发现问题
Security researcher Pedro Ribeiro revealed four unpatched vulnerabilities in IBM Data Risk Manager on April 21st. On the surface, these individual vulnerabilities, while carrying some risk, did not appear to be critical. However, as Mr. Riberio demonstrates, when skillfully linked together they delivered privileged host access.
安全研究员Pedro Ribeiro揭示了IBM Data Risk Manager中的 四个未修补的漏洞 在4月21日。 从表面上看,这些个体漏洞虽然带来一定风险,但似乎并不重要。 但是,正如Riberio先生所展示的那样,当他们巧妙地链接在一起时,它们便提供了特权主机访问权限。
This blog post will deconstruct the zero-days identified and their disclosure, how they can be linked together with a detailed example of the exploit, how the vulnerabilities could have been identified and what lessons can be learned.
这篇博客文章将解构识别的零日漏洞及其披露,如何将其与漏洞利用的详细示例链接在一起,如何识别漏洞以及可以学到什么教训。
披露故事 (The Disclosure Story)
Pedro Ribeiro made this public in the tweet as indicated below.
佩德罗·里贝罗(Pedro Ribeiro)在推文中将其公开,如下所示。
Update (04/24): Pedro acknowledged this narrative
更新(04/24) :Pedro承认了这一叙述
In reaction to this disclosure the team IBM initially rebuffed his claim with the following response
针对此披露,IBM团队最初拒绝了他的索赔,并做出以下回应
we have assessed this report and closed as being out of scope for our vulnerability disclosure program since this product is only for “enhanced” support paid for by our customers. This is outlined in our policy https://hackerone.com/ibm. To be eligible to participate in this program, you must not be under contract to perform security testing for IBM Corporation, or an IBM subsidiary, or IBM client within 6 months prior to submitting a report.
由于该产品仅用于由客户付费的“增强型”支持,因此我们评估了此报告,并认为它不在我们的漏洞披露程序的范围之内 。 我们的政策https://hackerone.com/ibm中对此进行了概述。 要有资格参加此计划,您必须没有合同才能在提交报告之前的6个月内对IBM Corporation,IBM子公司或IBM客户执行安全性测试。
This initial reaction backfired leading to articles published by Tech Radar, The Hacker News, The Register, ZDNet and Bleeping Computer and many others.
这种最初的React适得其反,导致Tech Radar , The Hacker News , The Register , ZDNet和Bleeping Computer等许多人发表了文章。
As a consequence of this backlash, IBM put efforts to patched two of the four vulnerabilities on April 21st and are currently still working to analyze and identify additional fixes actions as needed. The two that have been patched are:
由于这种抵制,IBM于4月21日努力修补了四个漏洞中的两个 ,并且目前仍在努力分析和确定所需的其他修复措施 。 已修补的两个是:
- Command Injection Vulnerability in version 2.0.1, 2.0.2 and 2.0.3 is addressed in version 2.0.4 2.0.1、2.0.2和2.0.3版中的命令注入漏洞已在2.0.4版中解决
- Arbitrary File Download identified in version 2.0.2 and 2.0.3 is addressed in version 2.0.4 版本2.0.2和2.0.3中标识的任意文件下载在版本2.0.4中已解决
To mitigate the vulnerabilities, IBM then recommended users to upgrade with IDRM version 2.0.6.
为了减轻漏洞,IBM随后建议用户使用IDRM 2.0.6版进行升级。
发现 (Discovery)
After analyzing IBM’s IDRM Linux virtual appliance, Perdro discovered 4 vulnerabilities
在分析了IBM的IDRM Linux虚拟设备之后,Perdro 发现了 4个漏洞
- Authentication Bypass 身份验证绕过
- Command Injection 命令注入
- Insecure Default Password 不安全的默认密码
- Arbitrary File Download 任意文件下载
Pedro described these four vulnerabilities and the steps required to chain the first three eventually leading to unauthenticated remote code execution as root. The researchers also release two metasploit modules that bypass authentication, allow remote code execution and exploit arbitrary file downloads.
Pedro描述了这四个漏洞以及将前三个漏洞链接 在一起最终导致以root身份导致未经身份验证的远程代码执行的步骤。 研究人员还发布了两个metasploit模块,这些模块绕过身份验证,允许远程执行代码并利用任意文件下载。
漏洞可以链接吗? (Can vulnerabilities be chained?)
Quite often, during security audits, a low severity vulnerability are overlooked, as its impact is not immediately perceived as dangerous. What is missed in this type of scenario is what happens when vulnerabilities of varying severity are combined and could lead to a step by step escalating type of exploit. This process of identifying individual vulnerabilities and links between them is often called chaining vulnerabilities
在安全审核过程中,经常会忽略低严重性漏洞,因为它的影响不会立即被视为危险。 在这种情况下,当严重性不同的漏洞组合在一起时可能会发生什么,并且可能导致逐步利用的漏洞逐步升级。 识别单个漏洞及其之间的链接的过程通常称为链接漏洞
Researchers have proposed a variety of graph-based algorithms to generate attack trees (or graphs). Either structure represents all possible sequences of exploits, where any given exploit can take advantage of the penetration achieved by prior exploits in its chain, and the final exploit in the chain achieves the attacker’s goal.
研究人员提出了多种基于图的算法来生成攻击树(或图) 。 两种结构都代表了所有可能的利用序列,其中任何给定的利用都可以利用其链中先前利用所取得的渗透,而链中的最终利用则可以达到攻击者的目标 。
Many of these chained combinations are hard to automate and detect with traditional static code analysis engines. Some can of course be combined heuristically, but others still require sophisticated query capabilities to fully understand the potential impact.
使用传统的静态代码分析引擎很难对许多这些链接组合进行自动化和检测。 当然,有些可以启发式地组合,但是其他仍然需要复杂的查询功能才能完全了解潜在的影响。
了解漏洞链 (Understanding the Vulnerability Chain)
DISCLAIMER : First, let me be clear that I have no insider knowledge. This is my best guess at what occurred, based on publicly available information here by Pedro Ribeiro.
免责声明: 首先,请让我清楚我没有内幕知识。 根据 佩德罗·里贝罗 ( Pedro Ribeiro) 此处 的 公开信息,这是我对发生的事情的最佳猜测 。
Also, we do not have access to the source code, bytecode or the encompassing virtual appliance of IBM Data Risk Manager to recount the events described below.
此外,我们无权访问源代码,字节码或IBM Data Risk Manager包含的虚拟设备来重新叙述以下所述的事件。
步骤#1 :身份验证绕过 (Step #1: Authentication Bypass)
The researcher enumerated attack surface of an operational Data Risk Manager appliance and discovers endpoints
研究人员列举了可操作的Data Risk Manager设备的攻击面并发现了端点
Upon discovery of routes, he initiated an attack sequence by enumerating
/albatross/saml/idpSelectionwith attacker controlled vectors[sessionId, userName]发现路线后,他通过枚举
/albatross/saml/idpSelection发起了攻击序列 带有攻击者控制的向量[sessionId, userName]Upon enumeration, he received feedback with a
302 redirect responsetohttps://domain:8765/saml/idpSelection(proof point ofuserNamesuccess)进行枚举后,他收到了对
https://domain:8765/saml/idpSelection的302 redirect response反馈(userName成功的证明点)

At this point, the researcher could easily bypass authentication by a simple user lookup and got a map of users and sessionIds. It was now time to use this newly acquired information to chain the vulnerability to something else.
此时,研究人员可以通过简单的用户查找轻松地绕过身份验证,并获得用户和sessionId的映射。 现在是时候使用这些新获得的信息来将漏洞链接到其他东西。
步骤2:横向移动(移至另一条裸露的路线) (Step #2: Lateral Movement (to another exposed route))
Leveraging the attack surface, he filtered out the list of routes that accept
[userName,sessionId]as one of the attacker controlled vectors利用攻击面,他过滤了接受
[userName,sessionId]的路由列表 作为攻击者控制的媒介之一One of the discovered route is
/albatross/user/loginthat accepts[userName,sessionId]发现的路由之一是
/albatross/user/login接受[userName,sessionId]Upon enumeration, he received feedback with a
200 OK responsecontaining apassword枚举后,他收到了包含
password的200 OK response反馈

This gaping hole in the code as seen above, exposed a temporary password generation mechanism which is ready to be chained to the next possible vulnerability.
如上所示,此代码漏洞极大地暴露了一个临时密码生成机制,该机制已准备好链接到下一个可能的漏洞。
步骤#3:在暴露的路线上进行身份验证 (Step #3: Authenticate on exposed route)
Using route from STEP #2
/albatross/user/loginthat accepts[userName,sessionId,password,...], he substituted the password received inpasswordfield从STEP#2
/albatross/user/login使用路由 接受[userName,sessionId,password,...],他替换了password字段中收到的passwordUpon enumeration, he received feedback with a
200 OK responsecontaining anotherpassword枚举后,他收到了包含
200 OK response反馈,其中包含另一个password

This gaping hole in the code as seen above, is enabling the researcher to re-authenticate with the temporary password provided from Step #2.
如上所示,此代码中的漏洞使研究人员能够使用步骤2中提供的临时密码重新进行身份验证。
步骤#4:获取承载令牌 (Step #4: Acquire Bearer Token)
Using route from STEP #2
/albatross/user/loginthat accepts[userName,sessionId,password,...], he substituted the password received inpasswordfield from Step #3从STEP#2
/albatross/user/login使用路由 接受[userName,sessionId,password,...],他替换了步骤3中在password字段中收到的passwordUpon enumeration, he received feedback with a
200 OK responsecontaining abearer/access token枚举后,他收到了包含
bearer/access token的200 OK response反馈Pedro also discovered that it is possible to login as a normal web user on the
/albatross/user/loginendpoint, which will yield an authenticated cookie instead of a token, allowing access to the web administration consolePedro还发现,可以在
/albatross/user/login端点上以普通Web用户身份/albatross/user/login,这将生成经过身份验证的cookie而不是令牌,从而允许访问Web管理控制台

With the password acquired from Step #3, the researcher was able to acquire an access/bearer token
使用从步骤3获得的密码,研究人员能够获取访问/承载令牌
步骤#5:在另一条裸露的路线上进行侦察 (Step #5: Recon on another exposed route)
Leveraging the attack surface, he filtered out the list of routes that accept a
bearer(access) tokenand discovered several routes利用攻击面,他过滤了接受
bearer(access) token的路由列表 发现了几条路Pedro then focussed on a discovered route
/albatross/restAPI/v2/nmap/run/scanthat allows an authenticated user to perform NMAP based scans然后,Pedro专注于发现的路由
/albatross/restAPI/v2/nmap/run/scan,该路由允许经过身份验证的用户执行基于NMAP的扫描Having access to NAMP allowed him running arbitrary commands if there was another route available to upload a script file that can be passed as an argument to nmap with
nmap ... —- script=<FILE>如果有另一种途径可以上载脚本文件,可以使用NAMP来访问NAMP,则他可以运行任意命令,该脚本文件可以作为参数使用
nmap ... —- script=<FILE>传递给nmap ... —- script=<FILE>

With the access/bearer token acquired from Step #4, the researcher was now able to detect other routes (from enumerated attacker surface) that accepts this token to validate the request. However, in order to induce command injection he would need to upload a script with the appropriate command embedded in it.
通过从步骤#4获取的访问/承载令牌 ,研究人员现在能够检测到其他路由(来自枚举的攻击者表面),接受该令牌以验证请求。 但是,为了引发命令注入,他将需要上载一个嵌入了适当命令的脚本。
步骤#6:在另一条公开的路由上上传脚本 (Step #6: Upload script on another exposed route)
Leveraging the attack surface, he filtered out the list of routes that provide
fileUploadutility (accepting multipart fileUpload)利用攻击面,他过滤了提供
fileUpload实用程序的路由列表(接受multipart fileUpload)He discovered an exposed route
/albatross/upload/patchthat accepts afileas an attacker controlled input他发现了一个暴露路径
/albatross/upload/patch,该路径接受file作为攻击者控制的输入Upon attempting to initiate file upload on this route, he received a
200 OKresponse with a JSON error message.尝试在此路由上启动文件上传后,他收到了
200 OK响应,并带有JSON错误消息。

Using the attack surface, the researcher was able to detect an additional route that enables a file to be uploaded to the host.
通过使用攻击面,研究人员能够检测到一条其他路径,该路径使文件可以上传到主机。
步骤#7:命令注入以执行脚本 (Step #7: Command Injection to execute script)
Pedro then returned to discovered route from Step#6
/albatross/restAPI/v2/nmap/run/scanthat allows an authenticated user to perform NMAP based scans然后,Pedro从步骤6
/albatross/restAPI/v2/nmap/run/scan返回到发现的路由,该路由允许经过身份验证的用户执行基于NMAP的扫描Using attacker controlled
httpRequestvector he substituted theuploaded fileNamefrom Step#5 to trigger the NMAP scan leading to execution ofnmap — script=[path_to]/evilscript.scwhich led to the inquiry他使用攻击者控制的
httpRequest矢量替换了步骤5中uploaded fileName,以触发NMAP扫描,从而导致执行nmap — script=[path_to]/evilscript.sc导致了询问Using attacker controlled
httpRequestvector he substituted theuploaded fileNamefrom Step#5 to trigger the NMAP scan leading to execution ofnmap — script=[path_to]/evilscript.scwhich led to the inquiryos.execute("/usr/bin/whoami > /tmp/testing")thereby returning an usera3userwith administrative privilege他使用攻击者控制的
httpRequest矢量替换了步骤5中uploaded fileName,以触发NMAP扫描,从而导致执行nmap — script=[path_to]/evilscript.sc导致查询os.execute("/usr/bin/whoami > /tmp/testing")从而返回具有管理特权的用户a3user
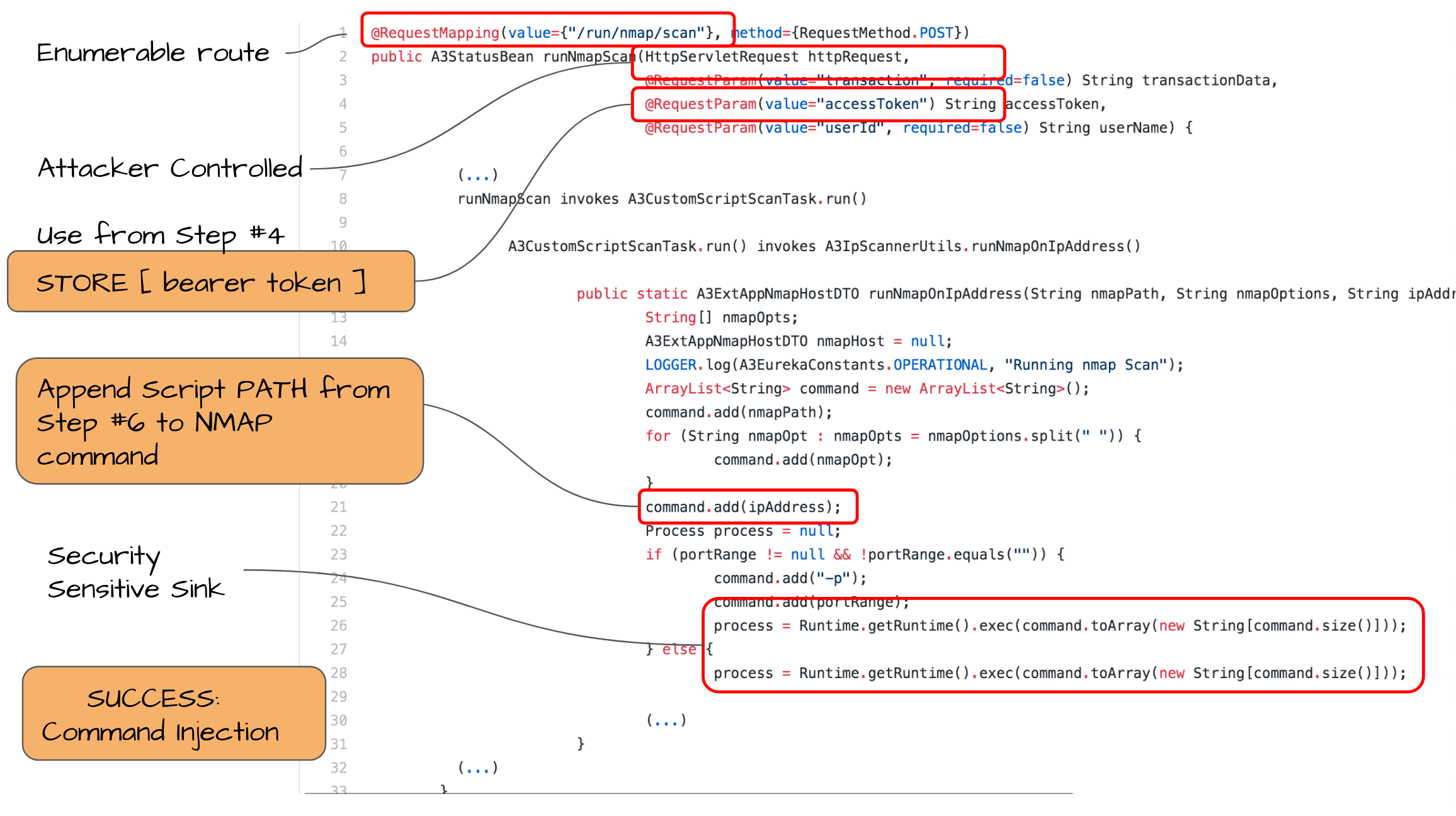
Now, the researcher reverted to the route from Step #5 to inject a command to trigger the script uploaded in Step #6
现在,研究人员返回到步骤5的路由,以注入命令以触发在步骤6中上传的脚本
步骤#7:主机访问(默认供应商设置未更改) (Step #7: Host access (with default vendor settings not changed))
Using
a3userfrom Step#7, an attempt was made to SSH to achieve remote code execution as root on the IDRM virtual appliance, leading to complete system compromise使用步骤7中的
a3user,尝试以SSH身份在IDRM虚拟设备上以root身份执行远程代码执行,从而导致系统全面受损
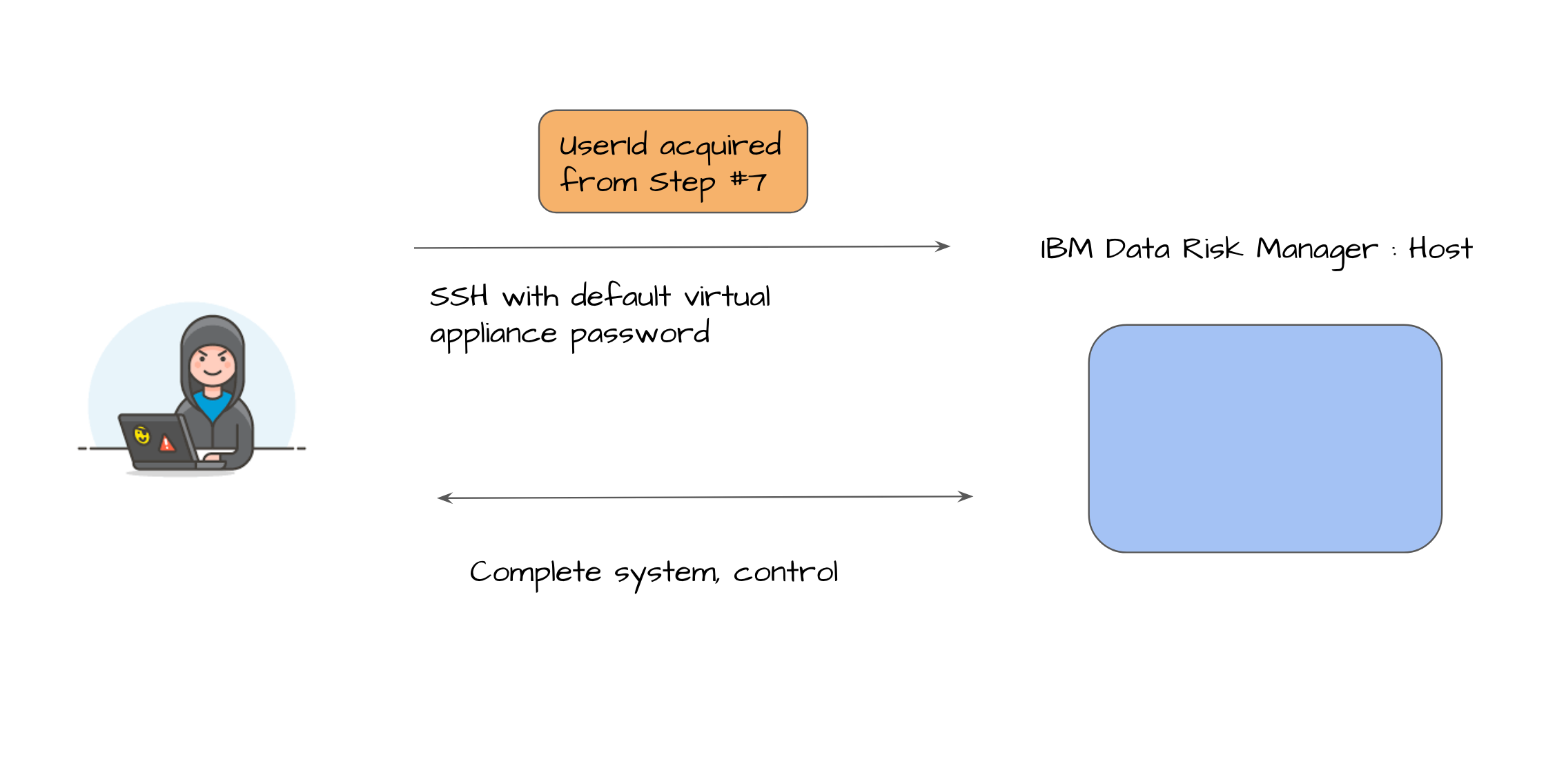
攻击链的视觉摘要 (Visual Summary of Attack Chain)

4个外卖菜 (4 Takeaways)
You may be confident that your perimeter defenses are robust enough to pick up on most such threats. However, adversaries have long known how reactive cybersecurity tools work — and they make it their mission to circumvent them.
您可能会相信自己的外围防御系统足够强大,足以应付大多数此类威胁。 但是,对手早就知道React式网络安全工具的工作原理-绕过它们是他们的使命。
A more precise approach for securing applications by industry practitioners, is taint analysis. In taint analysis, which is a kind of program analysis that can in principle detects most common forms of security issues, security properties are expressed as direct information flows from sources to sinks: either from untrusted sources to sensitive sinks (integrity) or conversely from sensitive sources to untrusted sinks (confidentiality).
用于确保行业从业人员保护应用程序的更精确方法是污点分析 。 在污点分析中,该分析是一种原则上可以检测到最常见形式的安全性问题的程序分析,其安全属性表示为从源到接收器的直接信息流:从不受信任的源到敏感的接收器(完整性),或者相反地从敏感的接收器来源到不可信的接收器(机密性) 。
- The big aha that I hope the industry will takeaway from this incident is that sophisticated attackers think in terms of chaining their exploit steps together. In network security, we might call this peeling the onion. Like network security, in AppSec we need to start thinking about vulnerabilities as nodes. It’s not just what data the node contains, but what it also what it has access to. This is how we need to evaluate vulnerabilities. It’s not just the severity of vulnerability but how can it be used to launch the next step in the exploit chain. 我希望业界从这次事件中得到的最大收益是,成熟的攻击者会考虑将其利用步骤链接在一起。 在网络安全中,我们可以称其为剥洋葱。 像网络安全一样,在AppSec中,我们需要开始考虑将漏洞作为节点。 这不仅是节点包含的数据,还包括它可以访问的数据。 这就是我们需要评估漏洞的方式。 这不仅是漏洞的严重性,而且如何用于启动漏洞利用链中的下一步。
- This highlights the asymmetry between attackers and defenders more than ever. Attackers have always had an advantage because they only need to find one way in, while defenders must remediate all potential vulnerabilities. In practice, for many organizations, this meant fixing all critical vulnerabilities and maybe some medium. However, there’s no rest for the weary and development organizations need to go deeper to fix more vulnerabilities to prevent vulnerability chains being linked together from seemingly lower severity issues. 这比以往任何时候都更加突出了攻击者和防御者之间的不对称性。 攻击者一直具有优势,因为他们只需要找到一种方法,而防御者则必须补救所有潜在的漏洞。 实际上,对于许多组织而言,这意味着要修复所有关键漏洞,甚至可能修复某些漏洞。 但是,疲惫不堪,开发组织需要更深入地解决更多漏洞,以防止将漏洞链链接在一起看似严重性较低的问题。
- Don’t take the basics for granted. Although everyone knows default passwords should not be used, even highly talented people make mistakes. When security is important double-check the basics. 不要将基础知识视为理所当然。 尽管每个人都知道不应使用默认密码,但即使是才华横溢的人也会犯错。 当安全性很重要时,请仔细检查基础知识。
Treat ethical hackers and vulnerability researchers with the utmost respect. People like Pedro Riberio play an important role in the security ecosystem and when they are attempting to disclose vulnerabilities responsibly, we need to clear the red tape and make it easy for them.
最大限度地尊重道德黑客和漏洞研究人员。 像Pedro Riberio这样的人在安全生态系统中扮演着重要的角色,当他们试图以负责任的方式披露漏洞时,我们需要清除繁琐的繁琐手续,并对其进行简化 。
ShiftLeft视觉:连接漏洞链中的不可见链接 (ShiftLeft Ocular: Connecting the Invisible Links in the Vulnerability Chain)
The write-up above does look like a magician’s work or a craftsman diligently searching and chaining to craft the exploit. It might seem random on the surface, but there is a process behind it.
上面的内容看起来确实像魔术师的作品或工匠孜孜不倦地搜索和链接以制作漏洞利用程序。 表面上看似随机,但背后有一个过程。
If we can describe the code completely as a graph, it is possible to ask questions to the graph in a succinct manner using a vulnerability modeling language called Ocular.
如果我们可以将代码完整地描述为图形,则可以使用称为Ocular的漏洞建模语言以简洁的方式向图形提出问题。
Using this graph language, can we ask the following questions to preemptively determine if any code base is susceptible to such a chained vulnerability?
使用这种图形语言 ,我们能否提出以下问题来抢先确定是否有任何代码库易受此类链式漏洞的影响?
获取应用程序的攻击面 (Get Attack Surface of Application)
获取应用程序的身份验证模型 (Get Authentication Model of Application)
确定从攻击面到安全敏感接收器的异味流(并关联从攻击面到创建链的REST / WEB路由) (Determine taint flow from attack surface to security sensitive sinks (and correlate REST/WEB routes from attack surface to create chains))
I like to take this opportunity to thank Andrew Fife and Suchakra Sharma for the effort and expertise that they contributed to edit and review this narrative.
我想借此机会感谢Andrew Fife和Suchakra Sharma所做的努力和专业知识,他们为编辑和审查此叙述做出了贡献。
发现问题





















 603
603











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








