个人阅读笔记,如有错误欢迎指出
会议:AAAI 2024 Beyond Traditional Threats: A Persistent Backdoor Attack on Federated Learning| Proceedings of the AAAI Conference on Artificial Intelligence
问题:
后门容易被联邦中的良性更新稀释,持久性差
灾难性遗忘解释了后门稀释
创新:
提出了一种新的度量来量化被削弱的后门程度
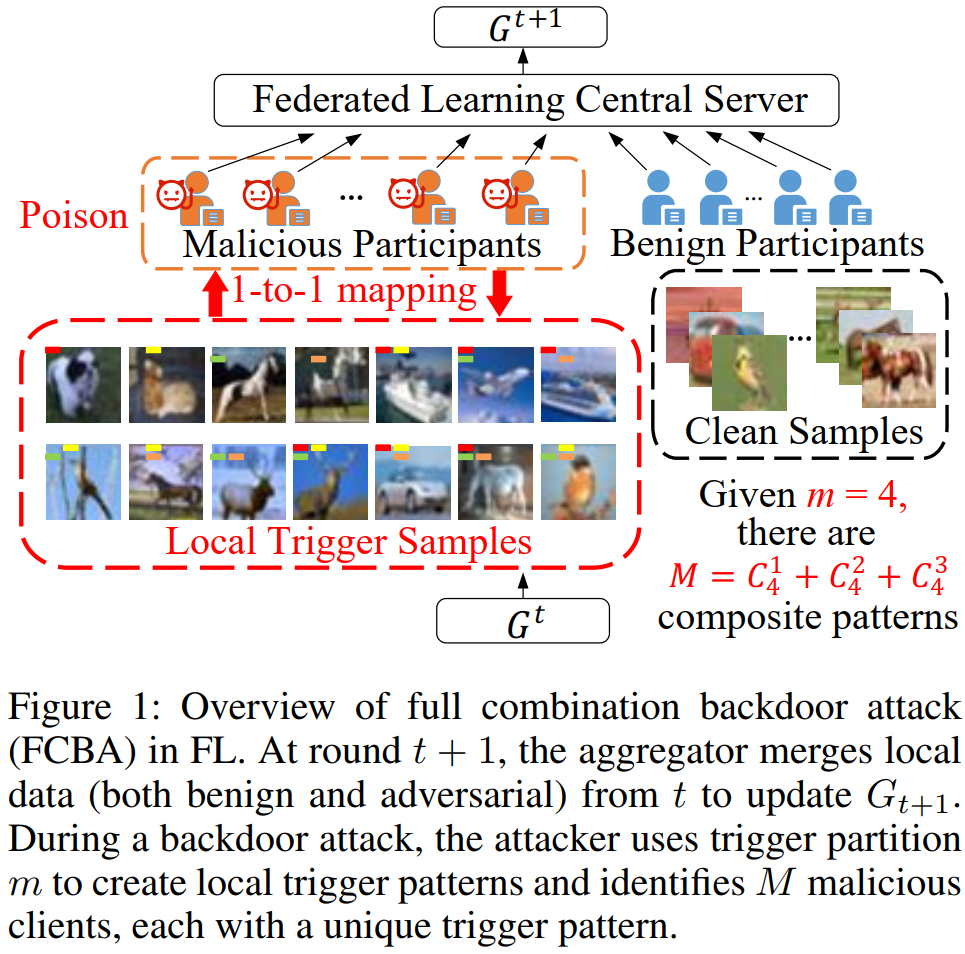
提出全组合后门攻击,聚合了更多的组合触发信息
方法:
攻击者能力:与DBA设置相同,可以完全控制受害的本地模型修改超参数。触发器使用白色像素块(占图像2%),左上角。
训练过程采用模型替换方法,优化local epoch和学习率以优化后门,以确保后门在平均聚合中幸存
本文方法:1)生成完整的组合触发器 2)恶意客户端数量计算 3)设计目标函数
1)生成组合触发器
给定一个触发器分区数,全局触发器被划分为
个不同的部分,这些部分被视为单元,通过不同样式的组合来生成局部触发器。(训练阶段本地模型使用组合的trigger,测试阶段使用全局trigger)
需要大于等于2但不能过大,
表示集中式攻击,过大的
将导致局部触发器极小影响后门效果增加计算量。
2)恶意客户端数量计算
每个恶意客户端使用唯一的本地触发器,恶意客户端的总数与本地触发器的总数相对应
当式4中的两个变量都为1时,简化为式5,将该式反过来得到组合数的和,可以此确定恶意客户端的数量。(如若触发器被划分为4各区域,即m=4m=4,则共有14个恶意客户端)
3)设计目标函数
考虑到恶意客户端和本地触发器之间的直接映射,每个本地模型都可以成为唯一的后门攻击目标。因此可将FCBA划分为个子攻击问题,第t轮第i个攻击者目标标签为
的对抗目标如下。函数
将后门样本输出到对应标签
实验:
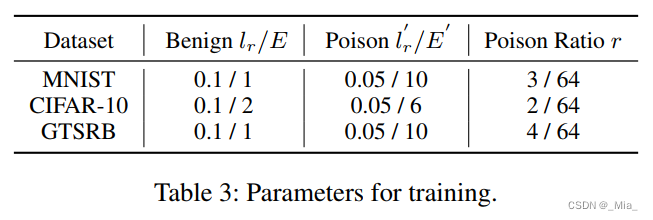
使用超参数为0.5的Dirichlet分布将图像分配给100个客户端,每轮选10个客户端提交本地更新。
触发器:MNIST
,CIFAR & GTSRB
后门学习率投毒率如下。采用single-shot攻击,放大恶意更新
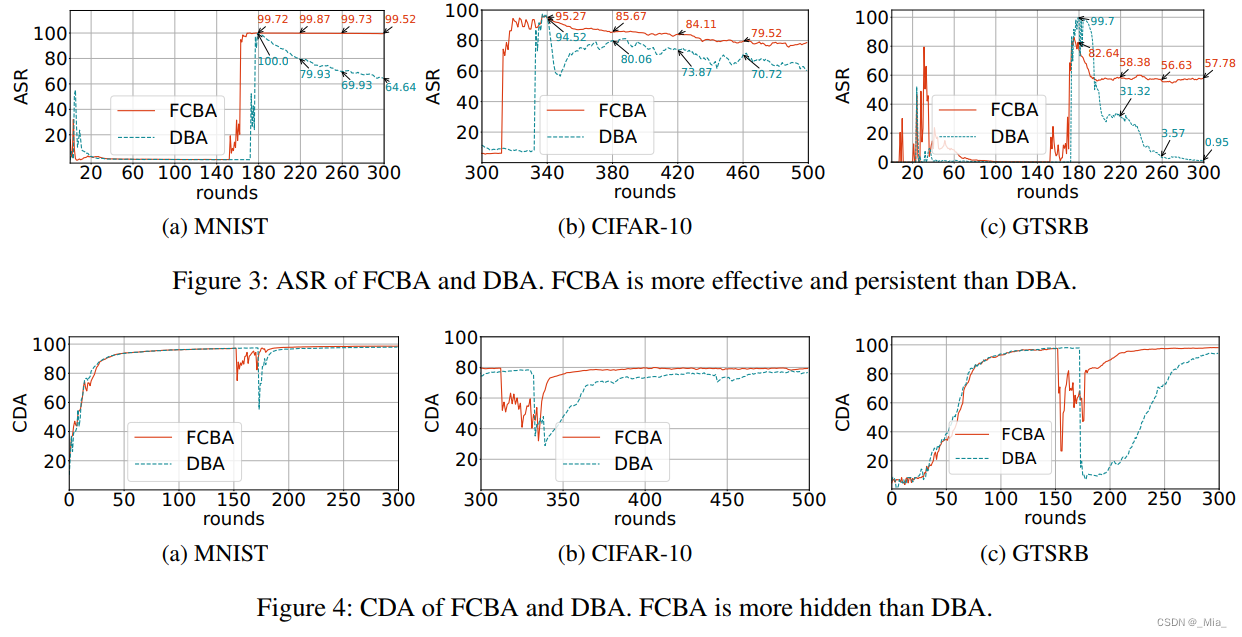
投毒后随着时间后门存活率(后门成功率)以及干净样本准确率
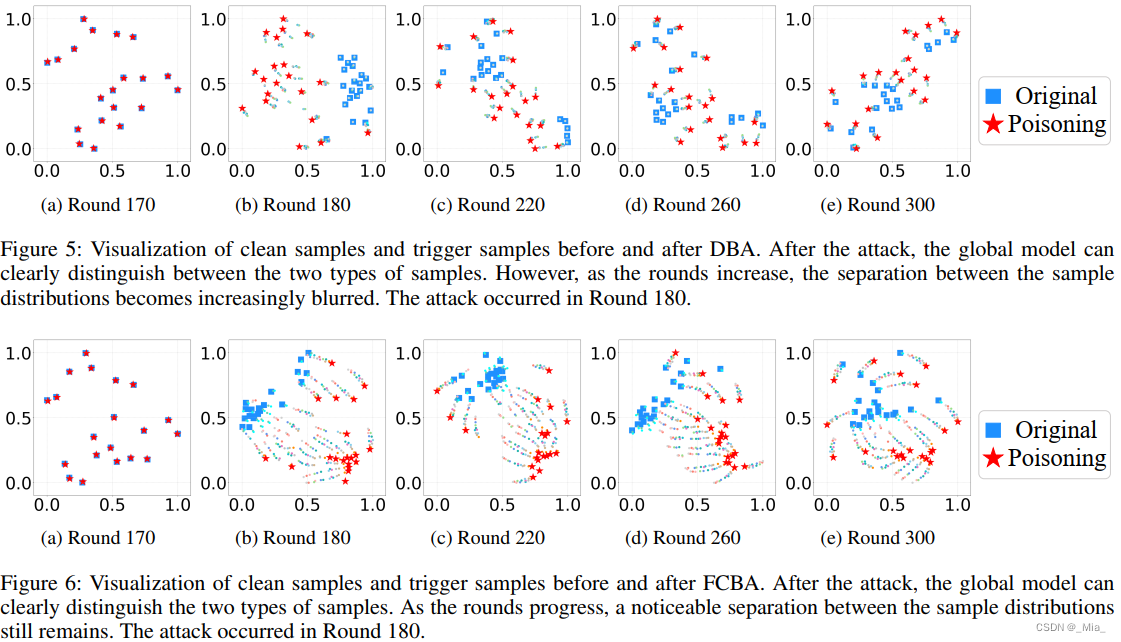
可视化MNIST “3”干净样本和20个后门样本的数据分布。图5显示随着回合的增多,DBA模糊了后门与干净样本。图6显示在FCBA中,干净样本与后门样本之间有明显的界限
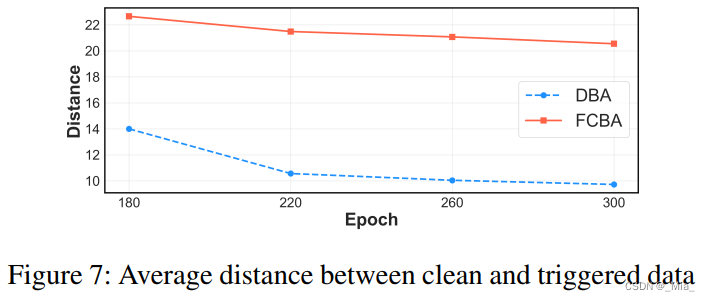
干净与目标样本分别与其在测试集中的t-SNE距离,与DBA相比FCBA的t-SNE距离更大,表明FCBA区分干净样本和后门样本的能力更强(更高的攻击持久性)
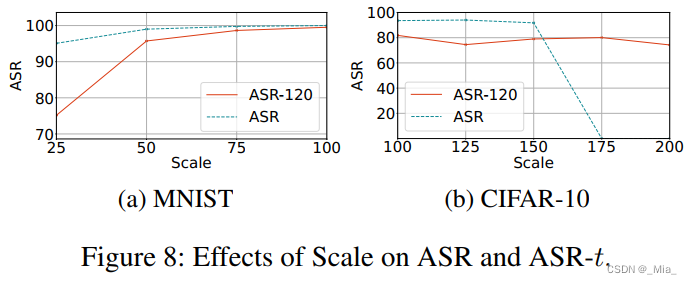
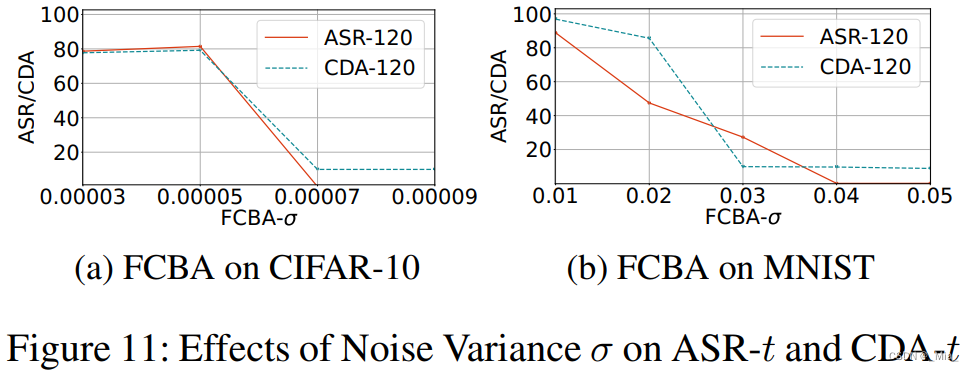
缩放因子消融
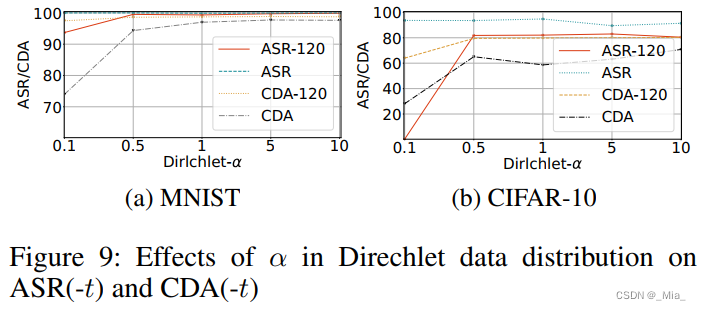
异质性消融
裁剪边界防御下的效果
差分隐私防御下的效果
总结
排列组合版的DBA,创新相对较弱,但是实验很充分,可以借鉴实验安排。
已有的研究证明通过放大恶意更新很容易通过比较更新方向检测出来,本文通过对恶意更新进行了放大,但并未比较在基于过滤的后门防御方法。







 文章探讨了在FederatedLearning中,通过提出新的度量和全组合后门攻击,增强后门攻击的持久性。研究者生成组合触发器并设计目标函数,实验证明了这种新型攻击方法在保持后门效果的同时提高了对检测的挑战。
文章探讨了在FederatedLearning中,通过提出新的度量和全组合后门攻击,增强后门攻击的持久性。研究者生成组合触发器并设计目标函数,实验证明了这种新型攻击方法在保持后门效果的同时提高了对检测的挑战。
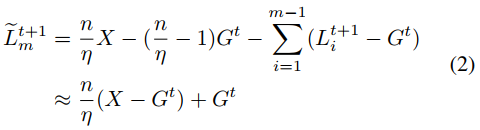
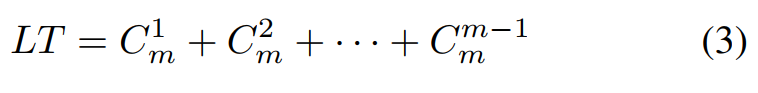
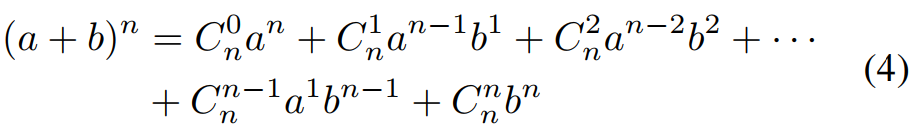
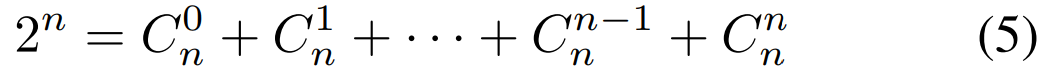
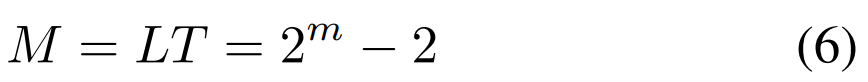
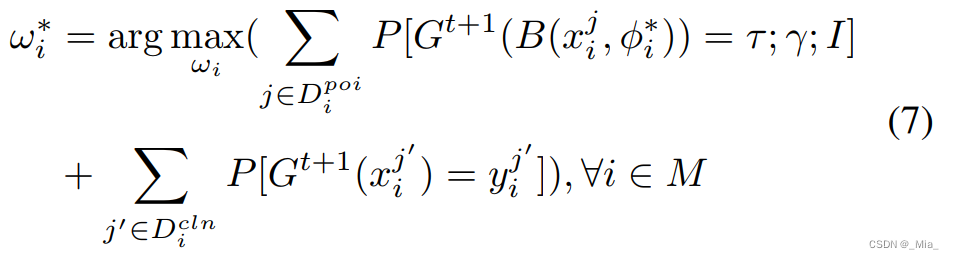
















 821
821

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








