声明:原文版权归属Intel®,这里仅作学习使用
来源:Intel® 64 and IA-32 Architectures Software Developer's Manual Volume 3A: System Programming Guide, Part 1
Chapter 1 ABOUT THIS MANUAL
1.1-1.2 省略
1.3 NOTATIONAL CONVENTIONS 符号惯例
This manual uses specific notation for data-structure formats, for symbolic representation of instructions, and for hexadecimal and binary numbers. A review of this notation makes the manual easier to read.
1.3.1 Bit and Byte Order 位和字节序
In illustrations of data structures in memory, smaller addresses appear toward the bottom of the figure; addresses increase toward the top. Bit positions are numbered from right to left. The numerical value of a set bit is equal to two raised to the power of the bit position. Intel 64 and IA-32 processors are “little endian” (小端在前)machines; this means the bytes of a word are numbered starting from the least significant byte(最低有效字节).
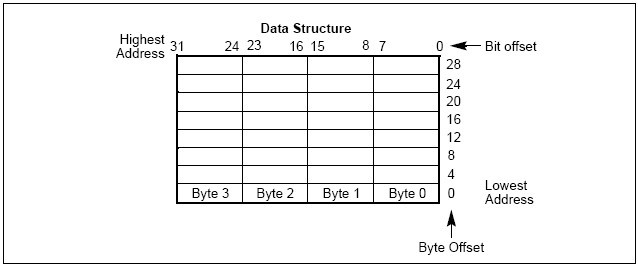
Figure 1-1 illustrates these conventions.
1.3.2 Reserved Bits and Software Compatibility 预留位与软件兼容性
In many register and memory layout descriptions, certain bits are marked as reserved. When bits are marked as reserved, it is essential for compatibility with future processors that software treat these bits as having a future, though unknown, effect. The behavior of reserved bits should be regarded as not only undefined, but unpredictable. Software should follow these guidelines in dealing with reserved bits:
- Do not depend on the states of any reserved bits when testing the values of registers which contain such bits. Mask out the reserved bits before testing.
- Do not depend on the states of any reserved bits when storing to memory or to a register.
- Do not depend on the ability to retain information written into any reserved bits.
- When loading a register, always load the reserved bits with the values indicated in the documentation, if any, or reload them with values previously read from the same register.
NOTE
Avoid any software dependence upon the state of reserved bits in Intel 64 and IA-32 registers. Depending upon the values of reserved register bits will make software dependent upon the unspecified manner in which the processor handles these bits. Programs that depend upon reserved values risk incompatibility with future processors.
1.3.3 Instruction Operands 指令操作数
When instructions are represented symbolically, a subset of assembly language is used. In this subset, an instruction has the following format:
label: mnemonic argument1, argument2, argument3 标记:助记符 参数1,参数2,参数3
where:
- A label (标记)is an identifier which is followed by a colon.
- A mnemonic (助记符) is a reserved name for a class of instruction opcodes which have the same function.
- The operands(操作数) argument1, argument2, and argument3 are optional. There may be from zero to three operands, depending on the opcode(操作码). When present, they take the form of either literals or identifiers for data items. Operand identifiers are either reserved names of registers or are assumed to be assigned to data items declared in another part of the program (which may not be shown in the example).
When two operands are present in an arithmetic or logical instruction, the right operand is the source and the left operand is the destination.
For example:
LOADREG: MOV EAX, SUBTOTAL
In this example LOADREG is a label, MOV is the mnemonic identifier of an opcode, EAX is the destination operand, and SUBTOTAL is the source operand. Some assembly languages put the source and destination in reverse order.
1.3.4 Hexadecimal and Binary Numbers 十六进制和二进制数
Base 16 (hexadecimal) numbers are represented by a string of hexadecimal digits followed by the character H (for example, F82EH). A hexadecimal digit is a character from the following set: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, and F.
Base 2 (binary) numbers are represented by a string of 1s and 0s, sometimes followed by the character B (for example, 1010B). The “B” designation is only used in situations where confusion as to the type of number might arise.
1.3.5 Segmented Addressing 段式寻址
The processor uses byte addressing (字节寻址). This means memory is organized and accessed as a sequence of bytes(内存是按照字节的序列组织和访问的). Whether one or more bytes are being accessed, a byte address is used to locate the byte or bytes memory(无论访问一个或者多个字节,需要一个字节地址来定位). The range of memory that can be addressed is called an address space (可寻址到的内存范围叫做地址空间).
The processor also supports segmented addressing(段式寻址). This is a form of addressing where a program may have many independent address spaces, called segments . For example, a program can keep its code (instructions) and stack in separate segments. Code addresses would always refer to the code space, and stack addresses would always refer to the stack space. The following notation is used to specify a byte address within a segment:
Segment-register:Byte-address 字节寻址
For example, the following segment address identifies the byte at address FF79H in the segment pointed by the DS register:
DS:FF79H
The following segment address identifies an instruction address in the code segment. The CS register points to the code segment and the EIP register contains the address of the instruction.
CS:EIP
1.3.6 Syntax for CPUID, CR, and MSR Values CPUID, CR和MSR值的语义
Obtain feature flags, status, and system information by using the CPUID instruction, by checking control register bits, and by reading model-specific registers. We are moving toward a single syntax to represent this type of information. See Figure 1-2.
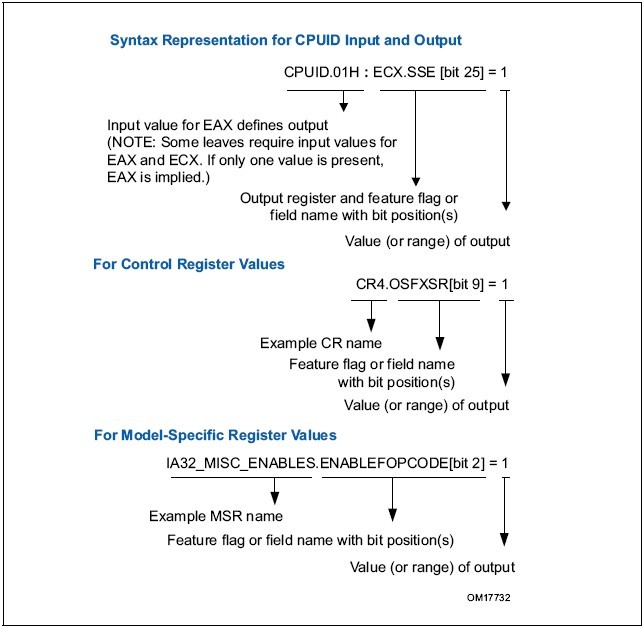
Figure 1-2. Syntax for CPUID, CR, and MSR Data Presentation
1.3.7 Exceptions 异常
An exception is an event that typically occurs when an instruction causes an error. (异常是一种事件,通常发生在指令产生错误时。)For example, an attempt to divide by zero(除零) generates an exception. However, some exceptions, such as breakpoints(断点), occur under other conditions. Some types of exceptions may provide error codes(错误码). An error code reports additional information about the error. An example of the notation used to show an exception and error code is shown below:
#PF(fault code)
This example refers to a page-fault exception under conditions where an error code naming a type of fault is reported. Under some conditions, exceptions which produce error codes may not be able to report an accurate code. In this case, the error code is zero, as shown below for a general-protection exception:
#GP(0)
1.4 RELATED LITERATURE 相关文献
Literature related to Intel 64 and IA-32 processors is listed on-line at:
http://developer.intel.com/products/processor/index.htm
Some of the documents listed at this web site can be viewed on-line; others can be ordered. The literature available is listed by Intel processor and then by the following literature types: applications notes, data sheets, manuals, papers, and specification updates.
See also:
•The data sheet for a particular Intel 64 or IA-32 processor
•The specification update for a particular Intel 64 or IA-32 processor
•Intel® C++ Compiler documentation and online help
http://www.intel.com/cd/software/products/asmo-na/eng/index.htm
•Intel® Fortran Compiler documentation and online help
http://www.intel.com/cd/software/products/asmo-na/eng/index.htm
•Intel® VTune™ Performance Analyzer documentation and online help
http://www.intel.com/cd/software/products/asmo-na/eng/index.htm
•Intel® 64 and IA-32 Architectures Software Developer’s Manual (in five volumes)
http://developer.intel.com/products/processor/manuals/index.htm
•Intel® 64 and IA-32 Architectures Optimization Reference Manual
http://developer.intel.com/products/processor/manuals/index.htm
•Intel® Processor Identification with the CPUID Instruction, AP-485
http://www.intel.com/support/processors/sb/cs-009861.htm
•TLBs, Paging-Structure Caches, and Their Invalidation, http://developer.intel.com/products/processor/manuals/index.htm
•Intel® 64 Architecture Memory Ordering White Paper, http://developer.intel.com/products/processor/manuals/index.htm
•Intel® Trusted Execution Technology Measured Launched Environment Programming Guide, http://www.intel.com/technology/security/index.htm
•Intel® SSE4 Programming Reference, http://developer.intel.com/products/processor/manuals/index.htm
•Developing Multi-threaded Applications: A Platform Consistent Approach
http://cache-www.intel.com/cd/00/00/05/15/51534_developing_multithreaded_applications.pdf
•Using Spin-Loops on Intel Pentium 4 Processor and Intel Xeon Processor MP
http://www3.intel.com/cd/ids/developer/asmo-na/eng/dc/threading/knowledgebase/19083.htm
More relevant links are:
•Software network link:
http://softwarecommunity.intel.com/isn/home/
•Developer centers:
http://www.intel.com/cd/ids/developer/asmo-na/eng/dc/index.htm
•Processor support general link:
http://www.intel.com/support/processors/
•Software products and packages:
http://www.intel.com/cd/software/products/asmo-na/eng/index.htm
•Intel 64 and IA-32 processor manuals (printed or PDF downloads):
http://developer.intel.com/products/processor/manuals/index.htm
•Intel® Multi-Core Technology:
http://developer.intel.com/multi-core/index.htm
•Hyper-Threading Technology (HT Technology):
http://developer.intel.com/technology/hyperthread/





















 5165
5165











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








