java ssl 通讯
In the age of the Internet, everything is available at our fingertips where we are just one click away to get any information from anywhere in the world. This includes our sensitive data as well. This sensitive data needs to be secured so that it does not get exposed to hackers. When we surf the internet or search for any information, it gets transmitted to our browser from a server. The browser to server communication aka client-server communication happens over HTTP protocol. HTTP protocol by itself cannot protect our sensitive data. That’s where SSL comes to rescue.
在Internet时代,一触即发,一切都触手可及,我们可以一键式获取来自世界任何地方的任何信息。 这也包括我们的敏感数据。 需要保护此敏感数据,以使其不会暴露给黑客。 当我们上网或搜索任何信息时,它会从服务器传输到我们的浏览器。 浏览器与服务器之间的通信(也称为客户端与服务器之间的通信)通过HTTP协议进行。 HTTP协议本身不能保护我们的敏感数据。 这就是SSL拯救的地方。
什么是SSL? (What is SSL?)
SSL stands for Secure Socket Layer. It was developed by Netscape to ensure that private data remains intact when it reaches the browser.
SSL代表安全套接字层。 它是由Netscape开发的,目的是确保私有数据在到达浏览器时保持完整。
SSL is an encryption based protocol which establishes a secure and trusted connection between browser and the server over which sensitive data can be transmitted.
SSL是一种基于加密的协议,可在浏览器与服务器之间建立安全且受信任的连接,通过该连接可以传输敏感数据 。
Once the connection is established, the data can be transmitted securely over the HTTP protocol. The HTTP protocol is now secured and becomes HTTPS protocol, which is nothing but HTTP-Secure or HTTP over SSL. To be able to establish an SSL connection, the server requires an SSL certificate.
一旦建立连接,就可以通过HTTP协议安全地传输数据。 现在,HTTP协议已受保护,并成为HTTPS协议,它不过是HTTP-Secure或SSL上的HTTP。 为了能够建立SSL连接,服务器需要SSL证书 。
SSL证书 (SSL Certificate)
SSL certificate is an electronic document that contains a public key used to encrypt data. It also contains information about the web site which is used to prove the ownership of the public key. In simple words, it is a document that binds the encryption key with organization details.
SSL证书是一种电子文档,其中包含用于加密数据的公共密钥。 它还包含有关该网站的信息,用于证明公钥的所有权。 简而言之,它是将加密密钥与组织详细信息绑定在一起的文档。
SSL certificate helps in establishing a secure connection between browser and server. It can be verified by seeing the green padlock 🔒which appears on the address bar of the browser. We can view the certificate by clicking the padlock.
SSL证书有助于在浏览器和服务器之间建立安全连接。 可以通过查看浏览器地址栏上的绿色挂锁verified进行验证。 我们可以通过单击挂锁来查看证书。

These certificates are x509 standard certificates, and the encoding of these certificates is done in two formats, DER (Distinguished Encoding Rules) and PEM (Privacy Enhanced Mail). In the DER format, the certificate is stored in binary form, whereas in PEM format, the certificate is stored in a human-readable text form.
这些证书是x509标准证书,这些证书的编码以两种格式完成: DER(专有编码规则)和PEM(隐私增强邮件)。 在DER格式中,证书以二进制形式存储,而在PEM格式中,证书以人类可读的文本形式存储。
A typical PEM certificate looks like this:
典型的PEM证书如下所示:
-----BEGIN CERTIFICATE-----
MIICEjCCAXsCAg36MA0GCSqGSIb3DQEBBQUAMIGbMQswCQYDVQQGEwJKUDEOMAwG
A1UECBMFVG9reW8xEDAOBgNVBAcTB0NodW8ta3UxETAPBgNVBAoTCEZyYW5rNERE
MRgwFgYDVQQLEw9XZWJDZXJ0IFN1cHBvcnQxGDAWBgNVBAMTD0ZyYW5rNEREIFdl
YiBDQTEjMCEGCSqGSIb3DQEJARYUc3VwcG9ydEBmcmFuazRkZC5jb20wHhcNMTIw
ODIyMDUyNjU0WhcNMTcwODIxMDUyNjU0WjBKMQswCQYDVQQGEwJKUDEOMAwGA1UE
CAwFVG9reW8xETAPBgNVBAoMCEZyYW5rNEREMRgwFgYDVQQDDA93d3cuZXhhbXBs
ZS5jb20wXDANBgkqhkiG9w0BAQEFAANLADBIAkEAm/xmkHmEQrurE/0re/jeFRLl
8ZPjBop7uLHhnia7lQG/5zDtZIUC3RVpqDSwBuw/NTweGyuP+o8AG98HxqxTBwID
AQABMA0GCSqGSIb3DQEBBQUAA4GBABS2TLuBeTPmcaTaUW/LCB2NYOy8GMdzR1mx
8iBIu2H6/E2tiY3RIevV2OW61qY2/XRQg7YPxx3ffeUugX9F4J/iPnnu1zAxxyBy
2VguKv4SWjRFoRkIfIlHX0qVviMhSlNy2ioFLy7JcPZb+v3ftDGywUqcBiVDoea0
Hn+GmxZA
-----END CERTIFICATE-----Let’s dive in and understand how this SSL communication happens.
让我们深入了解SSL通信是如何发生的。
SSL通讯 (SSL Communication)
The process of SSL communication is also known as an SSL handshake. It involves several steps to establish a secure connection.
SSL通信的过程也称为SSL握手。 它涉及建立安全连接的几个步骤。
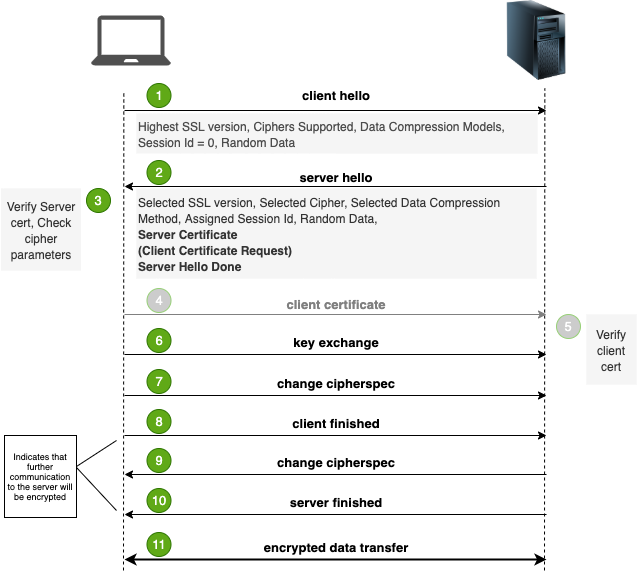
Let’s go through these steps in detail 📖
让我们详细了解这些步骤📖
第1步-客户您好 (Step 1 — Client Hello)
The client (browser) initiates the communication by sending the following details to the server:
客户端(浏览器)通过将以下详细信息发送到服务器来启动通信:
- Highest SSL version supported 支持的最高SSL版本
- Client Random (for generating encryption key) 客户端随机(用于生成加密密钥)
- Session-Id (blank in case of new session) 会话ID(在新会话的情况下为空白)
- Compression Method 压缩方式
- Cipher Suites (most preferred at top of the list) 密码套件(在列表顶部是最喜欢的)
第2步-服务器Hello (Step 2 — Server Hello)
The server replies to the client with the following information:
服务器使用以下信息答复客户端:
- SSL version selected by the server from the list provided by the client. 服务器从客户端提供的列表中选择的SSL版本。
- Server Random 服务器随机
- Session-Id 会话ID
- Compression Method (selected from client’s list) 压缩方式(从客户列表中选择)
- Cipher Suites (selected from client’s list) 密码套件(从客户列表中选择)
- Server Certificate 服务器证书
第3步-客户证书 (Step 3 — Client Certificate)
This step is optional and is used in 2-way SSL. In this step the client sends its SSL certificate to the server if the server has requested for it in step 2. In this way, the server authenticates the client.
此步骤是可选步骤,用于2向SSL。 在此步骤中,如果服务器在步骤2中请求了它,则客户端会将其SSL证书发送到服务器。这样,服务器将对客户端进行身份验证。
第4步-SSL验证 (Step 4 — SSL verification)
Until now the server hello is done. Now the client verifies the SSL certificate provided by the server by reading the CA (Certificate Authority) from the certificate and by loading the public key of that CA from the browser’s trust store and by verifying the signature. If the certificate is not valid, the browser produces a warning, otherwise, the browser shows a green padlock at the address bar showing the authenticity of the website.
到目前为止,服务器问候已经完成。 现在,客户端通过从证书中读取CA(证书颁发机构),并从浏览器的信任库中加载该CA的公钥,并验证签名来验证服务器提供的SSL证书。 如果证书无效,则浏览器会发出警告,否则,浏览器在地址栏上显示绿色的挂锁,以显示网站的真实性。
第5步-密钥交换 (Step 5 — Key Exchange)
This step aims at achieving a symmetric key which will be used for further communication. There are various algorithms for doing it. RSA & Diffie Hellman are two of those algorithms. The RSA algorithm uses the server’s public key for confidentiality while exchanging secrets. While in the Diffie Hellman algorithm, no secret key is exchanged and the server’s public key is not used. Here, the secret key of the client and the server changes for every session.
该步骤旨在实现将用于进一步通信的对称密钥。 有多种算法可以做到这一点。 RSA和Diffie Hellman是其中两个算法。 RSA算法在交换机密时使用服务器的公钥来确保机密性。 在Diffie Hellman算法中,不会交换任何秘密密钥,也不会使用服务器的公共密钥。 在此,客户端和服务器的密钥对于每个会话都会更改。
第6步-更改密码规范 (Step 6 — Change Cipherspec)
In this step, the client and the server have the key and now onwards the communication happens over an encrypted channel. At this step, the client and server finalizes the cipher spec. This is the last chance to change the cipher spec. After this the key exchange phase finishes.
在此步骤中,客户端和服务器具有密钥,现在开始通过加密通道进行通信。 在此步骤,客户端和服务器最终确定密码规范。 这是更改密码规范的最后机会。 此后,密钥交换阶段结束。
步骤7 —加密的数据传输 (Step 7 — Encrypted Data Transfer)
At this step, the data which is going to be transmitted, goes through a few steps:
在此步骤中,将要传输的数据经过几个步骤:
- The data is divided into small fragments. 数据分为小片段。
- Then, these fragments are compressed. 然后,将这些片段压缩。
- Then, the MAC is calculated and appended to the compressed fragment. 然后,计算MAC并将其附加到压缩的片段中。
- Then, the symmetric encryption happens. 然后,进行对称加密。
- Then, the SSL header is appended at the beginning of the encrypted fragment. This header tells about the SSL record type. For ex., Handshake type, data type, etc. 然后,将SSL标头附加在加密片段的开头。 此标头说明SSL记录类型。 例如,握手类型,数据类型等。
最后 (Finally)
After all steps, the browser now has the secure and encrypted connection with the server and sensitive data can be transmitted over. This entire process is transparent and happens within a fraction of seconds.
完成所有步骤之后,浏览器现在与服务器建立了安全且加密的连接,并且可以传输敏感数据。 整个过程是透明的,并且在几秒钟内即可完成。
结论 (Conclusion)
Well thanks for reaching this far… 👍 I hope this article gave a good grasp of SSL communication and the steps involved in the SSL handshake. Please let me know what you think about this article.
好的,谢谢您的学习……👍我希望本文能够很好地理解SSL通信以及SSL握手中涉及的步骤。 请让我知道您对本文的看法。
翻译自: https://medium.com/swlh/demystifying-ssl-communication-5a8ea2aebcb8
java ssl 通讯





















 360
360

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








