硬解密和软解码的区别
编码方式 (Encoding)
Encoding is a process of conversion of data from one format to another. It includes the utilization of a code to change unique information into a structure that can be utilized by an external application.
编码是将数据从一种格式转换为另一种格式的过程。 它包括利用代码将唯一信息更改为可由外部应用程序使用的结构。
The code utilized for changing over characters is called American Standard Code for Information Interchange (ASCII), the most commonly utilized encoding for files that contain text.
用于转换字符的代码称为美国信息交换标准代码(ASCII),这是包含文本的文件最常用的编码。
Media files such as audio and video use encoding to reduce their file size. Each audio and video file format has a corresponding coder-decoder (codec) program that is used to code it into the appropriate format and then decodes for playback. For example, converting .mp4 into .avi, .flv to .mp3 etc. would require encoding.
诸如音频和视频之类的媒体文件使用编码来减小其文件大小。 每种音频和视频文件格式都有一个对应的编解码器(codec)程序,该程序用于将其编码为适当的格式,然后进行解码以进行播放。 例如,将.mp4转换为.avi,将.flv转换为.mp3等,将需要编码。
Let’s look at type of encoding: base64
让我们看一下编码类型: base64
Base64 Encoding:
Base64编码:
It is an encoding technique used to convert binary data to an ASCII format. When we need to send binary data over media that are usually designed to handle textual data, we need to use base64. Example, sending images in an XML document or as an email attachment.
它是一种用于将二进制数据转换为ASCII格式的编码技术。 当我们需要通过通常用于处理文本数据的媒体发送二进制数据时,我们需要使用base64。 例如,以XML文档或电子邮件附件的形式发送图像。
The following figure is the base64 character index table, which is used to encode characters into base64.
下图是base64字符索引表,该表用于将字符编码为base64。
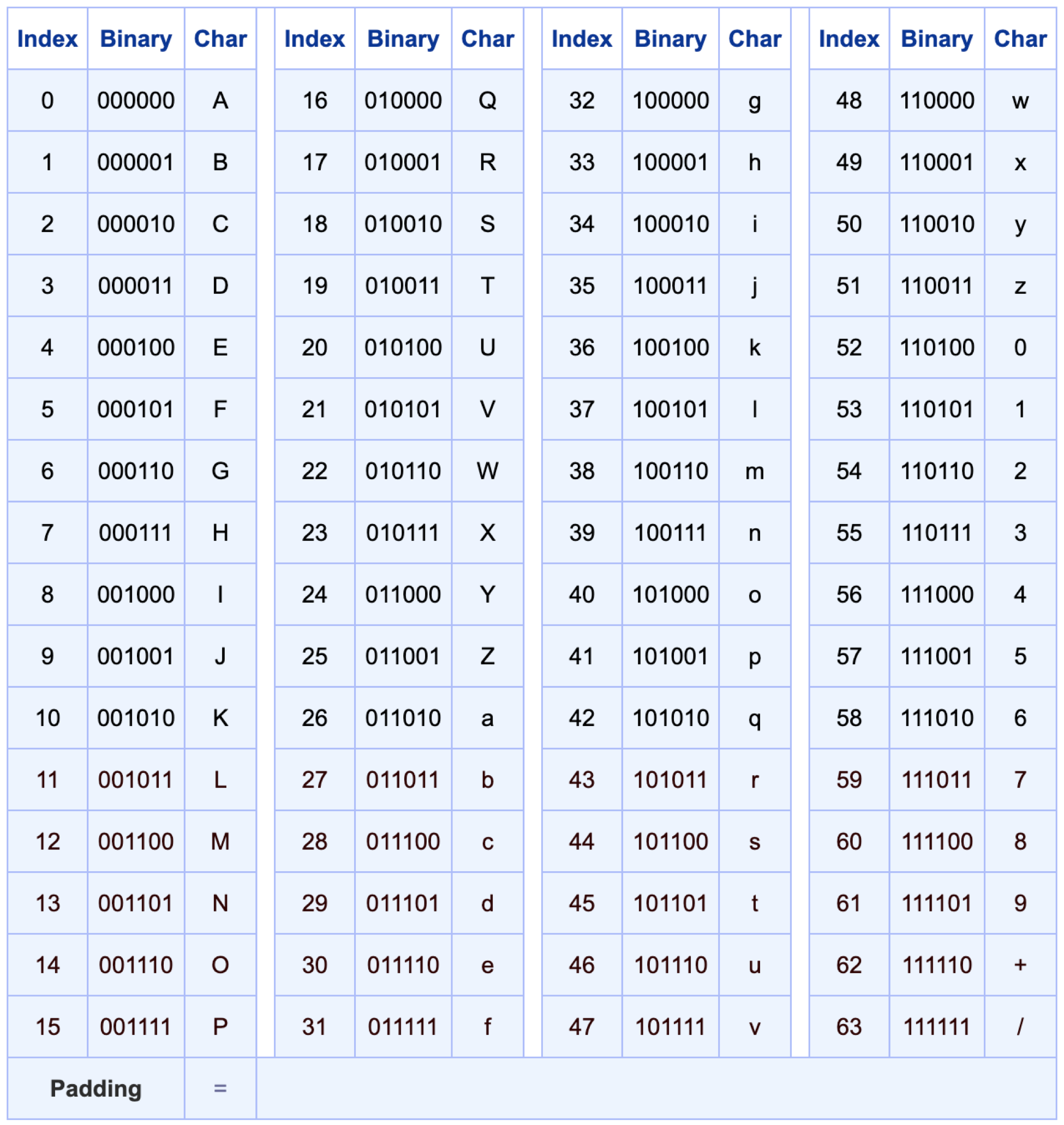
Let’s see some few examples:
让我们看一些例子:
1) And
1) 然后

Algorithm for base64 encoding:
base64编码算法:
- Convert ASCII code into octets 将ASCII码转换为八位字节
- Convert octets into sextets 将八位字节转换为六重奏
- Convert sextets into decimals 将六重音转换成小数
- Convert decimals to their equivalent characters in base64 character index table 将小数转换为base64字符索引表中的等效字符
Note: The total characters in base64 encoded text is always a multiple of 4.
注意:以base64编码的文本中的字符总数始终为4的倍数。
echo -n “And” | base64QW5k2) An
2)
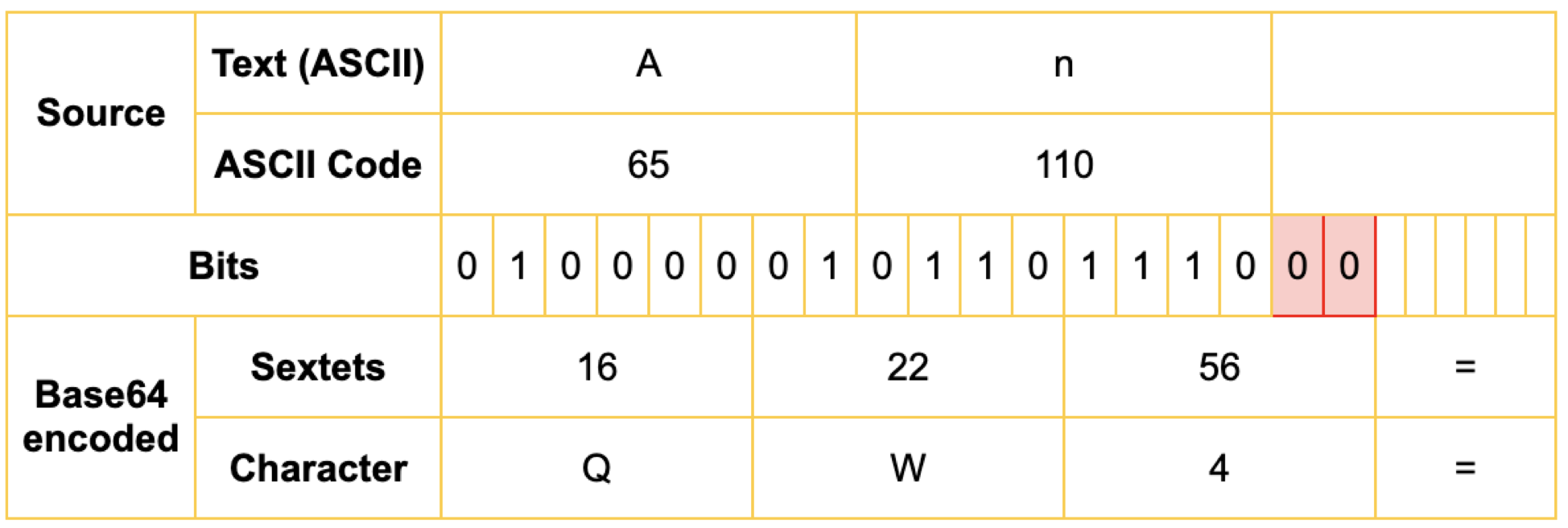
Note: The cells in the red are padded 0’s to complete the sextet. And since the total characters in the output should be multiple of 4, we pad the output with an extra ‘=’
注意 :红色的单元格用0填充以完成六重奏。 由于输出中的总字符数应为4的倍数,因此我们在输出处加上额外的'='
echo -n “An” | base64QW4=3) A
3)A
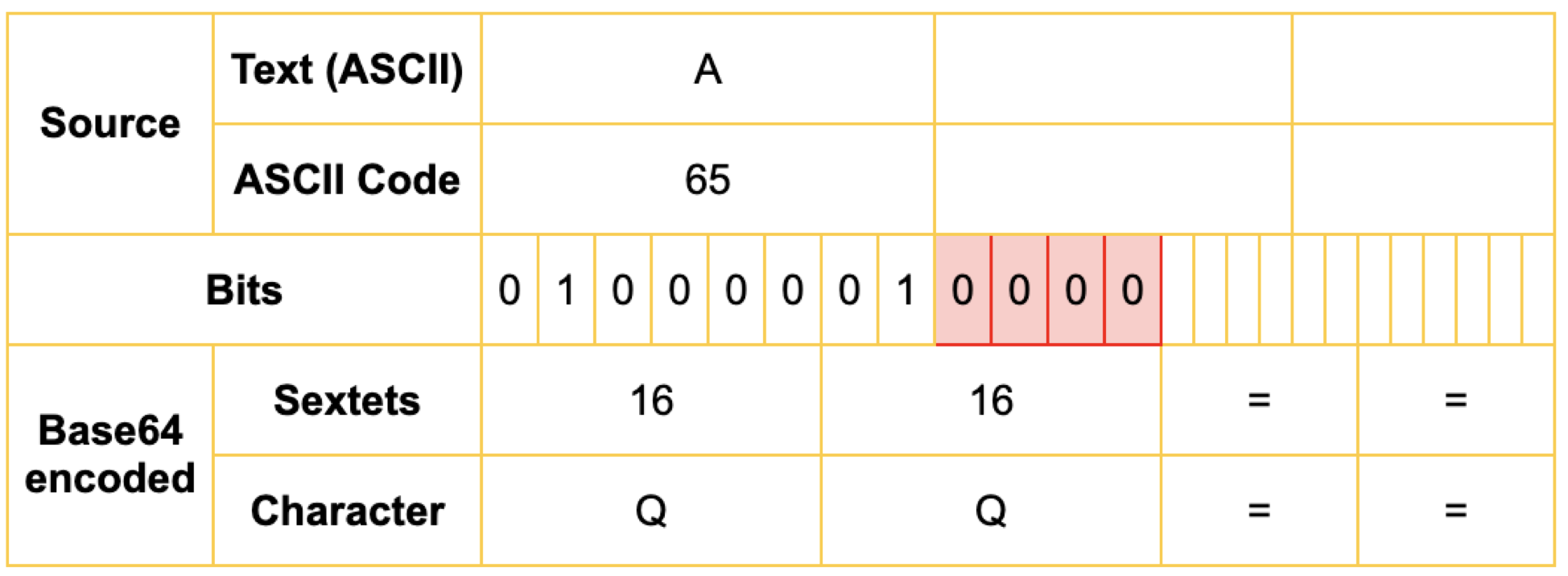
echo -n “A” | base64QQ==解码 (Decoding)
Decoding is the opposite of encoding. It is a process that converts an encoded code format back to its original code format.
解码与编码相反。 它是将编码的代码格式转换回其原始代码格式的过程。
Like in the encoding section above, the base64 encoded output can be converted back to its original text by reversing the steps.
像上面的编码部分一样,可以通过反转步骤将base64编码的输出转换回其原始文本。
Algorithm for base64 decoding:
base64解码算法:
- Convert base64 characters to their equivalent decimals index from the base64 index table 将base64字符转换为base64索引表中的等效小数索引
- Convert decimals into sextets 将小数转换为六音
- Convert sextets into octets 将六重奏转换为八位字节
- Convert octets into ASCII code 将八位字节转换为ASCII代码
加密 (Encryption)

Encryption is the process of encoding information so that only the users that have authorization can access the data. Encryption does not itself prevent interference and eavesdropping attacks, but denies intelligible content to the interceptor.
加密是对信息进行编码的过程,以便只有获得授权的用户才能访问数据。 加密本身并不能防止干扰和窃听攻击,但会拒绝拦截器可理解的内容。
Encryption Algorithms are of two types:
加密算法有两种类型:
Symmetric-key encryption
对称密钥加密
In this encryption technique, the encryption and decryption key are the same. The key is sometimes referred to as a shared secret because the sender or computer system doing the encryption must share the secret key with anyone authorized to decrypt the message. E.g. Advanced Encryption Standard (AES)
在这种加密技术中,加密和解密密钥相同。 该密钥有时称为共享密钥,因为进行加密的发送方或计算机系统必须与任何有权解密消息的人共享该密钥。 例如,高级加密标准(AES)
Public-key encryption:
公钥加密:
In this encryption technique, the encryption and decryption keys are different. The encryption key is published for anyone to use and to encrypt data, while only the receiving user has access to the decryption key that decrypts the encrypted data. E.g. The Rivest-Shamir-Adleman (RSA)
在这种加密技术中,加密和解密密钥是不同的。 公开发布加密密钥,以供任何人使用和加密数据,而只有接收用户才能访问解密密钥,该解密密钥对加密的数据进行解密。 例如Rivest-Shamir-Adleman(RSA)
Other Examples: Triple DES,, Blowfish, Twofish etc.
其他示例:三重DES,河豚,Twofish等。
解密方式 (Decryption)

Decryption is a process of converting encoded/encrypted data back to its original form. This method is performed by decrypting the text manually or by using keys used to encrypt the original data.
解密是将编码/加密的数据转换回其原始形式的过程。 通过手动解密文本或使用用于加密原始数据的密钥来执行此方法。
散列 (Hashing)
Hashing is a process of converting data through a function, which results in an output of a fixed length. Using a fixed-length output increases security since anyone trying to decrypt the hash won’t be able to tell how long or short the input is simply by looking at the length of the output.
散列是通过函数转换数据的过程,该过程导致输出固定长度的数据。 使用固定长度的输出可提高安全性,因为任何试图解密哈希的人都无法仅通过查看输出的长度来判断输入的长度是多少。
Example:
例:
MD5 (Message Digest 5) Hashing Algorithm
MD5(消息摘要5)哈希算法
It is an algorithm that takes in an input message (plain text) of arbitrary length and produces an output of length 128 bits called message digest (MD).
它是一种算法,它吸收任意长度的输入消息(纯文本),并产生称为消息摘要(MD)的 128位长度的输出。
This algorithm is usually used for authentications.
此算法通常用于身份验证。
Checking integrity of MD
检查MD的完整性
- A 128bit MD is generated by source. 源生成一个128位MD。
- MD is appended to plain text. MD附加在纯文本上。
- The MD is send to the receiver. MD发送到接收器。
- Both the source and receiver MD will be compared. If they match then we can say our data was safely encrypted and was not changes during the process. 源和接收方MD都将被比较。 如果它们匹配,则可以说我们的数据已被安全加密,并且在此过程中没有更改。
MD5 Algorithm:
MD5算法 :
1) Append Padding bits: The input message is padded so that its length equals to 448 mod 512. Padding is always performed even if the message is already 448 mod 512. Padding is performed as follows: a single “1” bit is appended to the message and then “0” bits are appended so that the length in bits of the padded message becomes congruent to 448 mod 512. At least one bit and at most 512 bits are appended.
1)追加填充位:填充输入消息,使其长度等于448 mod512。即使消息已经是448 mod 512,也始终执行填充。填充执行如下:将单个“ 1”位附加到消息,然后附加“ 0”位,以便已填充消息的以位为单位的长度与448 mod 512一致。至少附加一位,最多512位。
2) Append Length: A 64-bit representation of the length of the message is appended to the result of step1. If the length of the message is greater than 2⁶⁴, only the low-order 64 bits will be used. The resulting message (after padding with bits and with b) has a length that is an exact multiple of 512 bits. The input message will have a length that is exact multiple of 16 (32 bit) words.
2)附加长度:消息长度的64位表示形式附加到步骤1的结果中。 如果消息的长度大于2/5,则仅使用低阶64位。 结果消息(在用位和b填充之后)的长度是512位的精确倍数。 输入消息的长度为16(32位)个字的整数倍。
3) Initialize MD buffer: A four-word buffer (A, B, C, D) is used to computer the message digest. Each of A, B, C, D is a 32bit register. These registers are initialized to the following values in hexadecimal, low order bytes first)
3)初始化MD缓冲区:一个四字缓冲区(A,B,C,D)用于计算机处理消息摘要。 A,B,C,D均为32位寄存器。 这些寄存器被初始化为以下值(十六进制,低位字节优先)
word A: 01 23 45 67
word B: 89 ab cd ef
word C: fe dc ba 98
word D: 76 54 32 104) Process message in 16-word blocks: Four functions will be defined such that function takes an input of three 32-bit words and produces and produces a 32-bit word output. F(X,Y,Z) = (X and Y) or (not(X) and Z) [Round1] G(X,Y,Z) = (X and Z) or (Y and not(Z)) [Round2] H(X,Y,Z) = X xor Y xor Z [Round3] I(X,Y,Z) = Y xor (X or not(Z)) [Round4]
4)以16个字的块为单位的过程消息:将定义四个功能,以便该功能接受三个32位字的输入,并产生和产生32位字的输出。 F(X,Y,Z)=(X和Y)或(not(X)和Z)[Round1] G(X,Y,Z)=(X和Z)或(Y and not(Z))[ Round2] H(X,Y,Z)= X或Y x或Z [Round3] I(X,Y,Z)= Y或(X或非(Z))[Round4]
5) Each round has 16 steps of the form:
5)每轮比赛有16个步骤,形式如下:
A ← B + ((A + Function (B, C, D) + x[ ] + T[i]) <<< s)where A, B, C, D refer to the 4 words of the buffer. But used in varying permutations and F (B, C,D) is different nonlinear function in each round (1,2,3,4). i represents different constants 16 constants every round. i will be T[1–16] for 1st round, then T[17–32] for round 2, then T[33–48] for round 3 and finally T[49–64]. X[ ] is a part of the original message. s is the circular left shift s bits.That means for 2nd round we get:
其中A,B,C,D是指缓冲区的4个字。 但是在变化的排列和F(B,C,D)中使用的是每轮(1,2,3,4)中不同的非线性函数。 我代表不同的常数每轮16个常数。 第一轮我将为T [1–16],第二轮将为T [17–32],第三轮将为T [33-48],最后为T [49-64]。 X []是原始消息的一部分。 s是循环左移s位,这意味着在第二轮中我们得到:
B ← C + ((B + Function(C,D,A) + x[ ] + T[17–32]) <<< s)The following figure sums up the MD5 algorithm:
下图总结了MD5算法:

In the above figure gives the overview of the Md5 Algorithm. Here, Message is converted into x[ ] parts for each buffer( A,B,C,D) and is processed with the Functions F, G, H, I and the constants from T[1–64]( which are divided into 16 constants for each buffer). Then we perform “addition modulo” on the output of these buffers and the initial buffer values. And hence, we get our message digest. If the length of the message is > 512 bits i.e. 1 block then, we again perform “addition modulo” on the MD output and initial buffer values for the next block and so on until we process last block.
上图中给出了Md5算法的概述。 在此,对于每个缓冲区(A,B,C,D),消息被转换为x []部分,并使用函数F,G,H,I和来自T [1–64](的常数进行处理)每个缓冲区16个常量)。 然后,我们对这些缓冲区的输出和初始缓冲区值执行“加模”运算。 因此,我们得到了消息摘要。 如果消息的长度> 512位,即1块,则我们再次对MD输出和下一个块的初始缓冲区值执行“加模”运算,直到处理最后一个块。
Other Examples: SHA-1, SHA-2, SHA-3, SHA-256 etc
其他示例:SHA-1,SHA-2,SHA-3,SHA-256等
$echo -n Piyush | md510f95896a13c59b88e4c0e837642fb3c编码vs加密vs哈希 (Encoding vs Encryption vs Hashing)
Encoding: A technique for maintaining data usability and can be reversed by employing the same algorithm that encoded the content, i.e. no key is used.
编码 :一种用于维护数据可用性的技术,可以通过采用对内容进行编码的相同算法来逆转,即不使用任何密钥。
Encryption: A technique for maintaining data confidentiality and requires the use of a key (kept secret) in order to return to plaintext.
加密 :一种用于维护数据机密性的技术,需要使用密钥(保留的机密)才能返回纯文本。
Hashing: A technique for validating the integrity of content by detecting all modifications via obvious changes to the hash output.
哈希 :一种通过对哈希输出进行明显更改来检测所有修改来验证内容完整性的技术。
翻译自: https://medium.com/swlh/quickly-encoding-decoding-encryption-decryption-hashing-318f7b3ea11e
硬解密和软解码的区别







 本文探讨了硬解密和软解码之间的差异,主要聚焦于编码、解码、加密、解密及散列等信息安全领域的概念。内容来源于对原文的翻译,旨在帮助读者理解这两种技术在密码学中的应用。
本文探讨了硬解密和软解码之间的差异,主要聚焦于编码、解码、加密、解密及散列等信息安全领域的概念。内容来源于对原文的翻译,旨在帮助读者理解这两种技术在密码学中的应用。














 145
145

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








