3-3, and 3-4. (分页可以使用在上面提到的任何一个分段模型中)The processor's paging mechanism divides the linear address space (into which segments are mapped) into pages (as shown in Figure 3-1)(处理器的分页机制将线性地址空间切分为页). These linear-address-space pages are then mapped to pages in the physical address space.(线性地址空间中的页再映射到物理地址空间的页) The paging mechanism offers several page-level protection facilities that can be used with or instead of the segment-protection facilities. For example, it lets read-write protection be enforced on a page-by-page basis. The paging mechanism also provides two-level user-supervisor protection that can also be specified on a page-by-page basis.(分页机制可以允许逐页的读写保护,以及两层的用户-管理员保护)





















 5202
5202











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








