docker 删除映像
With Docker dominating the delivery workflow, it’s become imperative that your container images can be trusted. How can your users be sure that the image content they’re downloading is what you’ve created? How can you verifiably prove that you are, indeed, the creator of an image?
在Docker主导交付工作流程的情况下,必须信任您的容器映像。 用户如何确定他们下载的图像内容就是您创建的内容? 您如何能证明您确实是图像的创造者?
In this article, we’ll explore how trust works in Docker and I’ll show you how to securely sign your Docker images. If you need a quick introduction to the fundamentals of public-key cryptography, check out my previous piece on the topic.
在本文中,我们将探讨信任在Docker中的工作方式,并向您展示如何安全地对Docker映像进行签名。 如果您需要快速介绍公共密钥密码学的基础知识,请查看我之前关于该主题的文章。
Docker注册表和可信实体 (Docker Registry and Trusted Entities)
Although many associate Docker Hub with being the Docker registry, a Docker registry is a standalone concept. In simple terms, a registry is a location where records of information are kept. In the Docker domain, it’s where you upload your Docker images to share them with others.
虽然许多准泊坞枢纽与正在泊坞窗注册表,码头工人,注册表是一个独立的概念。 简单来说,注册表是保存信息记录的位置。 在Docker域中,您可以在其中上传Docker映像以与他人共享。
There are many products available allowing you to run your own private or public Docker registry, with Docker providing a default implementation for free in registry.
有许多可用的产品允许您运行自己的私有或公共Docker注册表,而Docker提供了默认的免费实现在Registry中 。
Currently, Docker Hub features north of 6 million repositories with 130 billion total image pulls. With such staggering numbers and literally anybody being able to create a new repository and start pushing images, trust becomes an issue.
目前,Docker Hub拥有600万个存储库中的北部,具有1300亿个图像提取。 有了如此惊人的数字,实际上任何人都能够创建新的存储库并开始推送图像,信任成为一个问题。
For big, well-known publishers, the issue of trust is taken care of by Docker, Inc., which manually vets selected publishers:
对于大型知名发行商,信任问题由Docker,Inc.处理,该公司手动审查选定的发行商:
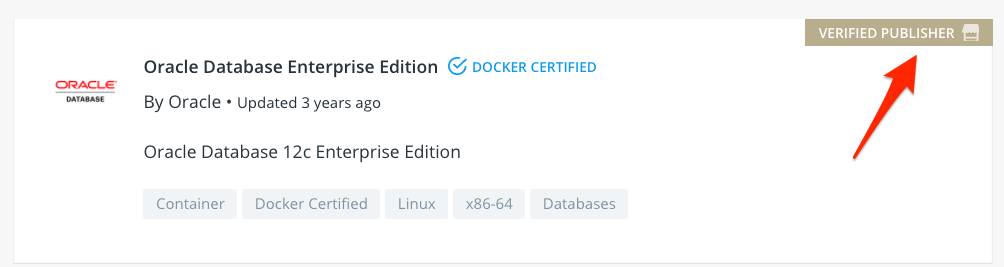
Anyone can apply to become a Verified Publisher. However, the complexity and associated cost behind it might be a deal-breaker for smaller publishers.
任何人都可以申请成为经过验证的发布者 。 但是,对于较小的发行商而言,其复杂性和相关成本可能会破坏交易。
Luckily, we have public-key cryptography and Docker Hub supports digital signatures in uploaded images.
幸运的是,我们拥有公钥加密技术,并且Docker Hub支持上传的图像中的数字签名。
Let’s see how to become our own Verified Publisher.
让我们看看如何成为我们自己的经过验证的发布者。
Docker内容信任(DCT) (Docker Content Trust (DCT))
DCT allows publishers of images to use digital signatures, effectively allowing users pulling their images to verify:
DCT允许图像的发布者使用数字签名,从而有效地允许用户提取其图像以验证:
- That the content of the image has not been tampered with. 图像的内容未被篡改。
- The identity of the publisher. 发布者的身份。
Because DCT is based on public-key cryptography, anyone can create a free public/private keypair and start pushing signed images. Publishers need to sign every single individual image before being uploaded and signatures refer to specific tags of their images. This is an important point to keep in mind. The fact that tag 1.0.0 was signed doesn’t necessarily mean that tag 1.0.1 will also be signed. It also means that a signed 1.0.0 tag can be overwritten by an unsigned 1.0.0 tag.
因为DCT基于公共密钥加密,所以任何人都可以创建一个免费的公共/私有密钥对并开始推送签名的图像。 发布者需要在上载每个单独的图像之前对其进行签名,并且签名引用其图像的特定标签。 这是要记住的重要一点。 标签1.0.0被签名的事实并不一定意味着标签1.0.1也将被签名。 这也意味着一个已签名的1.0.0标签可以被一个未签名的1.0.0标签覆盖。
To be on the safe side, make sure you verify all your images on the tag level every single time you pull them.
为了安全起见,请确保每次拉动图像时都在标签级别上验证所有图像。
It’s worth noting here that DCT is an additional feature for your images and users who don’t know how to make use of it can continue pulling your images as before.
在这里值得注意的是,DCT是图像的附加功能,不知道如何使用它的用户可以像以前一样继续提取图像。
So, ready to sign our first image? Let’s do that next.
那么,准备签署我们的第一张图片了吗? 让我们接下来做。
签署Docker映像 (Signing Docker Images)
In this section, we’ll see:
在本节中,我们将看到:
- How to generate signing keys. 如何生成签名密钥。
- How to bind a Docker repository with a public key. 如何使用公共密钥绑定Docker存储库。
- How to sign an image. 如何签名图像。
- How to verify that an image is signed. 如何验证图像已签名。
先决条件 (Prerequisites)
To sign an image, we obviously need an image to start with. Go ahead and pull the hello-world example from Docker Hub:
要签名图像,我们显然需要一个图像作为开始。 继续并从Docker Hub中获取hello-world示例:
docker pull hello-worldNext, you need to tag this image so that you can push it into your own repository. Adjust the following command to match your username on Docker Hub and execute:
接下来,您需要标记该图像,以便可以将其推送到您自己的存储库中。 调整以下命令以匹配您在Docker Hub上的用户名并执行:
docker tag hello-world nassos/signatures:1You now have your own image of hello-world and we’re ready to sign it.
您现在拥有了自己的hello-world ,我们已经准备好对其进行签名。
生成签名密钥 (Generating signing keys)
To generate a digital signature, you need to create a public/private keypair. You can use Docker CLI to create one (you can replace dev1 with your own name if you wish):
要生成数字签名,您需要创建一个公共/私有密钥对。 您可以使用Docker CLI创建一个(如果需要,可以使用自己的名称替换dev1 ):
docker trust key generate dev1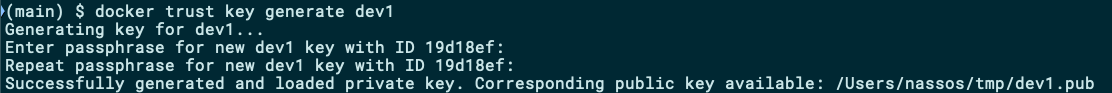
The public key will be created on the directory where you executed this command from and the private key will be placed under ~/.docker/private.
公钥将在执行此命令的目录上创建,私钥将放置在~/.docker/private 。
允许公共密钥对图像签名 (Allowing the public key to sign images)
The whole concept of content trust in Docker works in tandem with Docker Notary:
Docker中内容信任的整个概念与Docker Notary协同工作:
“Notary is a tool for publishing and managing trusted collections of content. Publishers can digitally sign collections and consumers can verify integrity and origin of content. This ability is built on a straightforward key management and signing interface to create signed collections and configure trusted publishers.”
公证人是用于发布和管理可信内容集合的工具。 发布者可以对馆藏进行数字签名,而消费者可以验证内容的完整性和来源。 此功能建立在简单的密钥管理和签名界面上,可以创建签名的集合并配置受信任的发布者。”
Docker Notary is bound to a Docker registry to provide its services. For Docker Hub, there is already a Notary server attached and Docker CLI streamlines the process of interacting with it, so you don’t really need to know it exists.
Docker Notary绑定到Docker注册表以提供其服务。 对于Docker Hub,已经连接了一个Notary服务器,并且Docker CLI简化了与之交互的过程,因此您实际上不需要知道它的存在。
To begin signing images, you should add your public key to the underlying Notary server. You can do so by executing the following command:
要开始对图像进行签名,您应该将公共密钥添加到基础公证服务器。 您可以通过执行以下命令来这样做:
docker trust signer add --key dev1.pub dev1 nassos/signatures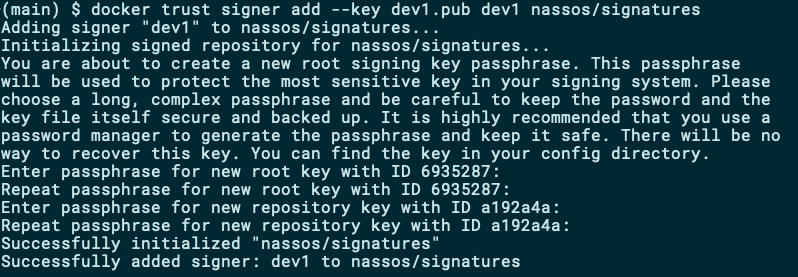
The public key of user dev1 is only allowed to sign images for the repository you have specified, namely nassos/signatures. If you need this user to be able to sign images on a different repository, you need to repeat the command above with the new repository as a target.
用户dev1公钥仅允许为您指定的存储库(即nassos/signatures 。 如果您需要该用户能够在其他存储库上签名图像,则需要以新存储库为目标重复上述命令。
签名图像 (Signing the image)
With your image and keypair in place and your public key added to the repository, you can now proceed to sign your first image:
将映像和密钥对放置到位,并将公钥添加到存储库后,您现在就可以对第一张映像进行签名了:
docker trust sign nassos/signatures:1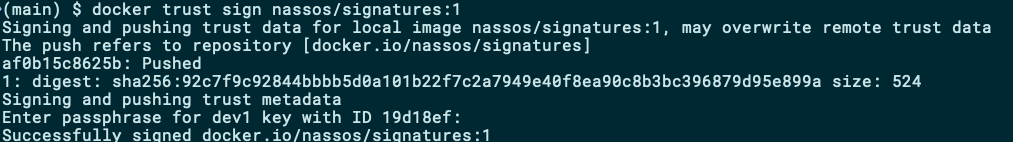
The command above signed the image and automatically pushed it to Docker Hub.
上面的命令对映像签名并自动将其推送到Docker Hub。
检查签名图像 (Inspecting signed images)
You can query Docker Hub (in fact, the Notary behind Docker registry) about the signatures and signatories status of a repository with:
您可以使用以下命令查询存储库的签名和签名者状态的Docker Hub(实际上是Docker注册表背后的公证人):
docker trust inspect --pretty nassos/signatures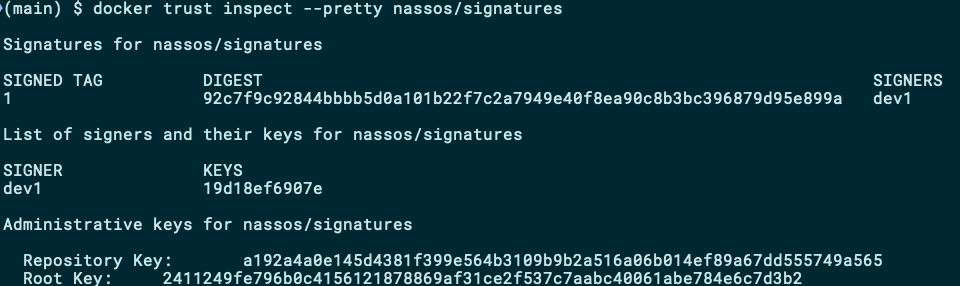
This command shows which tags on this repository are signed as well as the list of people with signatures attached to this repository (i.e. people who can sign images).
此命令显示此存储库上的哪些标签已签名,以及带有附加到此存储库的签名的人员(即可以签名图像的人员)列表。
使用签名图像 (Working With Signed Images)
The next step after having your images signed is to instruct Docker to work with signed images. As mentioned at the beginning of this article, signatures are an additional property of an image and you can completely ignore them if you wish. For example, you can still try to pull the signed image nassos/signatures:1 created above with a docker pull.
对映像进行签名后的下一步是指示Docker处理签名的映像。 如本文开头所述,签名是图像的附加属性,如果需要,您可以完全忽略它们。 例如,您仍然可以尝试使用nassos/signatures:1 docker pull上面创建的签名图像nassos/signatures:1 。
However, if you want to work only with signed images, you can instruct your Docker CLI to only fetch signed images with the DOCKER_CONTENT_TRUST environmental variable:
但是,如果您只想使用签名的图像,则可以指示Docker CLI仅使用DOCKER_CONTENT_TRUST环境变量来获取签名的图像:
DOCKER_CONTENT_TRUST=1 docker pull nassos/signatures:1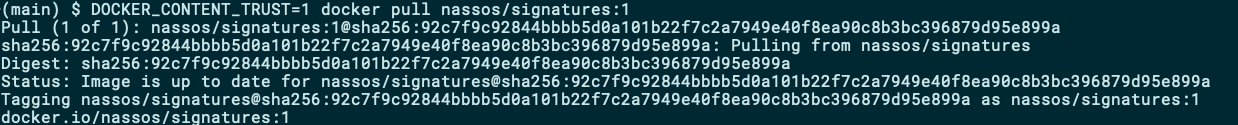
The Docker CLI pulls the image and verifies the signature before persisting it into your local storage.
Docker CLI将映像提取并验证签名,然后再将其持久保存到本地存储中。
Trying to pull an image with no signature attached results in an error:
尝试拉没有签名的图像会导致错误:
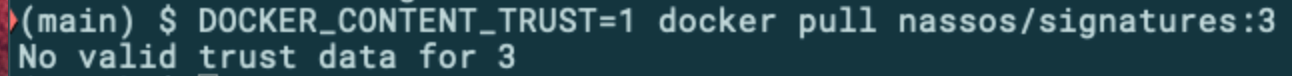
If you are working with the Enterprise edition of Docker, you can also configure the underlying Docker Engine to only work with signed images by modifying /etc/docker/daemon.json:
如果您使用的是企业版Docker,则还可以通过修改/etc/docker/daemon.json将底层Docker Engine配置为仅使用签名映像:
{
"content-trust": {
"mode": "enforced"
}
}与合作者一起工作 (Working With Collaborators)
If your Docker repository happens to be one that you share with others (e.g. a company repository), Docker Content Trust allows you to let multiple people being push signed images.
如果您的Docker存储库恰好是您与他人共享的存储库(例如公司存储库),则Docker Content Trust允许您让多个人被推送签名图像。
First, your collaborator needs to create a keypair:
首先,您的协作者需要创建一个密钥对:
docker trust key generate dev2The generated dev2.pub public key needs to be forwarded to you in order to be added to the list of signatories for the repository:
需要将生成的dev2.pub公钥转发给您,以便将其添加到存储库的签名者列表中:
docker trust signer add --key dev2.pub dev2 nassos/signaturesYour collaborator dev2 can now push images on the repository as you did before. You can inspect the repository once more, and this time you will see both yourself as well as the newly added collaborator:
现在,您的协作者dev2可以像以前一样将图像推dev2存储库中。 您可以再次检查存储库,这次您将同时看到自己和新添加的协作者:
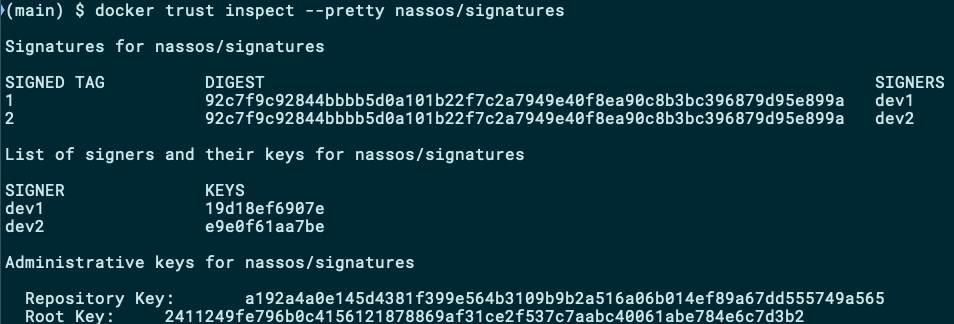
结论 (Conclusion)
In the era of Docker domination over the delivery workflow, it is imperative that you can trust the source of your Docker images. Docker provides a comprehensive mechanism for signing, verifying, and working with multiple collaborators under a repository, Docker Content Trust (DCT). You can leverage DCT so that users of your images are certain of the content of the image they’re about to use.
在Docker统治交付流程的时代,必须信任Docker映像的来源。 Docker提供了一种全面的机制来对Docker Content Trust(DCT)存储库中的多个协作者进行签名,验证和使用。 您可以利用DCT,以便图像用户确定他们将要使用的图像内容。
As always when working with public key infrastructure, make sure you properly back up your private keys.
与使用公钥基础结构时一样,请确保始终正确备份私钥。
Thank you for reading this article. I hope to see you in the next one.
感谢您阅读本文。 我希望在下一个见到你。
翻译自: https://medium.com/better-programming/docker-content-trust-security-digital-signatures-eeae9348140d
docker 删除映像




















 2171
2171











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








