csrf跨站请求伪造
什么是CSRF Attack ..? (What is CSRF Attack..?)
A Cross-Site Request Forgery is also known as CSRF, one-click attack or session riding. This is a sort of assault whereby web site with noxious aim will send a request to a web application that a client is already confirmed for. These requests are directed to the target site which the user is validated for through their browser because their browser is authenticated against the site. This will permit the attacker to get to the usefulness of the web application through the victim’s already verified browser.
跨站点请求伪造也被称为CSRF,一键式攻击或会话控制。 这是一种攻击,具有有害目的的网站会将请求发送到已经确认客户端的Web应用程序。 这些请求被定向到用户通过其浏览器对其进行验证的目标站点,因为他们的浏览器已针对该站点进行了身份验证。 这将使攻击者可以通过受害者已经验证的浏览器来使用Web应用程序。
这个怎么运作.. (How it Works..)
CSRF attack surfaces are often HTTP requests that cause a victim-related change, for example: name, email address, website, and even password. Sometimes it is also used to change the authentication status. This is mainly dependent on if the target web application’s user is still logged into the web application through his browser.
C SRF攻击面通常是导致受害人相关更改的HTTP请求,例如:名称,电子邮件地址,网站,甚至密码。 有时它也用于更改身份验证状态。 这主要取决于目标Web应用程序的用户是否仍通过其浏览器登录到Web应用程序。

For example, if a user visited an online banking website which had CSRF vulnerabilities and remained logged in, and another website he visits has a CRSF attack on that banking site, the attack would be executed as if he had done it himself. Now that malicious web site could get advantages from that online banking website. such as transferring money to another account and steal all money on his account.
例如,如果用户访问了一个具有CSRF漏洞并且仍保持登录状态的在线银行网站,并且他访问的另一个网站对该银行站点进行了CRSF攻击,则该攻击将被执行,就好像他自己做了一样。 现在,该恶意网站可以从该网上银行网站获得好处。 例如将资金转入另一个帐户并窃取他帐户中的所有资金 。
These attacks are mostly used against web applications which deal with social media, in-browser email clients and online banking. It can result in damaged client relationships, unauthorized money transfers, changed passwords and data theft including stolen session cookies
这些攻击主要用于处理社交媒体,浏览器内电子邮件客户端和在线银行业务的Web应用程序。 这可能会导致客户关系损坏,未经授权的汇款,更改的密码和数据盗窃(包括会话cookie被盗)
识别CSRF漏洞 (Identifying the CSRF Vulnerability..)
The easiest way to identify if a web application would suffer from a CSRF attack is checking if each form and link has an unexpected and unpredictable token attached to each user.
识别Web应用程序是否会遭受CSRF攻击的最简单方法是检查每个表单和链接是否都具有附加给每个用户的意外且不可预测的令牌。
CSRF预防和缓解方法 (Methods of CSRF Prevention and Mitigation..)
There are lot of methods for prevention and mitigation these attacks. Prevention is a matter of safeguarding login credentials and denying unauthorized actors’ access to applications. To do that we can follow these things.• Logging off web applications when not in use• Securing usernames and passwords• Do not allowing browsers to remember passwords and usernames
有很多方法可以预防和缓解这些攻击。 预防是维护登录凭据并拒绝未经授权的参与者访问应用程序的问题。 为此,我们可以遵循这些步骤。 •不使用时注销Web应用程序•保护用户名和密码•不允许浏览器记住密码和用户名
For web applications, the most common mitigation method is Synchronizer Token Pattern. It generates unique tokens for every session request or ID. These are checked and verified by the server. Session requests having either duplicate tokens or missing values are blocked. Then, a request that doesn’t match its session ID token is prevented from reaching an application.
对于Web应用程序,最常见的缓解方法是Synchronizer Token Pattern 。 它为每个会话请求或ID生成唯一的令牌。 这些由服务器检查和验证。 具有重复令牌或缺少值的会话请求将被阻止。 然后,将阻止与其会话ID令牌不匹配的请求到达应用程序。
什么是CSRF令牌...? (What is a CSRF Token..?)
Synchronizer Token Pattern is an approach where a unique token or a value is generated by server-side application for every session. It is Embedded as a hidden area in HTML types which will be validated with the aid of the server and authorize the request that should be completed. An attacker cannot read or regulate cookie values due to the fact of the same-origin requirement which will prevent CSRF.
同步器令牌模式是一种方法,其中服务器端应用程序为每个会话生成唯一的令牌或值。 它被嵌入为HTML类型的隐藏区域,将在服务器的帮助下进行验证并授权应完成的请求。 由于存在相同来源的要求(这将阻止CSRF),攻击者无法读取或调节cookie值。
该令牌如何工作? (How this Token Works?)
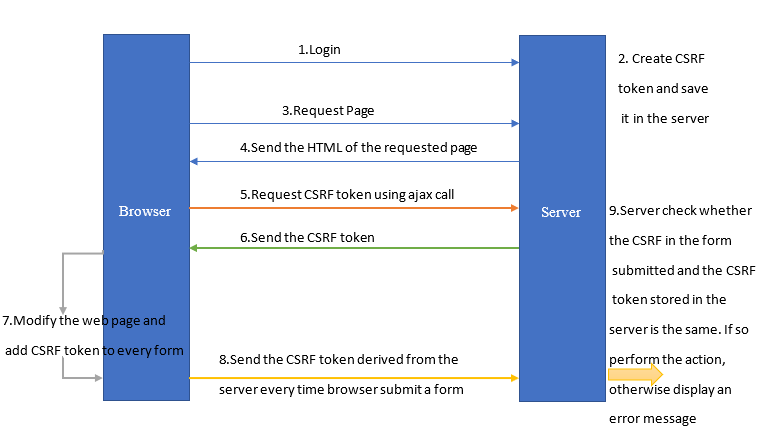
As above diagram, user request login page and log in to the system. Then at the same time server creates a CSRF token and save it in the server side. Next time when user interact with server, browser ask server to send CSRF token using AJAX call. Then browser modify the related web page and add CSRF token to every form. Then user submit data along with CSRF token. So server can check and verify whether the request came from original user by comparing CSRF token received and stored in own. If they match, server perform the action and if it didn’t match server display an error message.
如上图,用户请求登录页面并登录到系统。 然后,服务器同时创建一个CSRF令牌并将其保存在服务器端。 下次用户与服务器交互时,浏览器会要求服务器使用AJAX调用发送CSRF令牌。 然后浏览器修改相关的网页并将CSRF令牌添加到每个表单。 然后,用户与CSRF令牌一起提交数据。 因此,服务器可以通过比较自己接收和存储的CSRF令牌来检查并验证请求是否来自原始用户。 如果它们匹配,则服务器执行操作,如果不匹配,则服务器显示错误消息。
参考.. (References..)
网页实现 (Web page Implementation..)
This sample project developed using HTML, PHP and JavaScript. To get the source code Click here.
该示例项目使用HTML,PHP和JavaScript开发。 要获取源代码,请单击此处 。
It is a login form and you have to log into the application providing the hard-coded username and password. It will redirected automatically to another page.
这是一个登录表单,您必须登录并提供包含硬编码的用户名和密码的应用程序。 它将自动重定向到另一个页面。
The credentials as,
凭据为,
Username: admin Password: 1234
用户名 : admin 密码 : 1234

I create this page for only one user. So this page has only one username. So any other invalid entries must be unauthorized. Any invalid entry that user enter(username or password), user is prompt to a error message.
我仅为一个用户创建此页面。 因此,此页面只有一个用户名。 因此,任何其他无效条目都必须是未经授权的。 用户输入的任何无效条目(用户名或密码)都会提示用户输入错误消息。

After the user giving the right credentials he will be redirected to page called “login.php” and it will look like this. It will welcome the user from a simple PHP line of code and start a session.
用户提供正确的凭据后,他将被重定向到名为“ login.php”的页面,它看起来像这样。 它将通过简单PHP代码行欢迎用户并启动会话。
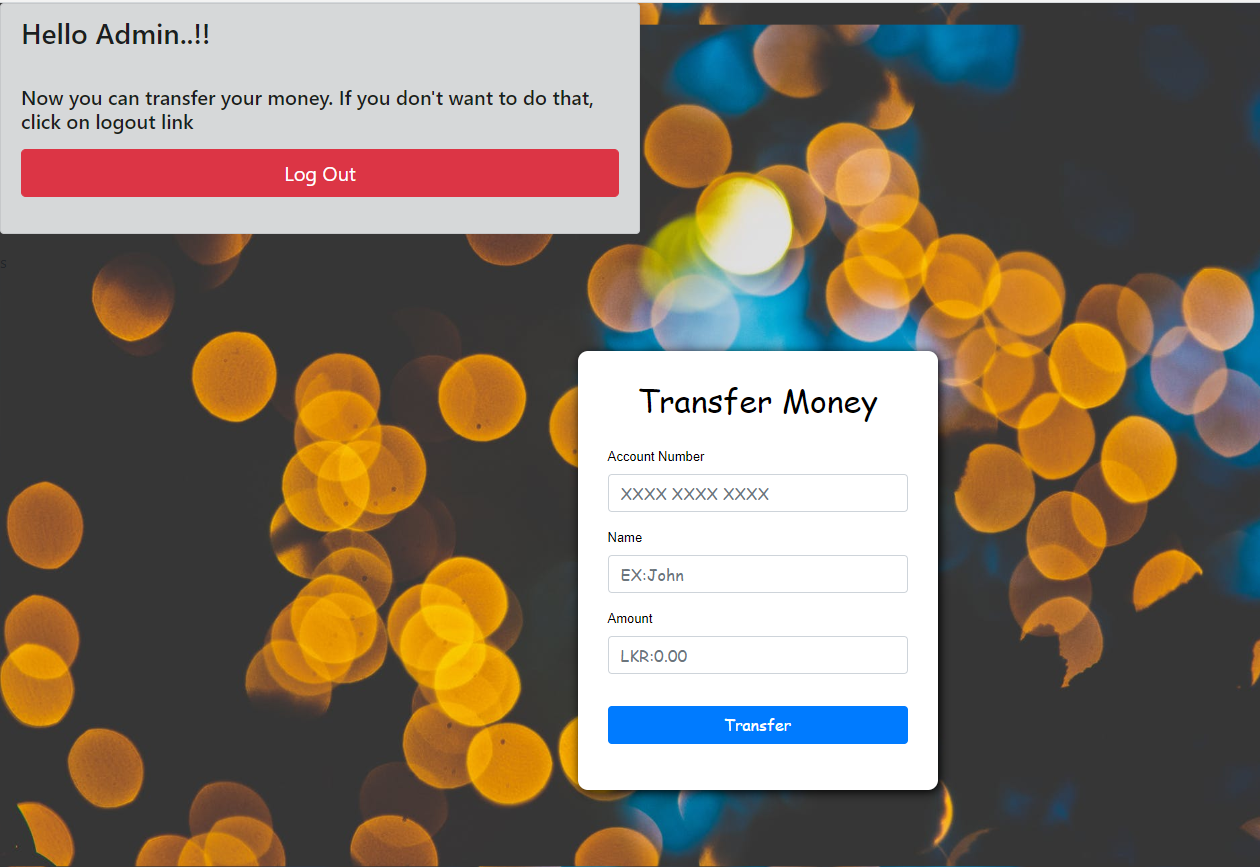
If the user press the “logout button” he will be redirected to the previous login page with the session destroying.
如果用户按下“登出按钮”,则他将被重定向到先前的登录页面,并且会话将被破坏。
when the index page load a session will start as well as a cookie will set in name of Admin.
当索引页加载时,将启动一个会话,同时还将以Admin名称设置cookie。

There is a function generate token, it will be a create a random number and it will be saved in the session variable call token. That will be save in the server side. That token will generate for only that person who logged in.
有一个函数生成令牌,它将是一个创建随机数,并将其保存在会话变量调用令牌中。 那将保存在服务器端。 该令牌只会为登录的那个人生成。
Then session will be automatically destroyed. Then user must be need to login again to see the “login.php” page.
然后会话将被自动销毁。 然后,用户必须再次登录才能看到“ login.php”页面。

I used function with encoded with “base64_encoding” for creating this unique token. It is more secure than using md5 or other random generating values.
我使用带有“ base64_encoding”编码的函数来创建此唯一令牌。 比使用md5或其他随机生成值更安全。

Then we have to call this static generate function on the value field inside the HTML hidden area that we have created earlier . This field is invincible to the interface and value will be randomly changed when the user refresh the browser.
然后,我们必须在我们之前创建HTML隐藏区域内的value字段上调用此static generate函数。 该字段对界面无敌,当用户刷新浏览器时,值将随机更改。

If the user is authenticated, the user will redirect to login.php where you can add transaction details. When we come back again to the login.php page we can a form like below.
如果用户通过了身份验证,则用户将重定向到login.php 您可以在其中添加交易明细。 当我们再次返回login.php页面时,我们可以使用如下形式。
We can use any number for “Account Number” column, any word for “Name” column and any number for “Amount” column.
我们可以在“帐号”列中使用任何数字,在“名称”列中使用任何单词,在“金额”列中使用任何数字。

Account Number, Name and Amount we are passing the value for CSRF token with the URL, it is a hidden value an the method that is using is POST and it is not visible to eye from the URL.
帐号,名称和金额我们通过URL传递CSRF令牌的值,它是一个隐藏的值,所使用的方法是POST,从URL看不到它。

So the token is valid and we can see like this for the first time.
因此令牌是有效的,我们可以第一次看到这样的令牌。

But if we try to refresh the browser, the token will be updated and then this popup will be displayed.
但是,如果我们尝试刷新浏览器,令牌将被更新,然后将显示此弹出窗口。

To retrieve the CSRF token an AJAX call should be executed.I took two variables and one for token and one for session cookie.
要检索CSRF令牌,应执行AJAX调用。我使用了两个变量,一个用于令牌,一个用于会话cookie。

The AJAX call type is POST and its URL is “getdata.php”. If the action worked it will display data the session ID on the console.
AJAX调用类型为POST,其URL为“ getdata.php” 。 如果操作成功,它将在控制台上显示数据和会话ID。

Then get session ID and pass it trough “sha1” algorithm and assign it to an array called id.
然后获取会话ID,并将其通过“ sha1”算法传递,并将其分配给名为id的数组。
So that’s all. You can get this project from my Git hub repository.
就是这样。 您可以从我的Git中心存储库中获得该项目。
谢谢。 再见。 (Thank you. See you soon.)
csrf跨站请求伪造







 本文深入探讨了跨站请求伪造(CSRF)的威胁,并详细介绍了设计模式中的一种缓解策略——同步器令牌模式,以保护HTTPS应用程序免受此类攻击。
本文深入探讨了跨站请求伪造(CSRF)的威胁,并详细介绍了设计模式中的一种缓解策略——同步器令牌模式,以保护HTTPS应用程序免受此类攻击。














 7912
7912

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








