使用frp实现内网穿透
引言
一打五师兄走之前留了一块树莓派给我,暑假闲来无事拿出来玩玩
如果每次都连接显示屏和键盘使用有点麻烦而且低级
正常笔记本和树莓派都连着实验室的WIFI,网段一样,是可以ssh远程登录的
但我突然想到在家里连着家里的WIFI能不能也登录进树莓派呢
问题有了,开始干吧
内网穿透初步
正常来说两台Linux设备只有在同一局域网下才可以进行互相的ssh远程登录
那么如果不在一个网段下,比方说一台在家里连着家里的WIFI,一台在学校连着实验室的WIFI,这种情况要想实现ssh远程登录则需要用到内网穿透
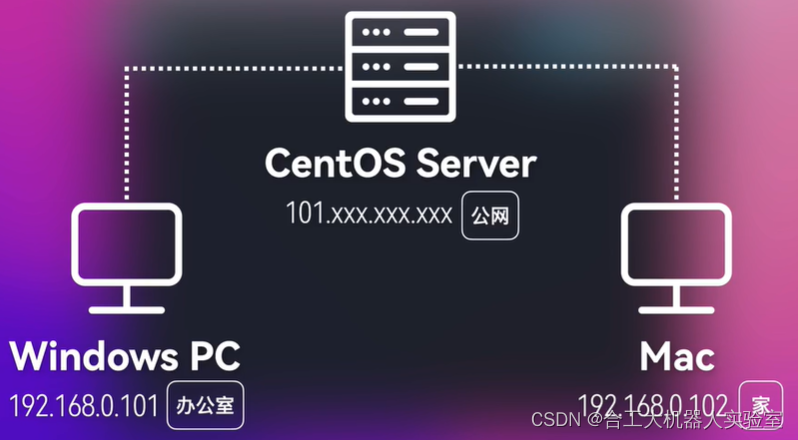
这就需要用到一个开源框架frp
https://github.com/fatedier/frp
在这里下载与主机架构对应的版本
查看安装的Linux架构/版本
cat /proc/version
prejudice@prejudice-VirtualBox:~$ cat /proc/version
Linux version 5.4.0-122-generic (buildd@lcy02-amd64-035) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #138~18.04.1-Ubuntu SMP Fri Jun 24 14:14:03 UTC 2022
[lighthouse@VM-4-11-centos ~]$ cat /proc/version
Linux version 4.18.0-348.7.1.el8_5.x86_64 (mockbuild@kbuilder.bsys.centos.org) (gcc version 8.5.0 20210514 (Red Hat 8.5.0-4) (GCC)) #1 SMP Wed Dec 22 13:25:12 UTC 2021
学习视频
其实B站搜frp就有很多
学习文档
官网给了教程,实在是很贴心
运行下述命令的时候
ssh -oPort=6000 test@x.x.x.x
中间-oPort=6000实际上可以简化为-p 6000
这里的端口是公网用于listen的端口,frp 会将请求 x.x.x.x:6000 的流量转发到内网机器的 22 端口,因此这里x.x.x.x也是公网IP
服务端有两个端口,一个负责接收客户端的连接,一个负责监听与流量转发,有点类似于TCP通信的connectfd和listenfd ,实际上也是基于TCP通信实现的
因此需要在云服务器上打开两个端口的防火墙

简单实操
云服务器端
运行服务端程序
[lighthouse@VM-4-11-centos frp_0.44.0_linux_amd64]$ ./frps -c ./frps.ini
2022/07/21 21:18:23 [I] [root.go:209] frps uses config file: ./frps.ini
2022/07/21 21:18:23 [I] [service.go:194] frps tcp listen on 0.0.0.0:7000
2022/07/21 21:18:23 [I] [root.go:218] frps started successfully
笔记本端运行./frpc -c ./frpc.ini 后,新建个登录窗口
[lighthouse@VM-4-11-centos /]$ ssh -p 6000 redwall@1.116.137.21
redwall@1.116.137.21's password:
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 5.4.0-122-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 updates can be applied immediately.
New release '20.04.4 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Your Hardware Enablement Stack (HWE) is supported until April 2023.
Last login: Thu Jul 21 17:05:31 2022 from 192.168.1.137
redwall@redwall-G3-3500:~$
看到已经成功远程登录,可以进行相关操作了
redwall@redwall-G3-3500:~$ ls
catkin_ws CUDA_Samples Test 公共的 模板 视频 图片 文档 下载 音乐 桌面
redwall@redwall-G3-3500:~$ pwd
/home/redwall
注意到客户端连接时会提示
2022/07/21 21:30:39 [I] [service.go:450] [f4703ace8f5e3c8f] client login info: ip [114.213.236.99:47292] version [0.44.0] hostname [] os [linux] arch [amd64]
2022/07/21 21:30:39 [I] [tcp.go:64] [f4703ace8f5e3c8f] [ssh] tcp proxy listen port [6000]
2022/07/21 21:30:39 [I] [control.go:465] [f4703ace8f5e3c8f] new proxy [ssh] type [tcp] success
有远程登录时会提示
2022/07/21 21:31:01 [I] [proxy.go:179] [f4703ace8f5e3c8f] [ssh] get a user connection [1.116.137.21:52368]
退出ssh远程登录时会提示
2022/07/21 21:28:31 [I] [control.go:307] [a1a79c2d05ad0fae] control writer is closing
2022/07/21 21:28:31 [I] [proxy.go:88] [a1a79c2d05ad0fae] [ssh] proxy closing
2022/07/21 21:28:31 [W] [proxy.go:176] [a1a79c2d05ad0fae] [ssh] listener is closed: accept tcp [::]:6000: use of closed network connection
2022/07/21 21:28:31 [I] [control.go:396] [a1a79c2d05ad0fae] client exit success
还是非常人性化的
笔记本端
打开终端查看网络信息
redwall@redwall-G3-3500:~$ ifconfig
enp59s0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 8c:47:be:3b:dd:d2 txqueuelen 1000 (以太网)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (本地环回)
RX packets 1351 bytes 123182 (123.1 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1351 bytes 123182 (123.1 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlp0s20f3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.137 netmask 255.255.255.0 broadcast 192.168.1.255
inet6 fe80::5348:35ba:d99a:6366 prefixlen 64 scopeid 0x20<link>
ether ac:12:03:c9:3a:01 txqueuelen 1000 (以太网)
RX packets 11079 bytes 12274960 (12.2 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 3983 bytes 509254 (509.2 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
简单配置frpc.ini
[common]
server_addr = 1.116.137.21
server_port = 7000
[ssh]
type = tcp
local_ip = 192.168.1.137
local_port = 22
remote_port = 6000
打开一个终端运行
redwall@redwall-G3-3500:~/Test/frp_0.44.0_linux_amd64$ ./frpc -c ./frpc.ini
2022/07/21 21:19:06 [I] [service.go:349] [a1a79c2d05ad0fae] login to server success, get run id [a1a79c2d05ad0fae], server udp port [0]
2022/07/21 21:19:06 [I] [proxy_manager.go:144] [a1a79c2d05ad0fae] proxy added: [ssh]
2022/07/21 21:19:06 [I] [control.go:181] [a1a79c2d05ad0fae] [ssh] start proxy success
在树莓派配置frp框架
由于树莓派只有2GB的RAM,因此安装的是Ubuntu 18.04 Bionic Beaver
一开始cat /proc/version查看是arm64,因此就在frp Release中下载的arm64版本
实际中会报错cannot execute binary file
原因是程序所需架构与系统不匹配,想起来当时安装的是32位的server,所以换了Release下的arm版本,成功运行
SSH时出现WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!
问题解决——SSH时出现WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!
WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!
翻译过来就是
警告:远程主机标识已更改!
此报错是由于远程的主机的公钥发生了变化导致的
ssh服务是通过公钥和私钥来进行连接的,它会把每个曾经访问过计算机或服务器的公钥(public key),记录在~/.ssh/known_hosts 中,当下次访问曾经访问过的计算机或服务器时,ssh就会核对公钥,如果和上次记录的不同,OpenSSH会发出警告
直接echo >”~/.ssh/known_hosts”可以解决该问题
SSH Failed Permission Denied
这里主要是与sshd_config的配置有关
修改云服务器上的sshd_config
sudo cd /etc/ssh/
sudo cp sshd_config sshd_config_init
sudo vim sshd_config
PermitRootLogin yes
PasswordAuthentication yes
ChallengeResponseAuthentication no
对树莓派上的sshd_config进行同样的修改,不过多一个内容
AddressFamily any
成功解决问题
Linux域名IP映射
进行域名IP映射是为了便于连接时的操作,不然还需要记住一长串IP地址,太麻烦了
sudo vim /etc/hosts
# CentOS
x.x.x.x centos
# Raspberry Pi
x.x.x.x raspberry
设置frp开机自启
创建service服务文件
cd /etc/systemd/system/
sudo touch frpc.service
sudo vim frpc.service
文件内容如下
[Unit]
Description=Frp Client
After=network.target
Wants=network.target
[Service]
Type=simple
User=ubuntu
Restart=on-failure
RestartSec=5
ExecStart=/home/ubuntu/frpc_client -c /home/ubuntu/frpc.ini
[Install]
WantedBy=multi-user.target
这里User是你的用户名,ExecStart是执行文件的地址,更改这两处即可
刷新服务列表
systemctl daemon-reload
设置开机自启
systemctl enable frpc.service
实际效果
首先在云服务器上运行
[root@VM-4-11-centos frp_server]# ./frps -c ./frps.ini
2022/07/22 15:45:25 [I] [root.go:209] frps uses config file: ./frps.ini
2022/07/22 15:45:25 [I] [service.go:194] frps tcp listen on 0.0.0.0:7000
2022/07/22 15:45:25 [I] [root.go:218] frps started successfully
树莓派通电开机后,云服务器终端显示
2022/07/22 15:46:02 [I] [service.go:450] [192daaa5a29e5228] client login info: ip [114.213.236.99:54242] version [0.44.0] hostname [] os [linux] arch [arm]
2022/07/22 15:46:02 [I] [tcp.go:64] [192daaa5a29e5228] [ssh] tcp proxy listen port [6000]
2022/07/22 15:46:02 [I] [control.go:465] [192daaa5a29e5228] new proxy [ssh] type [tcp] success
可以看到树莓派已经自动连接到云服务器
打开笔记本和手机热点,笔记本连接手机热点,使得笔记本和树莓派连接不同的WIFI
在笔记本终端运行
redwall@redwall-G3-3500:~/frp_client$ ./frpc -c ./frpc.ini
2022/07/22 15:46:31 [I] [service.go:349] [41273076a0105bd8] login to server success, get run id [41273076a0105bd8], server udp port [0]
2022/07/22 15:46:31 [I] [proxy_manager.go:144] [41273076a0105bd8] proxy added: [ssh]
此时云服务器终端提示
2022/07/22 15:46:31 [I] [service.go:450] [41273076a0105bd8] client login info: ip [39.144.38.10:42468] version [0.44.0] hostname [] os [linux] arch [amd64]
说明笔记本也连上了云服务器,并且明显可以看出笔记本和树莓派连着不同的WIFI
这时在笔记本新建一个终端,运行
redwall@redwall-G3-3500:~$ ssh -p 6000 ubuntu@centos
ubuntu@centos's password:
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 5.4.0-1066-raspi armv7l)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Jul 22 07:47:21 UTC 2022
System load: 1.18 Processes: 138
Usage of /: 37.9% of 14.28GB Users logged in: 0
Memory usage: 5% IP address for wlan0: 192.168.1.111
Swap usage: 0%
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
0 updates can be applied immediately.
New release '20.04.4 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Your Hardware Enablement Stack (HWE) is supported until April 2023.
Last login: Fri Jul 22 07:40:35 2022
ubuntu@ubuntu:~$ ls
catkin_ws frp_client
ubuntu@ubuntu:~$ pwd
/home/ubuntu
ubuntu@ubuntu:~$
可以看到已经成功实现在不同网段下Linux主机间的ssh远程登录
后面就可以进行愉快的编程开发啦





















 493
493











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








