默克尔树
Ralph C. Merkle (not pictured above), born 1952, is one of the founding fathers of Public Key Cryptography. Throughout his career he has developed and contributed to a list of monumental cryptographic systems, some of which are embedded in the backbone of the online protocols and applications we rely on in daily life. In this post we will look at his work on Merkle Trees, how they function, and why and how they are growing in use.
拉尔夫·默克尔(Ralph C. Merkle)(上图中未画)出生于1952年,是公钥密码学的创始人之一。 在他的整个职业生涯中,他已经开发并贡献了一系列重要的密码系统,其中一些嵌入了我们日常生活所依赖的在线协议和应用程序的主干中。 在这篇文章中,我们将研究他在Merkle Trees上的工作,它们的功能以及使用原因和增长方式。
默克尔_What_ (Merkle _What_)
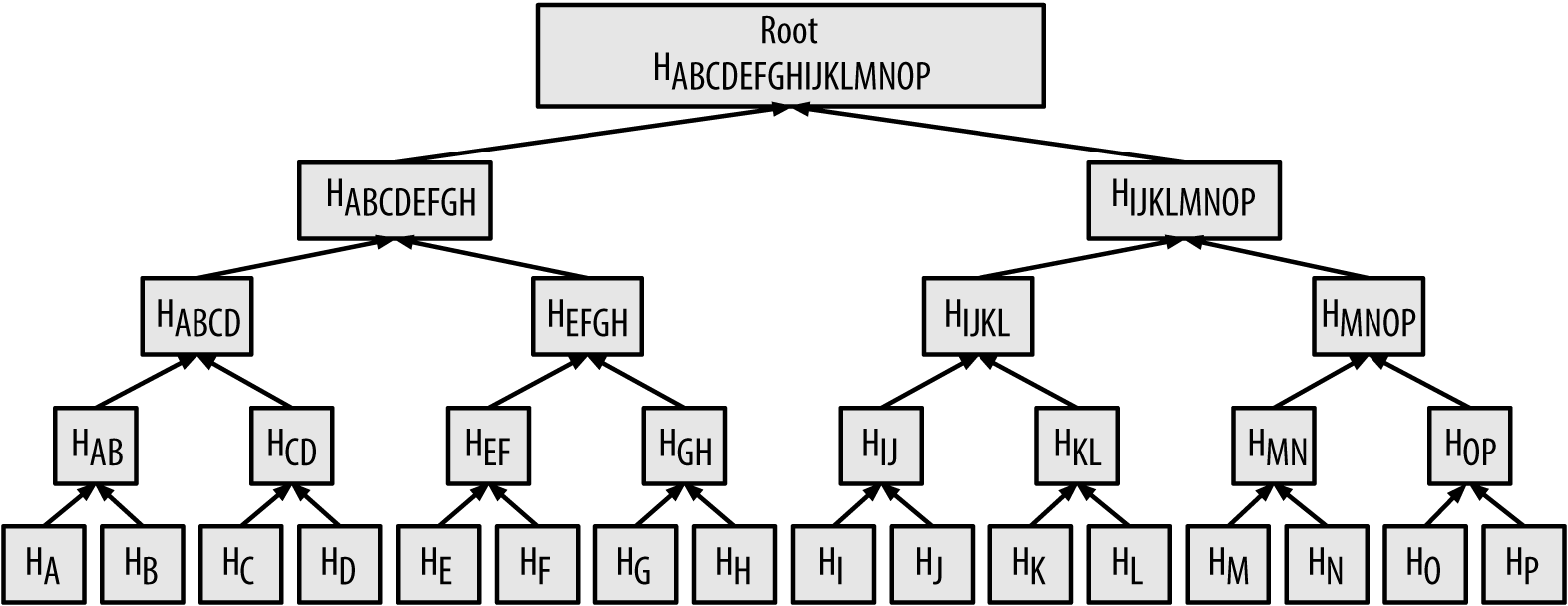
The overall structure of a Merkle Tree is quite simple and is very familiar to computer scientists: a tree data structure. Data trees have one root node (the main file or piece of data) which is then divided or branched out into child nodes — in this case exactly one or two. By branching out again, these children then become parent nodes to subsequent children and so on. The final child node of any branch is called a leaf node. In reverse, each leaf node in combination with its sibling node (should it have one) yields its parent node and so on, until the original root node is reconstructed.
Merkle树的整体结构非常简单,计算机科学家对此非常熟悉: 树数据结构 。 数据树具有一个根节点 (主文件或数据段),然后将其划分或分支为子节点 -在这种情况下,恰好是一个或两个。 通过再次分支,这些子项将成为后续子项的父节点 ,依此类推。 任何分支的最后一个子节点称为叶节点 。 相反,每个叶节点与其同级节点 (应该有一个)结合在一起,产生其父节点,依此类推,直到重建原始根节点为止。
Merkle Trees differ from traditional data trees in one simple way: they use cryptographic hashes of each piece of data rather than the data itself. From leaf nodes up to the root, the process works as such:
默克尔树与传统数据树的区别仅在于一种简单的方式:它们使用每个数据的加密哈希而不是数据本身。 从叶节点到根,该过程的工作方式如下:
- Each leaf node is hashed 每个叶节点都经过哈希处理
Moving up the tree towards the root, each leaf or child hash is XOR’d (cryptographically combined) with the hash of its sibling node
将树向上移到根,每个叶子或子哈希与它的同级节点的哈希进行异或(加密组合)
Finally, the hash of the the top parent nodes are XOR’d into the root node which precisely equals the aggregate hash of the original piece of data
最后,将顶级父节点的哈希值与根节点进行XOR运算,该根节点恰好等于原始数据的总哈希值

默克尔_为什么_ (Merkle _Why_)
For many years Merkle Trees were little more than a cryptographic magic trick. But as is common with mathematical and computational breakthroughs, years later it began to play a critical roll in various protocols and software projects. Merkle Trees are mainly used for two reasons:
多年以来,默克尔树只不过是一种加密魔术。 但是,与数学和计算突破一样,几年之后,它开始在各种协议和软件项目中发挥关键作用。 使用默克尔树主要有两个原因:
- They allow a client or server to efficiently validate the contents of large files/data 它们允许客户端或服务器有效地验证大文件/数据的内容
- They allow a client or server to validate any segment or sub-segment of the file/data without possessing any other segments 它们允许客户端或服务器验证文件/数据的任何段或子段,而无需拥有任何其他段
To understand why Merkle Trees have these properties, it is important to know a little bit about Cryptographic Hash Functions. Hash functions are easy to compute in one direction but extraordinarily hard to compute in the opposite direction. For example, the industry standard SHA-256 can be hashed in milliseconds but would theoretically take about 3.85 × 10²⁹ years to reverse, according to computer scientist Luke Dash Jr.
要了解Merkle树为何具有这些属性,重要的一点是要了解一些密码散列函数。 哈希函数易于在一个方向上计算,但在相反方向上却很难计算。 例如,根据计算机科学家Luke Dash Jr的说法,行业标准SHA-256可以以毫秒为单位进行哈希处理,但是从理论上讲,反向转换大约需要3.85×10²⁹年。
In the case of Merkle Trees, the hash function is used to calculate the hash of each segment of data which becomes the leaf nodes, then XOR each leaf node with sibling leaf/child nodes into parent nodes and so on, all the way up to the root node or Merkle Root. If each segment of the data is in tact and unchanged, the Merkle Root is exactly equal to the aggregate hash of the entire file or piece of data. If even one bit of information is changed in any segment, the hash is completely different which propagates up the tree, resulting in an entirely different Merkle Root. This root can then be compared with the actual/desired root and thus any inconsistency is detected.
对于Merkle树,哈希函数用于计算成为叶节点的每个数据段的哈希,然后将每个叶节点与同级叶/子节点异或为父节点,依此类推,直到根节点或Merkle Root 。 如果数据的每个段均完整无缺,则默克根(Merkle Root)完全等于整个文件或数据片段的总哈希值。 如果在任何段中甚至改变了一点信息,散列就完全不同,并沿树传播,从而导致完全不同的Merkle根。 然后可以将此根与实际/所需的根进行比较,从而检测到任何不一致之处。
“These numbers have nothing to do with the technology of the devices, they are the maximums that thermodynamics will allow. They strongly imply that brute-force attacks against 256-bit keys will be infeasible until computers are built from something other than matter and occupy something other than space.”
这些数字与设备的技术无关,它们是热力学允许的最大值。 他们强烈暗示,对256位密钥进行强力攻击将是不可行的,除非计算机是用物质以外的东西建造的并且占用空间以外的东西。”
— Bruce Schneier, Cryptographer
—密码学家Bruce Schneier
默克尔_How_ (Merkle _How_)
One important use of Merkle Trees is in downloading files. If a user/client attempts to download a large file all at once and something goes wrong, the entire file can be corrupted and the full download process would need to be restarted. Using Merkle Trees, the user can download a smaller segment of the data and hash it. By combining this hash with the hashes of each other segment (trivially small to download/check compared to the data itself), they can check to see if any data was corrupted during the download process. These steps continue for each segment such that if the Merkle Root doesn’t match up at any step during the download process, they know which segment of the data was corrupted. It is important to note that this process takes place automatically in the background and does not require any action from the actual user.
Merkle树的一项重要用途是下载文件。 如果用户/客户端尝试一次全部下载一个大文件而出现问题,则整个文件可能会损坏,并且需要重新启动完整的下载过程。 使用Merkle树,用户可以下载较小部分的数据并对其进行哈希处理。 通过将此哈希与其他每个段的哈希值组合在一起(与数据本身相比,下载/检查的哈希值很小),他们可以检查以查看在下载过程中是否有数据损坏。 这些步骤针对每个段继续进行,这样,如果Merkle根在下载过程中的任何步骤都不匹配,则它们知道数据的哪个段已损坏。 重要的是要注意,此过程在后台自动进行,不需要实际用户采取任何措施。
Another place we see Merkle Trees being used is in the Distributed Version Control System Git. Git maintains and reconciles many different versions of a piece of software as it is built, changed and updated simultaneously by many contributors. Git is both fast and secure because instead of storing and comparing every instance of the actual software, it instead stores and compares the hashes of each segment and version in the form of a Merkle Tree. Git’s implementation is slightly more complicated as it XOR’s some additional nonces along the way, but the overall structure is that of a Merkle Tree.
我们看到使用Merkle树的另一个地方是分布式版本控制系统Git中 。 当许多贡献者同时构建,更改和更新软件时,Git维护并协调该软件的许多不同版本。 Git既快速又安全,因为它没有存储和比较实际软件的每个实例,而是以Merkle树的形式存储和比较每个段和版本的哈希。 Git的实现稍微复杂一些,因为它在此过程中对XOR进行了一些附加的随机数运算,但是总体结构是Merkle Tree的结构。
Finally, Merkle Trees play a key roll in the construction of the Bitcoin blockchain. When a Bitcoin node broadcasts a transaction to the rest of the peer-to-peer network and is included in a block by a mining node, the miner hashes that Transaction ID along with every other Transaction ID in that block. Those hashes are then put into pairs and XOR’d into a new hash and so forth in the form of a tree, all the way up to the Merkle Root. The root is then XOR’d once more with some additional data pertaining to the block itself and the hash of the preceding block (forming the chain), which finally results in a new block hash. While it is impossible to infer the details any particular transaction from it, the details of all transactions in the block are needed to compute the final block hash.
最后,默克尔树(Merkle Trees)在比特币区块链的构建中发挥了关键作用。 当比特币节点将交易广播到对等网络的其余部分并被挖掘节点包含在一个区块中时,矿工会将该交易ID以及该区块中的所有其他交易ID进行哈希处理。 然后将这些哈希成对放置,并以树的形式异或为一个新的哈希,以此类推,直到Merkle Root。 然后,将根与该块本身以及前一个块的哈希(形成链)有关的一些其他数据再次进行异或运算,最终导致新的块哈希。 虽然不可能从中推断出任何特定交易的细节,但是需要块中所有交易的细节来计算最终的块哈希。

默克尔(Merkle) (Merkle _Root_)
In conclusion, Merkle Trees are a very clever way to maintain and verify databases and large files across networks of users/devices. When checked against the original Merkle Root, every piece of data must remain completely unchanged, else the roots will not align. As we live in a continuously more digital age and distributed systems gain popularity, it is likely we will start to see more Merkle Trees sprouting up in new and exciting places.
总之,Merkle树是在用户/设备网络之间维护和验证数据库和大文件的非常聪明的方法。 当对照原始的Merkle根进行检查时,每条数据都必须完全保持不变,否则根将无法对齐。 随着我们生活在一个数字化时代,分布式系统越来越受欢迎,我们很可能会开始在新的令人兴奋的地方看到更多的Merkle树。
翻译自: https://medium.com/@EricB10/merkle-trees-growing-in-usage-a7cc1ed7b2ac
默克尔树





















 1075
1075

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








