密码学算法
密码学 (Cryptography)
The practice and the study of techniques for secure communication in the presence of third parties is known as cryptography. Secure communication means that when two parties communicate, they don’t want third parties to eavesdrop on their communication and/or alter them. confidentiality, data integrity, authentication, and non-repudiation[4] are central components of modern cryptography.
在第三方在场的情况下进行安全通信的技术的实践和研究称为加密。 安全通信意味着当两方通信时,他们不希望第三方窃听其通信和/或更改它们。 机密性 , 数据完整性 , 身份验证和不可否认性 [4]是现代加密技术的核心组成部分。
秘密密钥算法 (Secrete Key Algorithms)
Secrete key algorithms, otherwise known as symmetric key algorithms use a single key for both encryption and decryption of the message. So the both sending party and receiving party should have shared the key beforehand. These algorithms are very fast because they are based on simple mathematical operations.
秘密密钥算法(也称为对称密钥算法)将单个密钥用于消息的加密和解密。 因此,发送方和接收方都应该事先共享密钥。 这些算法非常快速,因为它们基于简单的数学运算。
Here are some of the common secrete key algorithms that are used for encryption and decryption.
以下是一些用于加密和解密的常见秘密密钥算法。
数据加密标准(DES) (Data Encryption Standard (DES))
DES is one of the most popular symmetric encryption algorithms out there. It is a block cipher that was developed by IBM in the early 1970s. DES encrypts blocks 64 bits of plaintext to ciphertext using a 56 bit key. DES operations can be done in two ways.
DES是目前最流行的对称加密算法之一。 这是由IBM在1970年代初期开发的分组密码。 DES使用56位密钥将64位纯文本块加密为密文。 DES操作可以通过两种方式完成。
Electronic Code Book(ECB) serially encrypts every 64 bit plaintext using the same 56 bit key. Because of this, if two identical plaintext blocks are encrypted using the same key, the resulting ciphertext blocks are the same. Therefore, an attacker could identify similar or identical traffic flowing through a communications channel.
电子密码书(ECB)使用相同的56位密钥对每个64位明文进行串行加密。 因此,如果使用相同的密钥对两个相同的明文块进行加密,则生成的密文块将相同。 因此,攻击者可以识别流经通信信道的相似或相同流量。
Cipher block chaining (CBC) on the other hand, bitwise XORs previous ciphertext block with the current plaintext block and then encrypts it using the DES key to make the current ciphertext block. So, the encryption of each block is dependent on the previous block, and encryption of identical plaintext blocks will result in different ciphertext blocks.
另一方面,密码块链接(CBC)将先前的密文块与当前的纯文本块进行按位XOR运算,然后使用DES密钥对其进行加密以生成当前的密文块。 因此,每个块的加密取决于先前的块,相同的明文块的加密将导致不同的密文块。
However, due to its small key size, DES vulnerable to modern brute force attacks, differential cryptanalysis (DC), linear cryptanalysis (LC), and Davies’ attack. Because of this, many former systems that used DES now use 3DES which is 256 times more secure than DES.
但是,由于密钥较小,因此DES容易受到现代暴力攻击, 差分密码分析 (DC), 线性密码分析 (LC)和Davies的攻击 。 因此,许多以前使用DES的系统现在使用3DES,其安全性是DES的256倍。

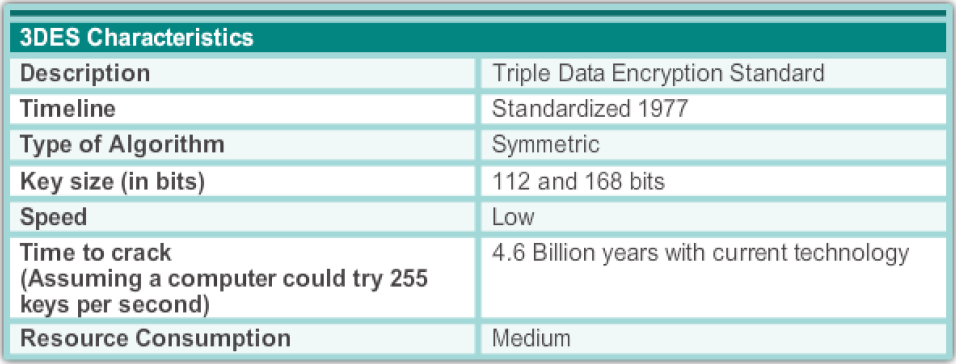
三重DES(3DES或TDES) (Triple DES (3DES or TDES))
3DES is an adapted version of DES which uses the same algorithm to produce more secure encryption. It does this by applying the DES encryption algorithm three times for each 64 bit data block in the plaintext. 3DES uses a key bundle that has three 56 bit keys and encrypts a data block with the first key, decrypts it with the second key, and encrypts again with the third key. Decryption is done in the reverse order. It requires more processing time than DES because of the two additional operations.
3DES是DES的改编版本,它使用相同的算法来产生更安全的加密。 它通过对明文中的每个64位数据块应用DES加密算法三次来实现此目的。 3DES使用具有三个56位密钥的密钥束,并使用第一个密钥加密数据块,使用第二个密钥解密数据块,然后使用第三个密钥再次加密。 解密以相反的顺序进行。 由于有两个附加操作,因此它比DES需要更多的处理时间。
If the keys in the key bundle are K1,K2 and K3, 3DES defines three keying options.
如果密钥束中的密钥是K1,K2和K3,则3DES定义了三个密钥选项。
- All three keys are independent. It is known as triple-length keys.This is the strongest form with 3 x 56 = 168 independent key bits. 这三个键都是独立的。 它被称为三倍长度密钥,这是最强大的形式,具有3 x 56 = 168个独立密钥位。
- K1 and K2 are independent and K1 = K3. It is known as double-length keys. It provides a shorter key length of 112 bits. This was deprecated in 2016. K1和K2是独立的,并且K1 = K3。 它被称为双长度键。 它提供了较短的112位密钥长度。 自2016年起已弃用。
- All three keys are identical (K1 = K2 = K3). This is the same as DES as two operations cancels out. 所有三个键都相同(K1 = K2 = K3)。 这与DES相同,因为取消了两个操作。
高级加密标准(AES) (Advanced Encryption Standard (AES))
1997, the AES initiative was announced, and the public was invited to propose encryption schemes to replace DES. After five year process of standardization in which 15 competing designs were presented an evaluated, Rijndael block cipher was selected as the AES algorithm by U.S. National Institute of Standards and Technology (NIST).
1997年,AES倡议宣布,并邀请公众提出加密方案来代替DES。 经过五年的标准化过程,评估了15个竞争性设计,Rijndael分组密码被美国国家标准技术研究院(NIST)选择为AES算法。
AES is a variant of Rijndael, which has a fixed block size of 128 bits, but can have three different key sizes : 128, 192 and 256 bits. By contrast, original Rijndael is specified with block sizes and key sizes that may be any multiple of 32 bits, with a minimum of 128 and a maximum of 256 bits.
AES是Rijndael的一种变体,它具有128位的固定块大小,但可以具有三种不同的密钥大小:128、192和256位。 相比之下,原始的Rijndael指定的块大小和密钥大小可以是32位的任意倍数,最小为128位,最大为256位。
AES have few distinct advantages when compared to DES and 3DES:
与DES和3DES相比,AES具有一些独特的优势:
- It is much stronger than DES because of it’s key lengths. 它的密钥长度比DES强得多。
- It runs much faster than 3DES on comparable hardware. 在同类硬件上,它的运行速度比3DES快得多。
- It is more efficient than DES and 3DES on comparable hardware, usually by a factor of five if compared to DES. 在可比较的硬件上,它比DES和3DES效率更高,如果与DES相比通常要高出五倍。
- AES is more suitable for high-throughput, low-latency environments, especially if pure software encryption is used. AES更适合于高吞吐量,低延迟的环境,尤其是在使用纯软件加密的情况下。
However, AES is a relatively young algorithm and cryptographic community tends to trust mature algorithms than the younger ones.
但是,AES是一个相对较年轻的算法,与较年轻的算法相比,密码学界更倾向于信任成熟的算法。

Rivest密码6(RC6) (Rivest Cipher 6 (RC6))
RC6 is a symmetric key block cipher which was derived from its predecessor RC5, to meet the requirements of the Advanced Encryption Standard(AES). Infact, it was one of the five finalists in the AES competition and was submitted to the NESSIE and CRYPTREC projects. RC6 is a proprietary algorithm, which was patented by RSA Security.
RC6是从其前身RC5衍生而来的对称密钥块密码,可满足高级加密标准(AES)的要求。 实际上,它是AES竞赛的5个入围者之一,并已提交给NESSIE和CRYPTREC项目。 RC6是一种专有算法,已获得RSA Security的专利。
RC6 has a block size of 128 bits and supports key sizes of 128, 192 and 256 bits and then up to 2040. RC6 includes four working registers instead of two like in RC5, and includes integer multiplication as an additional primitive operation. This inclusion of multiplication allows for greater security, fewer rounds and increased throughput.
RC6的块大小为128位,并支持128、192和256位的密钥大小,直至2040年。RC6包括四个工作寄存器,而不是像RC5中的两个寄存器,并且包括整数乘法作为附加的基本操作。 包含乘法可以提高安全性,减少回合次数并提高吞吐量。

That’s it for this article. If you found this interesting, stay tuned for my next article on public key algorithms in cryptography. See you on the next one! 😊
本文就是这样。 如果您发现这很有趣,请继续关注我的下一篇有关密码学中的公钥算法的文章。 下一个见! 😊
翻译自: https://medium.com/swlh/secret-key-algorithms-in-cryptography-b29de0ef96bd
密码学算法





















 5088
5088

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








