微信小程序secret
At the beginning of last year, I wrote an article titled How to secure and manage secrets using Google Cloud KMS, explaining how we can use Google Cloud KMS (Key Management System) to encrypt secrets and securely use it in our applications.
去年初,我写了一篇标题为“ 如何使用Google Cloud KMS保护和管理机密 ”的文章,解释了如何使用Google Cloud KMS(密钥管理系统)对机密进行加密并在我们的应用程序中安全地使用它。
I mentioned it is a decent approach because of the lack of support for good secret management solutions within the Google cloud ecosystem. It is kind of, a hacky way to get the job done, because,
我提到这是一种不错的方法,因为它缺乏对Google云生态系统中良好的秘密管理解决方案的支持。 这是一种完成工作的简单方法,因为,
- it requires a lot of code setup 它需要大量的代码设置
- had to keep the encrypted version within version control 必须将加密版本保留在版本控制中
- no easy way to manage these secrets (like a console UI) 没有简单的方法来管理这些机密(例如控制台UI)
Finally, there is now an easier & better a solution, Google has announced their secret management solution Google Secret Manager.
最后,现在有一个更简单,更好的解决方案,Google宣布了其秘密管理解决方案Google Secret Manager 。
Huge shout-out to Google Cloud and their team behind this solution.
此解决方案背后对Google Cloud及其团队大声疾呼。
Secret Manager is a secure and convenient storage system for API keys, passwords, certificates, and other sensitive data. Secret Manager provides a central place and single source of truth to manage, access, and audit secrets across Google Cloud.
Secret Manager是用于API密钥,密码,证书和其他敏感数据的安全,便捷的存储系统。 Secret Manager提供了一个中心位置和单一事实来源,可以跨Google Cloud管理,访问和审计秘密。
Let's get our hands dirty…
让我们弄脏双手吧……
创造秘密 (Creating Secrets)
Secret Manager offers a full set of APIs for creating & managing secrets so it can be integrated with dev tools, pipelines, etc, check out their Official Docs. Better, it has a fancy Web UI for easier management without the need to write any code. A typical workflow will be like, the secrets will be added by the SRE team and they grant permission to individual projects to access it. So, for this example, we will be using Web UI for secrets creation.
Secret Manager提供了用于创建和管理机密的全套API,因此可以将其与开发工具,管道等集成,请查看其官方文档 。 更好的是,它具有精美的Web UI,可简化管理,而无需编写任何代码。 一个典型的工作流程将是这样,机密信息将由SRE团队添加,并向单个项目授予访问权限。 因此,在此示例中,我们将使用Web UI创建机密。
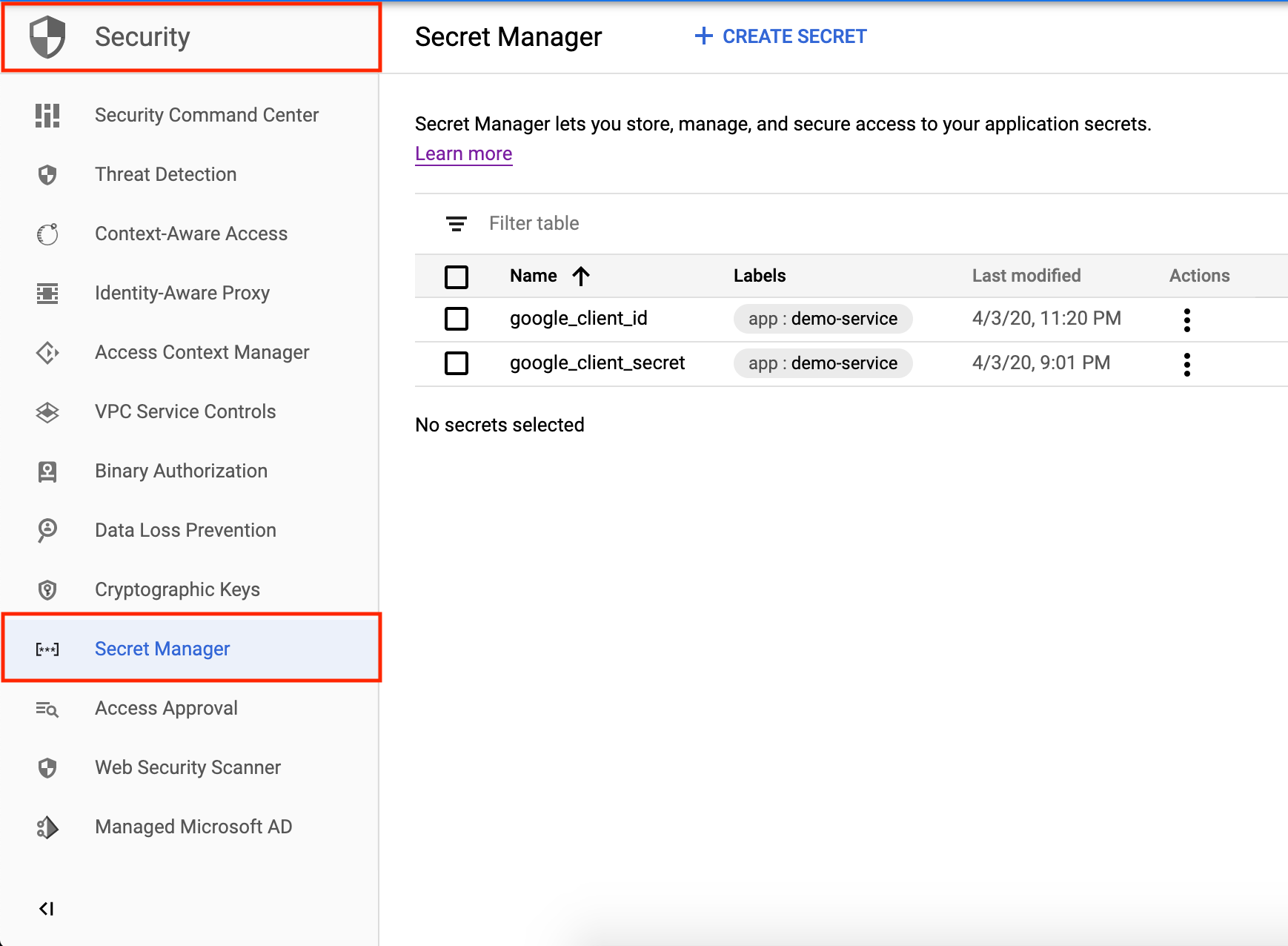
Under Security -> Secret Manager , you can now create & manage secrets.
在“ Security -> Secret Manager ,您现在可以创建和管理秘密。
秘密定义 (Secrets Definition)
A Secret consists of a name, labels, region, and versions.
机密由名称 , 标签 , 区域和版本组成。
Versions are where we store our secret value,
版本是我们存储秘密价值的地方,
- we can have multiple versions per secret, useful for key rotation and management 我们每个秘密可以有多个版本,对于密钥轮换和管理非常有用
- The secret value can be plain-text or a file, Secret Manager will store it as base64 encoded data, convenient to store any form of secrets. 秘密值可以是纯文本或文件,Secret Manager将其存储为base64编码的数据,方便存储任何形式的秘密。
- You can disable or destroy versions to deactivate or remove a secret (useful for deprecations, etc…) 您可以禁用或销毁版本以停用或删除机密(用于弃用等)。
For our example, we will be creating the following secrets (check the previous image),
对于我们的示例,我们将创建以下机密(请检查上一张图片),
google_client_id=prod_client_1google_client_secret=prod_client_secret_123NOTE: Creating a secret requires roles/secretmanager.admin IAM role on the parent project.
注意 :创建密钥需要在父项目上具有roles/secretmanager.admin IAM角色。
Now we have our secrets defined & ready for use. Let’s see how we can access it within our application.
现在,我们已定义好秘密并准备使用。 让我们看看如何在应用程序中访问它。
访问秘密 (Accessing Secrets)
We will be setting up a simple spring boot application and deploy it to Google AppEngine. With the power of Spring Boot AutoConfiguration , we don't really need to write any code to access these secrets. Instead, with a few lines of configuration, we can automagically access our secrets, thus offering a seamless integration similar to (HashiCorp Vault)
我们将设置一个简单的spring boot应用程序并将其部署到Google AppEngine。 借助Spring Boot AutoConfiguration的强大功能,我们实际上不需要编写任何代码即可访问这些机密。 相反,通过几行配置,我们可以自动访问我们的秘密,从而提供与( HashiCorp Vault )类似的无缝集成
授予应用程序访问权限 (Granting application access)
For application to access these secrets, first we need to grant permission to its service account.
为了使应用程序访问这些机密,首先,我们需要为其服务帐户授予权限。
For AppEngine, a default service account is created with the format {PROJECT_ID}@appspot.gserviceaccount.com. For a compute engine, GKE or another environment, you need to create a new service account.
对于AppEngine,将使用{ PROJECT_ID }@appspot.gserviceaccount.com格式创建默认服务帐户。 对于计算引擎,GKE或其他环境, 您需要创建一个新的服务帐户 。
To access the secret, the service account should have roles/secretmanager.secretAccessor IAM Permission. Depending on the security requirement you can assign this role at two levels,
要访问机密,服务帐户应具有roles/secretmanager.secretAccessor IAM权限。 根据安全要求,您可以在两个级别上分配此角色,
Project level, so the application can access all the secrets within the GCP project (less restrictive if all secrets aren’t for this service)
专案层级 ,因此应用程式可以存取GCP专案中的所有机密(如果并非所有机密,则限制较少)
Secret level, for each secret you can add the service account with accessor role, it is a repetitive action if you have many secrets but offers fine-grained security.
机密级别 ,对于每个机密,您可以添加具有访问者角色的服务帐户,如果您有许多机密但提供细粒度的安全性,则这是重复的操作。
For the purpose of this demo, we will be granting accessor role to the AppEngine default service account at the project level, Go to IAM & Admin -> IAM page and search for the AppEngine default service account, add the role SecretManager -> Secret Manager Secret Accessor ,
就本演示而言,我们将在项目级别为AppEngine默认服务帐户授予访问者角色,转到IAM & Admin -> IAM SecretManager -> Secret Manager Secret Accessor IAM & Admin -> IAM页面并搜索AppEngine默认服务帐户,添加角色SecretManager -> Secret Manager Secret Accessor ,

Okay, we have the secrets and added the necessary permission for our application. Let's build a demo app.
好的,我们有秘密,并为我们的应用程序添加了必要的权限。 让我们构建一个演示应用程序。
演示申请 (Demo Application)
Create a spring boot application using the Spring Initializer website,
使用Spring Initializer网站创建Spring Boot应用程序,

We have added the following dependencies,
我们添加了以下依赖项,
spring-cloud-gcp-starter — useful to bootstrap different gcp modules.
spring-cloud-gcp- starter-引导不同的gcp模块很有用。
spring-cloud-gcp-starter-secretmanager — bootstrap secret manager configurations.
spring-cloud-gcp-starter-secretmanager —引导秘密管理器配置。
appengine-maven-plugin — used to deploy the application to AppEngine.
appengine-maven-plugin-用于将应用程序部署到AppEngine。
组态 (Configuration)
The secret manager starter library offers spring bootstrap configurations to load GCP secrets into application properties. In the src/main/resources/bootstrap.yml file,
秘密管理器入门库提供了弹簧引导程序配置,以将GCP秘密加载到应用程序属性中。 在src/main/resources/bootstrap.yml文件中,
secretmanager.enabled — is used to enable/disable auto-configuration for the secret manger, useful for local development.
secretmanager.enabled —用于为秘密管理器启用/禁用自动配置,对本地开发很有用。
secretmanager.bootstrap.enabled — is used to load the GCP secrets as an application source.
secretmanager.bootstrap.enabled —用于加载GCP机密作为应用程序源。
secretmanager.secret-name-prefix — this is used by the bootstrap service to only load secret whose property name has this prefix. Useful to distinguish between GCP secrets and other secrets.
secretmanager.secret-name-prefix —引导服务使用它来仅加载其属性名称带有此前缀的密钥。 有助于区分GCP机密和其他机密。
GCP_SECRETS_ENABLED — is the environment variable that is used to enable/disable secret manager service.
GCP_SECRETS_ENABLED —是用于启用/禁用机密管理器服务的环境变量。
That's it, now you can use the GCP secrets in the application properties. Here I am using Spring Profiles to have two profile settings, one for prod which has the secret manager enabled and one fordefault without the secret manager, for local development. In application-prod.yml
就是这样,现在您可以在应用程序属性中使用GCP密码了。 在这里,我使用Spring Profiles进行两个配置文件设置,一个用于启用了秘密管理器的prod ,另一个用于本地开发的不带秘密管理器的default 。 在application-prod.yml
As you can see, googleClientId & googleClientSecret takes the value from GCP secrets whose name has the prefix gcp-secrets. , which will be loaded by the secret manager service.
如您所见, googleClientId和googleClientSecret从名称为gcp-secrets.前缀的GCP密钥中获取值gcp-secrets. ,它将由机密管理器服务加载。
使用秘密 (Using Secrets)
Now, we can use the @ConfigurationProperties to load these secrets into our code, notice the prefix app.secrets it should match with the application.yml configuration.
现在,我们可以使用@ConfigurationProperties将这些秘密加载到我们的代码中,请注意前缀app.secrets应该与application.yml配置匹配。
And also create a simple Controller to make sure all the setup is working fine,
并创建一个简单的Controller以确保所有设置都能正常运行,
For the final touch, add the app engine app.yml configuration to deploying the application, we have added the environment variables to specify the spring active profile and to enable the Secret Manage service for prod ,
最后,将App Engine app.yml配置添加到部署应用程序中,我们添加了环境变量以指定spring活动配置文件并为prod启用Secret Manage服务,
Deploy your application using the maven goal,
使用Maven目标部署您的应用程序,
mvn clean package appengine:deploy \
-Dapp.deploy.projectId=GCP_PROJECT \
-Dapp.deploy.version=VERSIONVoilà, we now have a production application accessing the secrets using Google Secret Manager, without any boilerplate code,
Voilà,我们现在有了一个生产应用程序,可以使用Google Secret Manager访问机密信息,而无需任何样板代码,

稽核 (Auditing)
As usual with any other GCP services, every action performed on the secrets are added to the audit logs, provides complete traceability for changes made to a secret,
与任何其他GCP服务一样,对机密执行的每项操作都会添加到审核日志中,从而为对机密所做的更改提供完全的可追溯性

The complete code sample is available in the GitHub repo,
完整的代码示例可在GitHub存储库中找到,
结论 (Conclusion)
Properly managing and accessing secrets is very critical for every application and doing it right has always been difficult in the Google cloud platform but not more, and I think Secret Manager is a lifesaver in this regard. And now we can manage secrets like a Pro without needing a workaround solution. I highly recommend giving it a try.
正确地管理和访问机密对于每个应用程序都是至关重要的,而在Google云平台上正确地做到这一点一直很困难,但没有更多,我认为Secret Manager在这方面是一个救命稻草。 现在,我们可以像Pro一样管理机密信息,而无需解决方法。 我强烈建议尝试一下。
微信小程序secret







 本文介绍如何借鉴专业方法,通过Google Secret Manager来安全管理微信小程序的应用秘密,确保Python和Java后端的安全集成。
本文介绍如何借鉴专业方法,通过Google Secret Manager来安全管理微信小程序的应用秘密,确保Python和Java后端的安全集成。














 1035
1035

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








