If you are a computer network or security enthusiast, you’ve probably heard of Wireshark. Wireshark is the world’s most popular network protocol analyzer. It lets you dive into captured traffic and analyze what is going on within a network. You can use it to diagnose network issues and find network vulnerabilities.
如果您是计算机网络或安全爱好者,则可能听说过Wireshark 。 Wireshark是世界上最受欢迎的网络协议分析器。 它使您能够深入了解捕获的流量并分析网络中发生的情况。 您可以使用它来诊断网络问题并查找网络漏洞。
In this article, we will go through some basics of capturing traffic with Wireshark. Since we will go through some examples, feel free to use a PCAP file to follow along! Head to the Wireshark wiki to find some sample capture files.
在本文中,我们将介绍一些使用Wireshark捕获流量的基础知识。 由于我们将通过一些示例,请随时使用PCAP文件! 前往Wireshark Wiki查找一些示例捕获文件。
使用PCAP文件 (Working With PCAP Files)
After you open up Wireshark, it will start capturing traffic on multiple network interfaces. You can double-click on an interface to see traffic details:
打开Wireshark后,它将开始捕获多个网络接口上的流量。 您可以双击某个接口以查看流量详细信息:
You should see packets listed in the Wireshark window like this:
您应该在Wireshark窗口中看到如下所示的数据包:
You can save the captured packets by first clicking on the red square button on the top toolbar:
您可以通过首先单击顶部工具栏上的红色正方形按钮来保存捕获的数据包:
This will tell Wireshark to stop capturing packets. Then, go to “File > Save” to save the PCAP file. PCAP stands for “Packet CAPture” and is the file extension used for Wireshark capture files. You might also see the extension “PCAPNG,” which stands for “PCAP Next Generation” and is a new version of the PCAP file format.
这将告诉Wireshark停止捕获数据包。 然后,转到“文件>保存”以保存PCAP文件。 PCAP代表“数据包捕获”,是Wireshark捕获文件使用的文件扩展名。 您可能还会看到扩展名“ PCAPNG”,它代表“ PCAP Next Generation”,是PCAP文件格式的新版本。
Later when you want to revisit the traffic capture, you can go to “File > Open” to import a saved PCAP file.
稍后,当您想重新访问流量捕获时,可以转到“文件>打开”以导入保存的PCAP文件。
远端撷取 (Remote Capture)
What if you wanted to capture and analyze traffic on a remote server? Wireshark is usually used to analyze traffic on your local network, so you would need to use a tool like tcpdump.
如果要捕获和分析远程服务器上的流量怎么办? Wireshark通常用于分析本地网络上的流量,因此您需要使用tcpdump之类的工具。
First, SSH into the remote machine with an account with root access:
首先,使用具有root用户访问权限的帐户SSH到远程计算机:
ssh remoteuser@remotehostNext, use tcpdump to capture the traffic on the remote network and save it into a PCAP file:
接下来,使用tcpdump捕获远程网络上的流量并将其保存到PCAP文件中:
sudo tcpdump -i eth0 -w tcpdump.pcapFinally, copy the capture file to your computer by using the scp command:
最后,使用scp命令将捕获文件复制到您的计算机:
scp remoteuser@remotehost:tcpdump.pcap /some/local/directoryYou can now open up the remote capture file by using Wireshark on your computer.
现在,您可以使用计算机上的Wireshark打开远程捕获文件。
Alternatively, you can use Wireshark’s remote capture tool sshdump. This command is functionally equivalent to the commands above:
另外,您可以使用Wireshark的远程捕获工具sshdump。 该命令在功能上等同于上述命令:
sshdump --extcap-interface=sshdump --capture--remote-host remotehost --remote-username remoteuser--fifo=/some/local/directory/tcpdump.pcapYou can also use sshdump directly in Wireshark’s GUI. Access sshdump by scrolling down the interfaces list on the startup screen and double-click on “SSH remote capture: sshdump”:
您也可以直接在Wireshark的GUI中使用sshdump。 通过在启动屏幕上向下滚动接口列表并双击“ SSH远程捕获:sshdump”来访问sshdump:
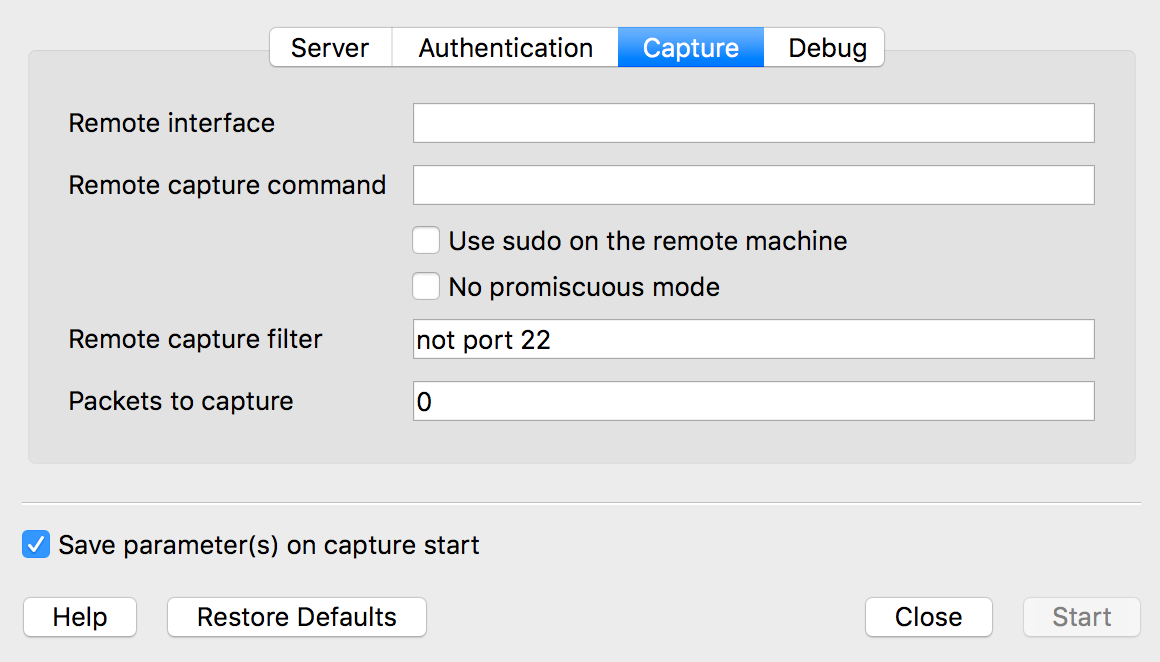
From this dialog, you can specify the remote server, port, interface, username, and password:
在此对话框中,您可以指定远程服务器,端口,接口,用户名和密码:
You can also specify capture filters and capture commands. Be sure to check the “Use sudo on remote machine” option!
您还可以指定捕获过滤器和捕获命令。 确保选中“在远程计算机上使用sudo”选项!
捕获过滤器 (Capture Filters)
You can use Wireshark’s capture filters to reduce the size of your capture files. Capture filters enable you to leave out packets that you are not interested in during a capture. In Wireshark’s startup window, you can see the capture filter above the interfaces list:
您可以使用Wireshark的捕获过滤器来减小捕获文件的大小。 捕获过滤器使您可以忽略捕获期间不感兴趣的数据包。 在Wireshark的启动窗口中,您可以在接口列表上方看到捕获过滤器:

You can filter packets based on criteria like IP addresses, port numbers, and protocol. For example, you can use a “host” filter to focus on traffic to and from a target host:
您可以根据IP地址,端口号和协议等条件过滤数据包。 例如,您可以使用“主机”过滤器来关注往返于目标主机的流量:
host 74.125.5.4 (Captures all traffic to and from host.)
dst host 74.125.5.4 (Captures all traffic to host.)
src host 74.125.5.4 (Captures all traffic from host.)You can also filter according to source and destination ports:
您还可以根据源端口和目标端口进行过滤:
port 80 (Captures all traffic to and from port.)
dst port 80 (Captures all traffic to port.)
src port 80 (Captures all traffic from port.)Finally, you can use filters to exclude packets as well:
最后,您还可以使用过滤器排除数据包:
not port 80 (Captures all packets that do not use port.)You can find more useful capture filters on the wiki.
您可以在Wiki上找到更多有用的捕获过滤器 。
显示过滤器 (Display Filters)
On the other hand, you can use display filters to leave out packets you do not want to see in the Wireshark window. Display filters do not affect the PCAP file but allow you to see only certain packets during your analysis. You can see the display filter in Wireshark’s window above the packets list:
另一方面,您可以使用显示过滤器来丢弃不想在Wireshark窗口中看到的数据包。 显示过滤器不会影响PCAP文件,但允许您在分析期间仅看到某些数据包。 您可以在Wireshark的数据包列表上方的窗口中看到显示过滤器:
For example, you can tell Wireshark to display or exclude packets with certain source and destination IPs:
例如,您可以告诉Wireshark显示或排除具有某些源IP和目标IP的数据包:
ip.src==74.125.5.4 and ip.dst==192.168.0.1
ip.src!=74.125.5.4You can also filter based on protocol:
您还可以根据协议进行过滤:
udp or icmpOr filter packets based on content by using the contains filter. This filter will display packets that contain the three-byte sequence 0x81, 0x60, 0x03 anywhere in the UDP header or payload:
或使用contains过滤器根据内容过滤数据包。 此过滤器将在UDP标头或有效负载中的任何位置显示包含三字节序列0x81、0x60、0x03的数据包:
<host or protocol> contains <expression>
udp contains 81:60:03Finally, you can combine filters using boolean expressions like and or or:
最后,您可以使用布尔表达式(例如and或or来组合过滤器:
tcp.port==80 or udpYou can find more useful display filters on the wiki.
您可以在Wiki上找到更多有用的显示过滤器 。
结论 (Conclusion)
Thanks for reading! This article only introduces a small fraction of what you can do with Wireshark. It is a versatile tool that is capable of performing many different types of analysis.
谢谢阅读! 本文仅介绍您可以使用Wireshark做的一小部分。 它是一种多功能工具,能够执行许多不同类型的分析。
If you are interested in learning more about Wireshark, visit its documentation below:
如果您想了解有关Wireshark的更多信息,请访问下面的文档:
翻译自: https://medium.com/better-programming/intro-to-wireshark-2abe7fb24f53





















 103
103

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








